What is the Attribute Based Access Control (ABAC) model?
Learn about ABAC, the security model underpinning archTIS’ products and services, and how it can be applied to your data security needs.
The secure collaboration challenge
Globally, digital transformation has created new ways to work smarter and faster — anytime, anywhere. However, collaborating on and sharing sensitive or classified information introduces new information security risks and problems that must be solved.
A new threat vector has emerged with digital collaboration – insiders. Globally, careless or negligent employees and contractors account for 62% of insider security incidents, and malicious insiders 23%. Data security that addresses insider threats and external threats is paramount for enterprises, government, defence industry, research, intelligence and supply chain collaboration.
Traditional security tools are focused on protecting systems against external threats. To address insider threats a new security model is needed that focuses on directly protecting what’s at stake – your data. Attribute Based Access Control provides a solution.
What is Attribute Based Access Control?
Attribute Based Access Control (ABAC) is a data-centric security model that uses dynamic policies to control who accesses information and under what conditions.
Using an ABAC-enabled solution, policies can be based on any combination of user (i.e. position, nationality), content (via discovery process rules) and environment (access point to information) attributes. This allows governance and security teams to create policies that dynamically adjust access, usage and sharing rights based on real-time comparison of user context and file content to enforce regulations and policies.
ABAC policies ensure only the right people can access the right information at the right time.
The complete portfolio of archTIS solutions leverage a data-centric, attribute-based access control (ABAC) methodology to ensure the highest levels of data protection.
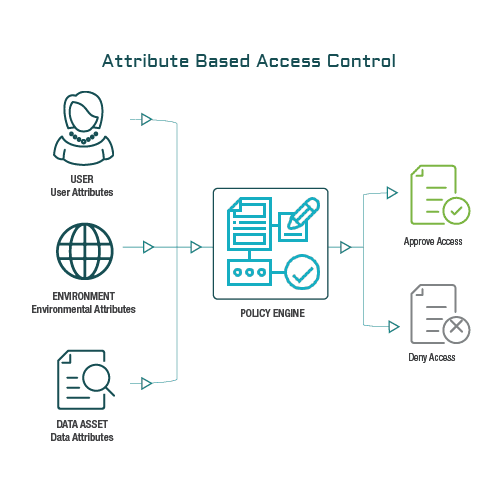
How Does ABAC Work?
The ABAC model uses attributes including document, user and environment values. A dictionary of attributes is created to build precise access control and data protection policies. Here is a simplified example of the ABAC security model applied to document sharing and collaboration.
The ABAC policy could read,
If User A has geography = Australia, Clearance = NV1, and Department = 1, access is granted,
as shown in the access request scenario below.
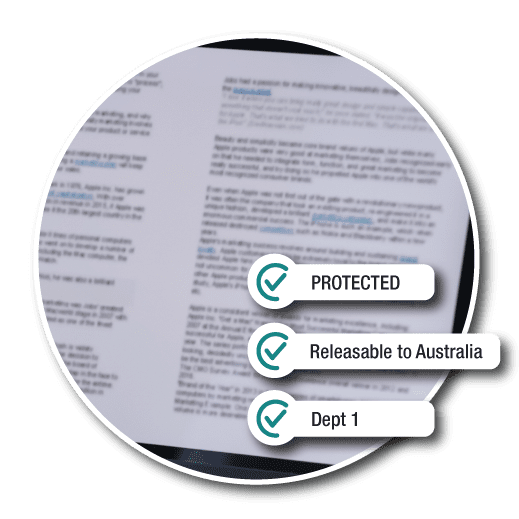
The attributes of geography and sensitivity level are applied to the document.
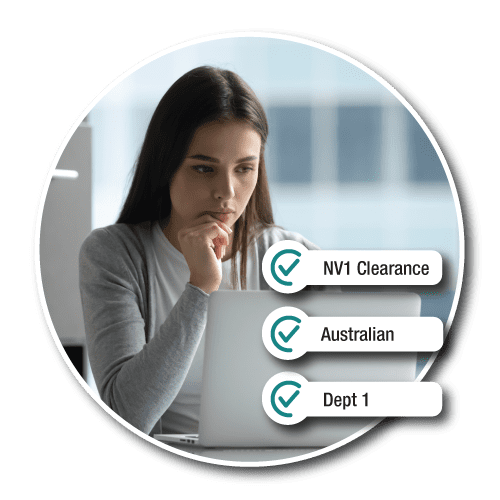
User attributes are defined based on department and clearance levels assigned to the requestor.

If all conditions within the ABAC policy are met, access to the document is approved.
Video: How ABAC Works
What is an attribute?
Attributes are the characteristics or values of a component. With ABAC, security is built around the combination of different user, environmental and resource attributes.
Here are some examples:
USER
- Name
- Nationality
- Security Clearance
- Organisation
- Group
LOCATION
- Country
- State
- Address
DEVICE
- Name
-
MAC Address
-
Credentials
-
Classification
NETWORK
- Name
- Credential
- Classification
DATA
- Document Type
- Sensitivity Level
- Data Classification
- Metadata
APPLICATIONS OF ATTRIBUTE-BASED ACCESS CONTROL IN GOVERNMENT, DEFENCE AND INDUSTRY
The ABAC methodology ensures secure information access and sharing across government and industry. Explore the applications below.
Government
ABAC helps governments to facilitate highly secure and productive interagency and multinational collaboration.
Defence
ABAC facilitates the granular level of control needed to protect the TOP SECRET and critical Defence work.
Financial Services
ABAC enables financial services organisations to better protect client information and ensure compliance at all levels.
Critical Infrastructure
ABAC helps facilitate secure collaboration for big and complex projects, for increased productivity.
Government Industry
Defense Industry
ABAC helps Defence protect the nation’s most sensitive and classified information, across the supply chain.
Healthcare & Life Sciences
ABAC helps securely share sensitive information and intellectual property in the development of critical health and response services.
Legal
ABAC enforces a greater level of protection over confidential documents and data, to uphold important justice processes.
Explore archTIS’ ABAC Powered Information Security Solutions

DYNAMIC ACCESS AND DATA PROTECTION FOR MICROSOFT 365 APPS, NUTANIX FILES AND DROPBOX
NC Protect provides advanced data-centric security collaboration applications including Microsoft 365, SharePoint Online and on-premises, OneDrive, Teams, Yammer and Exchange emails, as well as Nutanix Files, Dropbox and Windows File Shares. It discovers, classifies and secures unstructured data including files, messages and chat content. Access and security are dynamically adjusted based on real-time comparison of user context and file content to make sure that users access, use and share files according to your business regulations and policies.

COMPARTMENTALISED CLASSIFIED INFORMATION COLLABORATION AND SHARING platform
For Defence, Defence Industry, and Intelligence who need the ability to share sensitive and classified information internally and with partners and clients, Kojensi is a proven and accredited platform for classified information collaboration and sharing that allows productivity while managing the compliance and security of information. Unlike spending millions to build and manage your own information sharing system, Kojensi enables secure, compartmentalized collaboration out of the box for less time and money.
