Blog
Stay up to date on industry trends, security advice, product news and more.
Tips for Managing Unstructured Data Security
Explore the unstructured data security and protection controls needed to ensure only the right users have access to the right content at the right time.

Understanding EAR Compliance Regulations: Tips for US and non-US Companies
Understanding EAR Compliance: Tips for US and non-US Companies to manage compliance and data security obligations
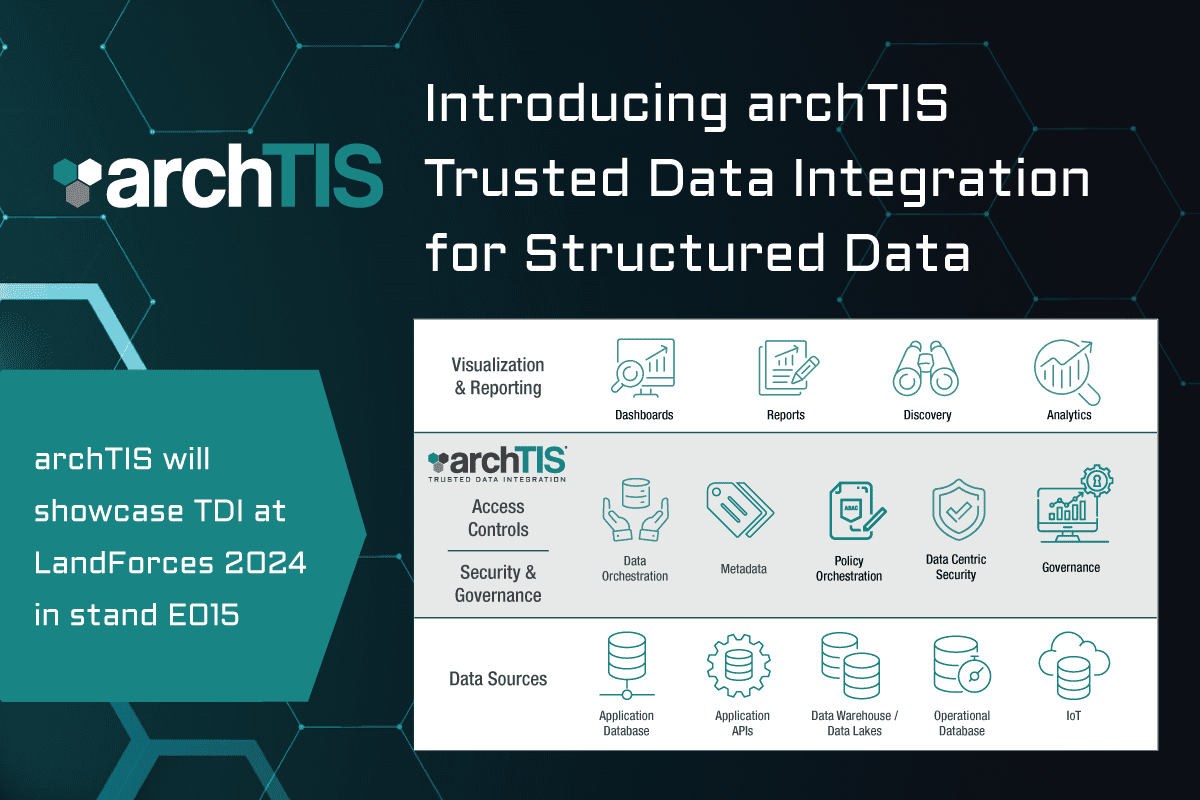
New archTIS Trusted Data Integration Solution for Structured Data
This week, during LandForces 2024 archTIS announced the launch of archTIS Trusted Data Integration, a new ...

Creating a Secure Community of Interest (COI) for Defence & Industry Information Exchange
Explore the use cases, challenges and tools for creating a Community of Interest (COI) for secure information exchange.

Understanding the Differences Between Fine-Grained vs Coarse-Grained Access Control
Fine-grained vs coarse-grained access control: How to choose the best option for your data protection needs.
Defense Supply Chain Data Security
This blog examines the top threats, best practices and tools for securing defense supply chain data security.

Why Artificial Intelligence (AI) Is Neither
What exactly is AI, and more importantly, how does it work? This blog delves into separating the facts from the hype.
Understanding the Differences Between DFARS and CMMC
Discover the Differences Between DFARS and CMMC to meet compliance and safeguard US DoD sensitive information and CUI.

DFARS 7012 Class Deviation and NIST 800-171 Rev 3 Guidance for DIBs
archTIS talks to Robert Metzger, head of RJO’s DC office and Cybersecurity and Privacy practice chair, about the impact of the DFARS 7012 Class Deviation and NIST 800-171 Rev 3 on defense contractors.

The 2024 Cybersecurity Excellence Awards Recognizes archTIS Products as Winners in Data-centric Security and National Cyber Defense
archTIS has won two awards in the 2024 Cybersecurity Excellence Awards in the National Cyber Defense and Data-centric Security categories.

Controlled Unclassified Information (CUI) Marking Requirements & Management in M365 & GCC High
DoD controlled unclassified information (CUI) visual marking requirements and how to implement them in M365, Office 365 and GCC High.

What is Policy Orchestration?
Explore how Policy Orchestration simplifies the complexity of data access, security and governance to accelerate decision-making processes in the cloud.

Understanding ITAR Compliance: A Guide for Australian Companies
To avoid ITAR risks, organisations must establish robust compliance programs and provide training to employees on the requirements for managing ITAR in Australia. Learn more in this ITAR checklist for Australian companies.

What is Attribute-Based Access Control or ABAC?
Learn about ABAC, the security model underpinning our solutions, and how it can be applied to secure collaboration of sensitive data.

archTIS Recognized as a 2024 Microsoft Security Excellence Awards Finalist for Compliance & Privacy Trailblazer
archTIS is pleased to announce it is a Compliance & Privacy Trailblazer award finalist in the 2024 Microsoft Security Excellence Awards. The company was honored among a global field of industry leaders that demonstrated success across the security landscape during the past 12 months.

archTIS Inspires Inclusion to Support International Women’s Day 2024
To celebrate International Women's Day our talented team members share their insights as ‘Women in Tech’ for those considering careers in the fields of technology and cybersecurity.

Safeguarding Classified Information
Understanding classified information handling requirements and technologies to help ensure information security obligations are enforced.

ITAR Compliance Checklist
Comply with ITAR regulations and establish an effective ITAR compliance and information security program using this comprehensive checklist of best practices.
