ITAR & EAR Compliance
ITAR and EAR Compliance in Microsoft 365 and SharePoint
Meeting ITAR AND EAR Compliance in Microsoft 365 and SharePoint
International Traffic in Arms Regulations (ITAR), are issued by the United States government to control the export and import of defense-related articles and services on the United States Munitions List (USML). In short, the U.S. Government requires all manufacturers, exporters, and brokers of defense articles, defense services or related technical data to be ITAR compliant. The Export Administration Regulations (EAR) are issued by the United States Department of Commerce to control the export of items that are designed for a commercial purpose which could have military applications, such as computer hardware and software (Commerce Control List). If your company handles, manufactures, designs, sells, or distributes items on the USML you must be ITAR compliant.
ITAR and EAR violations can pose a huge risk for impacted companies. Defense contractors have been fined tens of millions of dollars for failing to control access to EAR and ITAR regulated data. Furthermore, they can impact more than just the bottom line – criminal penalties of 10 to 20 years in prison, depending on the regulation, are also possible.
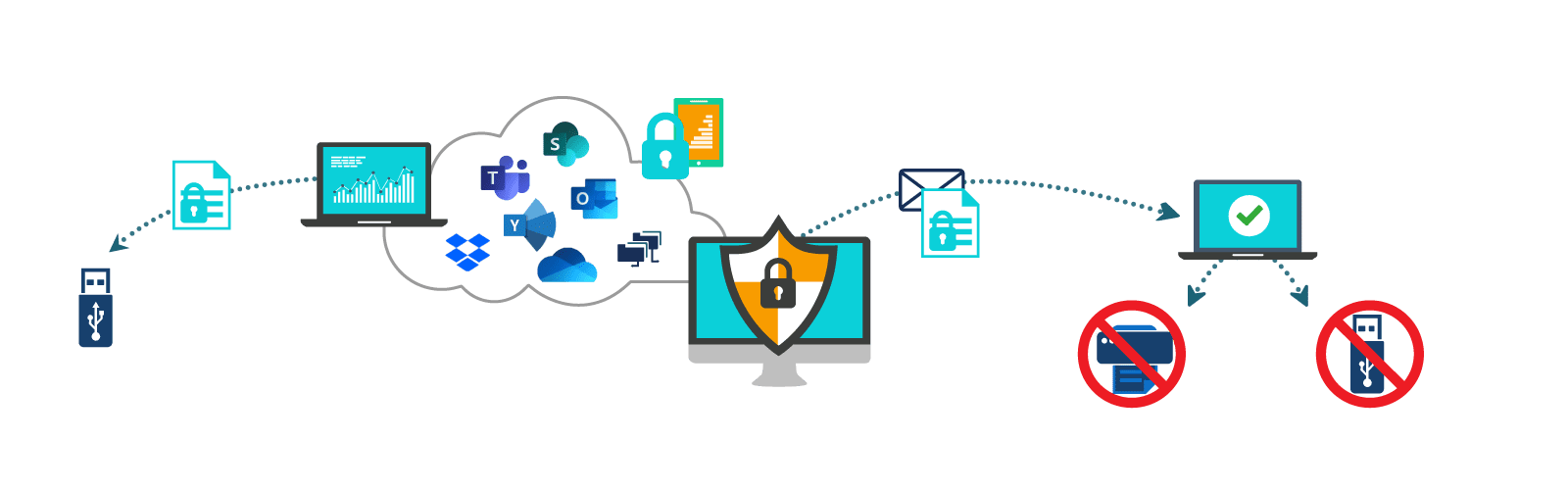
If your company falls under ITAR or EAR and you are using Microsoft 365 (M365), SharePoint Online or on-premises (SharePoint) to provide access to product development plans, hardware specifications, source code, and other sensitive information, then you must implement security controls in these applications to be ITAR compliant. The rules apply to any internal and external users or groups that have access to regulated content in the US and in many other countries as defined in the requirements.
It is one of the most complex access management issues to solve. To be ITAR compliant, multiple factors must be considered before sharing regulated content with M365 or SharePoint including:
- User clearance level and caveats
- User citizenship
- Document/item clearance level (i.e. top secret, confidential, etc.)
- Device (i.e. browser or OS such as iPad, Android, tablet or other mobile device)
- Geography and access locations
Trying to define access in M365 or SharePoint using item permissions would require the creation of thousands of security groups, and if using inheritance thousands of sites or libraries and folders. You also run the risk of exceeding the limit of allowed security scopes on a list. The complexity of these security schemes greatly expands the likelihood of multiple single point defects in individual user or document permissions – any of which constitute an export breach.
NC Protect provides a simple approach using real-time dynamic access and identity management.
data-centric zero trust access and data protection policies Help Ensure ITAR Compliance
NC Protect’s zero trust methodology uses attribute-based access control (ABAC) to determine access, usage and sharing permissions at the item level — without the need to create additional groups and independent of item permissions. Organizations define policies and dynamically define groups, permissions and access based on user and file attributes including classification.
With NC Protect access controls and information protection are applied to individual files, chats and messages in real-time, so sensitive content can be safely stored, shared and collaborated in Microsoft 365 apps and SharePoint—regardless of user membership, unlike solutions that secure or encrypt at the app or location level. This approach also controls the proliferation of sites to support individual collaboration scenarios.
KEY ITAR COMPLIANCE BENEFITS OF NC PROTECT
- Automatically identifies if a document falls under ITAR or EAR and classifies it based on its contents/sensitivity accordingly.
- Real-time attribute-based access control (ABAC) policies determine access, usage and sharing rights based on file and user attributes such as country, user citizenship, categorization, clearance level, etc.
- Dynamically embeds a CUI Designator Label including Owner Name, Controlled By, Category, Distribution/Limited Dissemination Control and POC into documents as a persistent watermark.
- Prevents the deletion of ITAR documents based on the published date or shipment date to meet retention requirements.
- Dynamically encrypt ITAR files at-rest or in-motion, as well as SharePoint lists using secure AES-256 bit encryption that is FIPS 140-2 compatible.
- Tracks chain of custody including file access and actions taken with it.
- Ingest user logs into Microsoft Sentinel or Splunk to trigger upstream actions and alerts.
- Enforces zero trust principles at the data level each and every time a document is accessed.
- Supports Microsoft 365, SharePoint cloud and on-premises, Windows file shares and hybrid environments.
Case Study
Learn how this Defense Manufacturer uses NC Protect to identify and restrict access to content containing CUI to meet ITAR compliance.
Get Advanced ITAR Information Protection that’s Simple, Fast & Dynamic with NC Protect
Discover how NC Protect’s advanced information protection capabilities prevent data breaches, unauthorized file access and accidental sharing to meet ITAR compliance in M365 apps, Windows File Shares and more — for a solution that’s simple, fast and dynamic.






Let’s Get the Conversation Started
Learn how NC Protect aids in ITAR and EAR compliance with dynamic access and data protection capabilities designed to proactively protect ITAR controlled information.
