NC Encrypt
Data Encryption, Key Management & BYOK for Microsoft 365, SharePoint Server & File Shares
Data encryption and key management are a core part of any organization’s security and compliance toolbox for protecting Microsoft 365 (M365) and SharePoint data.
Out-of-the-box NC Protect’s policy-based encryption provides the ability to secure documents automatically based on user attributes, context, and file sensitivity to protect your data no matter where it is stored or travels.
Pairing NC Protect with the NC Encrypt add-on module offers dynamic encryption capabilities and Bring Your Own Key (BYOK) for M365. It’s the perfect solution for organizations that prefer to maintain control of their encryption keys in the Cloud to maintain data sovereignty.
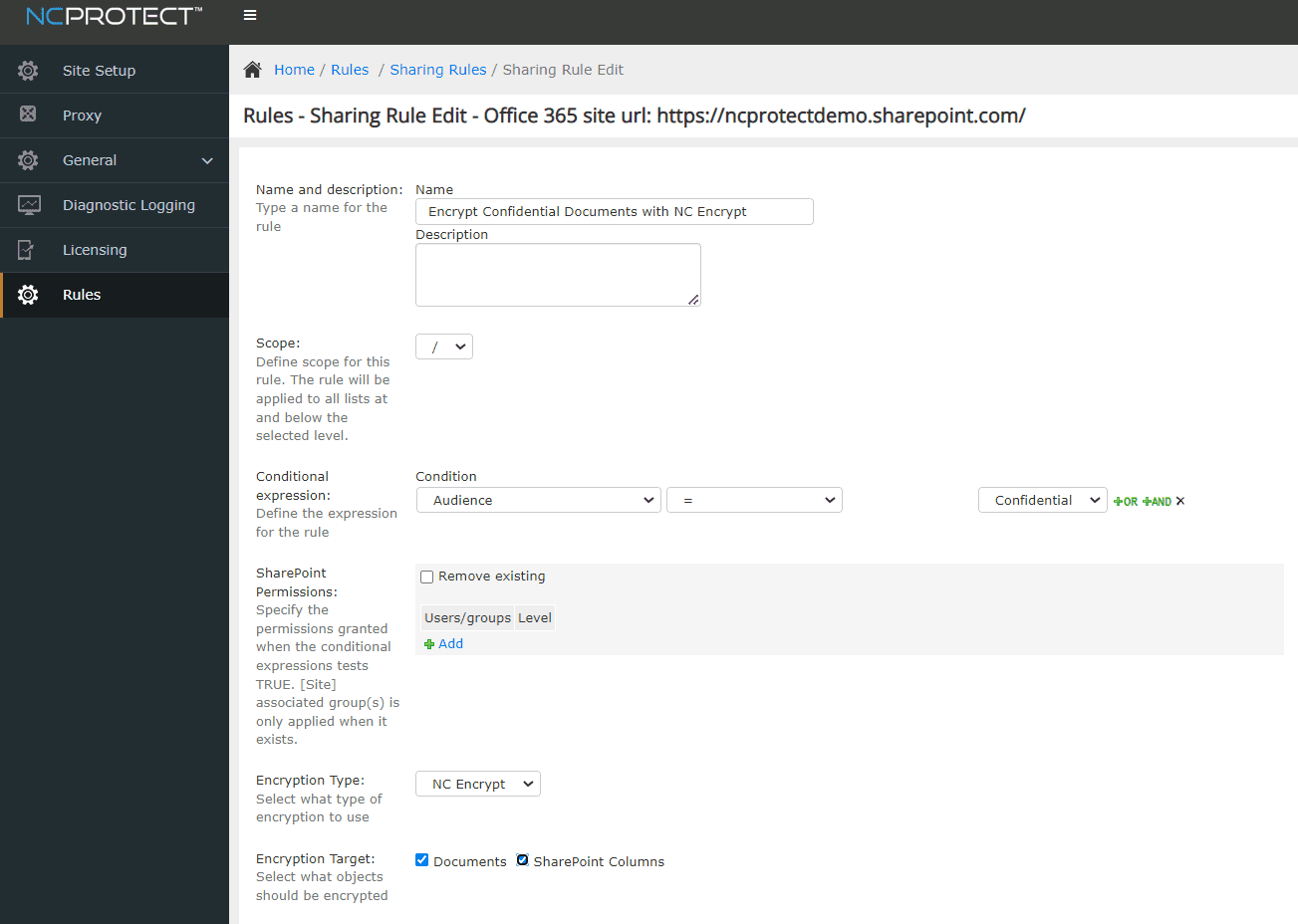
Easily build dynamic encryption into data protection policies in NC Protect’s central policy manager
Dynamic Encryption & Key Management for
Microsoft 365, SharePoint Server & File Shares
Flexible Encryption & Key Management Options
Improving your organization’s security posture should be simple, flexible and tailored to your security philosophy and needs.
NC Encrypt provides encryption capabilities for organizations that:
- Do not have RMS.
- Are expanding existing bring your own key (BYOK) encryption strategies.
- Require independent encryption key management for Microsoft applications and SharePoint on-premises environments.
- Want to add dynamic and robust encryption and real-time protection of sensitive data leveraging existing Microsoft Purview Information Protection and RMS controls.
Use NC Encrypt’s dynamically created keys or supply and manage your own keys. NC Encrypt has the option to integrate with third-party key management platforms using Thales CipherTrust Manager, which provides connectivity to VSMs and HSMs. Linking CipherTrust Manager to NC Encrypt provides an innovative solution that allows you to manage your encryption key processes independently in CipherTrust Manager while managing your dynamic encryption and access control policies in NC Protect.
NC Encrypt’s agentless design means there’s no administrative overhead. There are no encryption keys or passwords that need to be shared with end users or endpoints. No software to be installed and maintained or endpoint policies to update.
Key Benefits
- Enables compliance with GDPR, HIPAA and other privacy regulations with encryption and dynamic access control capabilities.
- Maintains control of your encryption keys in the Cloud.
- Remote key management keeps keys separated from the cloud.
- Adds dynamic at rest and in motion encryption capabilities.
- Encrypt files and SharePoint list column values dynamically based on defined policies.
- Quick and easy to set up with system generated or your own encryption keys.
- Offers centrally controlled and granular security policies to alleviate dependency on user behavior.
- Uses secure AES-256 bit encryption that is FIPS 140-2 compatible.
- Supports BYOK with connectors to third party key management platforms.
- Connect directly to existing HSM/VSMs via integration with Thales CipherTrust Manager.
- Supports investigation of security breaches with real-time activity logging and reporting.
- Agentless design enables easy deployment and management.
- Available for Microsoft 365, SharePoint Server and File Shares.
Key Capabilities
Encrypt Files & SharePoint Columns
Dynamic policy-driven encryption of individual files in supported applications. Encrypt SharePoint list column values to restrict visibility.

Strong Encryption
Uses secure AES-256 bit encryption that is
FIPS 140-2 compatible.
Remote Key Management
Exclusive, customer-only control of encryption keys for M365 (Microsoft controlled environment). Enables keys to be stored in specific geographical locations for data sovereignty and compliance.

Centrally Manage Policies
Centrally manage encryption and access policies across the Microsoft suite from the NC Protect Administration Portal.

Bring Your Own Key (BYOK) Support
Supply and manage your own keys or use NC Encrypt’s dynamically created keys. Provides connectors for third party key management platforms.
Reporting & Auditing
Real-time activity logging and reporting tracks permitted and denied access requests, and actions taken with files accessed.
Supports Encryption & Key Management Across These Applications

SharePoint Online &
On-Premises

Office
File Shares
Resources
Video: NC Encrypt Overview
NC Encrypt Data Sheet
CipherTrust Manager Connector Data Sheet
FREQUENTLY ASKED QUESTIONS
How can I apply end-to-end encryption when needed?
NC Protect can dynamically encrypt files at rest or in motion, when required, using secure AES-256 bit encryption that is FIPS 140-2 compatible. It can also encrypt SharePoint list values.
How can I manage my own encryption keys?
The NC Encrypt module provides encryption capabilities out-of-the-box for organisations using NC Protect that prefer to manage their own encryption keys. Using a central policy manager, it provides critical management of files stored and shared across all of your Microsoft 365 apps, SharePoint on-premises and File Shares. It also supports BYOK with connectors to third-party key management platforms using Thales CipherTrust Manager.
Can I encrypt data at rest? What about data in motion?
With NC Encrypt, organisations gain supplementary at rest and in motion encryption and decryption capabilities in Microsoft 365 using their own designated master key.
What if I already have a Key Management solution but want dynamic encryption?
With NC Encrypt, you have the flexibility to utilise a Bring Your Own Key (BYOK) approach at any point through a seamless integration with Thales CipherTrust Manager which provides connectivity to VSMs and HSMs. Linking CipherTrust Manager to NC Encrypt provides an innovative solution that allows you to manage your encryption key processes independently in CipherTrust Manager, while managing your dynamic encryption and access controls in NC Protect.
What if I want to use multiple encryption methods?
The NC Protect policy manager gives you the flexibility to apply different encryption methodologies to meet your security needs using NC Encrypt, Microsoft Purview Information Protection (MPIP), or CipherTrust Manager, or a combination of these depending on the file and use case. This is all made possible with NC Protect’s dynamic data protection policies.
How does NC Encrypt help with Data Sovereignty?
The NC Encrypt module provides dynamic encryption and key management to empower organisations to maintain data sovereignty and control over their encryption keys in the Cloud. Gain supplementary at rest and in motion encryption and decryption capabilities in Microsoft 365 using your own designated master key. The option exists to generate a default AES-256 encryption key on the fly, enabling a swift start. You also have the flexibility to utilise a Bring Your Own Key (BYOK) approach at any point through a seamless integration with Thales CipherTrust Manager.
Let’s Get the Conversation Started
Learn how NC Protect allows you to take control of your keys in M365 to meet security and compliance objectives.