Resource Center
Filter by
All Resources | Kojensi Resources | NC Protect Resources

Data Sheet: NC Protect and Microsoft Purview Information Protection (MIP) Integration
NC Protect leverages key Microsoft Purview Information Protection (MPIP) extensibility capabilities to provide fine-grained, data-centric security for collaboration in Microsoft 365 applications. By combining MPIP sensitivity labels with NC Protect’s dynamic attribute-based access control (ABAC) and protection policies customers will benefit from expanded protection and control over information access, collaboration and sharing. Learn more about the integration.

Data Sheet: NC Protect for File Shares
The numbers tell the story, 90 percent of data generated today is unstructured (customer purchase history, call center logs, email, spreadsheets, documents, web content, blogs, wikis, etc.). And information velocity is not slowing down with quintillions of bytes of data being created every day.

Data Sheet: NC Protect for Nutanix
Organizations rely on file storage platforms like Nutanix Files to store and collaborate on unstructured content. And that content is growing quickly.

NC Protect Technical Specifications
The following technical requirements represent the minimum recommended configuration for installing NC Protect version 8.5. archTIS recognizes that each deployment is different and can advise on how your specific environment should be configured to ensure optimal performance.

Data Sheet: NC Protect Overview
With modern collaboration apps, users can access data from an alarming variety of locations. Between Azure, Office 365 and other cloud platforms, businesses are adopting new technologies faster than ever and data loss prevention methodology needs to keep up.

White Paper: Top 10 SharePoint Security and Compliance Risks
This whitepaper describes 10 risks that are common in SharePoint environments. These risks are ones that we at archTIS have frequently seen in dealing with hundreds of SharePoint users over the past few years, and they are risks that can have serious consequences for organisation if left unmanaged.
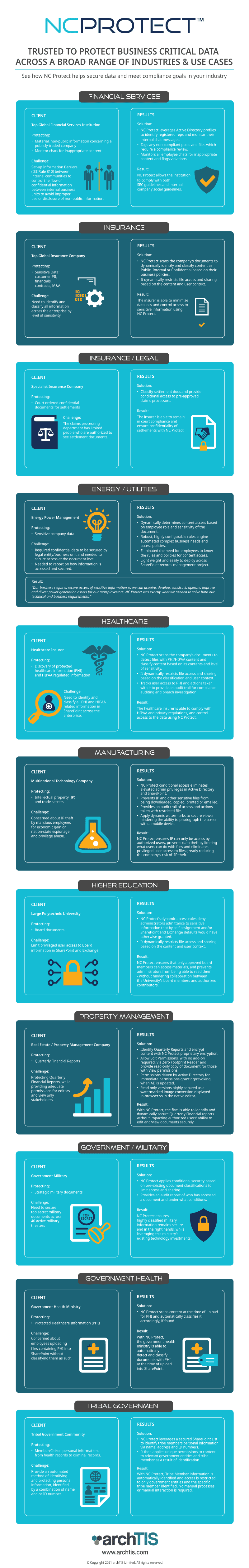
NC Protect Customer Success Stories by Industry
See how NC Protect helps customers in every industry secure data and meet compliance.

Case Study: NC Protect Trims Information Sharing Risk in SharePoint for German Insurer BGW
Learn how NC Protect enabled BGW to secure SharePoint documents in accordance with their security requirements to mitigate risk and protect documents by limiting users to secure read-only access and eliminating their ability to use certain SharePoint functionality.

Case Study: Cogentrix Secures Access to Sensitive Information in SharePoint with NC Protect
Learn why this energy utility says NC Protect product was a perfect fit for securing highly confidential data in SharePoint.

Infographic: 5 Ways Remote Work Fuels Data Loss
Get the facts about this alarming trend and the steps your organization can take to address data loss that has been amplified by working from home.
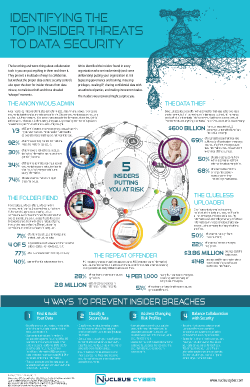
Infographic: Identifying The Top Insider Threats to Data Security
Every organization has them. Discover the insiders inadvertently (and deliberately) putting you at risk bypassing governance and training, misusing privileges, stealing IP, sharing confidential data with unauthorized parties, and simply making innocent mistakes.

2021 State of Remote Work Security Report
The 2021 State of Remote Work Security Report reveals additional insights into the status of organizations’ efforts to secure the new workforce, key challenges and unique security threats, technology gaps and investment priorities.

2019 Insider Threat Report
The 2019 Insider Threat Report from Cybersecurity Insiders reveals the latest trends and challenges facing organizations, how IT and security professionals are dealing with risky insiders and preparing to better protect their critical data and IT infrastructure.
Solution Brief: NC Protect – Adding Value to Microsoft Investments
Discover why customers rely on NC Protect to enhance and add additional capabilities to their Office 365 apps to safeguard against data loss, misuse, and accidental sharing.

White Paper: Dynamic Data Loss Prevention in SharePoint
Enable collaboration without compromising security. Learn how to apply user and file context to drive dynamic, attribute-based data protection to prevent data loss, misuse and accidental sharing.

White Paper: Secure Collaboration – The Impossible Paradox
Despite best efforts, the security solutions in use today are only partially effective at protecting sensitive data. A new approach is clearly needed. Explore a more effective data-centric approach to tackling data security.

White Paper: 5 Data Security Challenges to Modern Collaboration
Get our tips for balancing security and collaboration needs as cybersecurity threats have increased and data protection regulations have evolved.

Video: NC Protect for Microsoft 365
See how NC Protect’s advanced information protection capabilities prevent data breaches, unauthorized file access and accidental sharing in M365 apps, Windows File Shares and more — simpler, faster and cheaper.
