One of the biggest issues facing government and industry is how to securely share sensitive and classified information. While information sharing and collaboration have tremendous benefits for productivity and service outcomes, they do come with risks. A dynamic, data-centric approach is key to securing sensitive information and achieving compliance. Learn about attribute-based access control or ABAC, the security model underpinning archTIS solutions, and how it can be applied to secure your sensitive data more effectively.
ABAC Solves Modern Information Security Needs
Security that addresses insider threats and external threats is paramount for government, defense industry, research, intelligence, supply chain, and enterprise collaboration. In an attempt to address this threat, many organizations add layers of security that often slow productivity and increase complexity.
The goal is to ensure that only trusted users can share information with those who have the appropriate access rights. We also need to control how users and information recipients can use that information. All this needs to be done proactively without any negative impact on productivity.
The ABAC methodology is a highly effective solution that is increasingly being adopted as the recommended best practice by both industry and government. This is evidenced by the US government’s endorsement of it in NIST SP 800-162 ‘Guide to Attribute Based Access Control (ABAC) Definition and Considerations.’
What is Attribute-based access control (ABAC)?
Attribute-based access control (ABAC) is a security model that aims to control access to information by defining policies that dictate who can access information and under what circumstances. In ABAC, policies are created based on attributes such as user credentials, environment, and resource properties. By controlling access to information, the right people can access the right information at the right time.
In contrast, Role-based access control (RBAC) is a methodology that grants access based on the user’s role. In RBAC, an IT administrator sets access parameters for each role. Depending on the user’s position in the organization, they will have specific access permissions, and other roles will have different access.
The ABAC methodology enables more flexible and precise control over user access than the traditional RBAC model. ABAC’s ability to determine a user’s access rights to infrastructure, data, or resources after initial authentication is called fine-grained access control. Unlike the coarse-grained access control that RBAC provides, which grants access based on a single factor such as role. Learn more about the differences between ABAC and RBAC in this blog post.
How Does ABAC Work?
The ABAC methodology is designed to reduce risks due to unauthorized access, and control security and access on a more fine-grained basis. ABAC analyses the attributes of documents, users and their environment. A dictionary of attributes is used to build precise access control policies. The policy defines rules about what operations can be performed on an object’s data, who is authorized to perform those operations and the context under which those operations can be performed. These operations can include discovering, reading, creating, editing, deleting, and executing objects.
Here is a simplified example of ABAC applied to secure document sharing and collaboration of government-regulated sensitive information.
ABAC policy: “If User A has Citizenship = United States, Clearance = ITAR Cleared, and Department = 1, access is granted.”
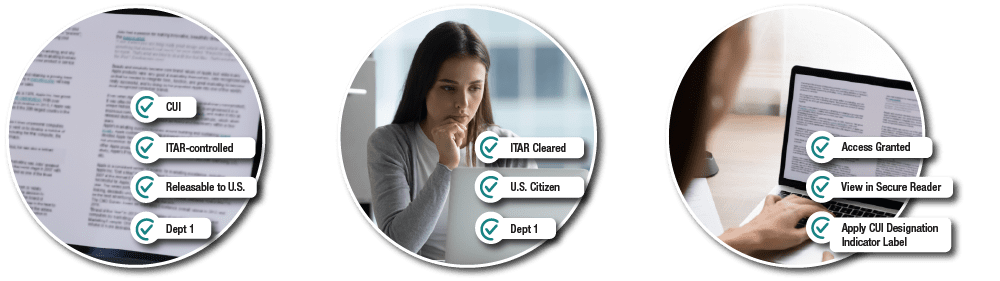
- The attributes of sensitivity level, citizenship and department are applied to the document (object) manually or using automated tools.
- User (subject) attributes are based on department, citizenship and ITAR clearance levels assigned to the individual.
- If all of the conditions within the ABAC policy are met, access to the document is approved. If not, access is denied.
The advantage of ABAC is more granular access control based on flexible policies that can accommodate multiple attribute combinations. ABAC policies are only limited by the available attributes.
ABAC enables access decisions to be modified when attribute values are modified. For example, instead of a user always being able to access sensitive information based on their security clearance, ABAC can place further limits on their access, such as only allowing it during certain times of day or only if they are in a certain country. As a result, governance and security teams can establish policies that can adjust access, usage, and sharing rights based on real-time comparison of user context and file content. This can reduce security issues and can also help with auditing processes later. This dynamic policy enforcement can enhance data protection and ensure compliance with regulations.
What are the Components used in ABAC?
Attributes are the characteristics or values of a component involved in an access event. With ABAC, security is built around the combination of different attributes, including user attributes (subject), environmental attributes and resource attributes (object). ABAC enables more precise access control with flexible policies that can accommodate multiple attribute combinations that are only limited by the available attributes.
Here are the examples of attributes that can be used in the ABAC model :
User Attributes
The attributes of the subject relevant to a request to grant or deny access. For example:
- Name
- Nationality
- Security Clearance
- Organisation
- Group
Environmental Attributes
Attributes of the environment relevant to a request to grant or deny access. For example:
Location
- Country
- State
- Address
Device
- Name
- MAC Address
- Credentials
Network
- Name
- Credential
- Classification
Resource Attributes
The attributes of an object or resource relevant to a request to grant or deny access. For example:
- Documents
- Videos
- Raw Data
- Images
- Classification
- Sensitivity level
What are the Benefits of ABAC?
Flexible, fine-grain policies
The key benefit of ABAC is its flexibility and granularity. Access decisions can change between requests by simply changing attribute values, without the need to change the subject/object relationships defining underlying rule sets. This also means fewer policies are required to manage complex access and sharing scenarios.
For example, an ABAC access policy asks three questions:
- What is the role of the the user accessing the document?
- Does the file contain sensitive data?
- What are the conditions of the user requesting access?
One ABAC rule can apply appropriate controls to multiple access scenarios. For example, if a project manager is attempting to access a contract document from their company laptop then ABAC grants access. However, if the project manager tries to access the same document from their mobile device while connected to public WiFi, the same ABAC policy will deny access. .
Dynamic Authorization
ABAC enables Dynamic Authorization, the process of granting authorization and access rights to networks, applications, and data dynamically in real time based on attribute-based rules/policies.
Scalable
ABAC is scalable and will grow with your company. Admins can create ABAC policies that permit new users to access resources. There is no need to modify existing rules or object attributes as long as new users are assigned the necessary attributes to access the objects.
Governance and compliance
ABAC policies can control various situational factors by utilizing attributes such as nationality, clearance levels, roles, departments, geography, device and more. This fine-grained access control allows organizations to tightly restrict access to individual resources on a need to know basis and follow regulatory compliance requirements.
ABAC Use Cases
- A product engineer can only access ITAR-controlled documents if he/she is a US Citizen physically located in the US.
- A finance manager can work on M&A documents in the office but not on public Wi-Fi in a coffee shop.
- A product manager reassigned to a new team needs to access information related to the new team but should no longer be able to access data from the old team.
- Only an HR manager assigned to a particular country’s operation or business unit can access the personally identifiable information (PII) data of employees in that country’s operation or business unit.
Solutions for Secure ABAC Driven Collaboration & Sharing
For Microsoft 365 and File Share users who want policy based access and protection
NC Protect is both content and context aware to automatically find, classify and secure unstructured data on-premises, in the cloud and in hybrid environments. It protects against breaches, sensitive data misuse and unauthorized file access enabling enterprises to fully take advantage of the intelligent workplace. NC Protect dynamically adjusts file security based on real-time comparison of user context and file content to make sure that users view, use and share files according to your business’ regulations and policies.
For Government and Defense Industry with Classified and Top Secret Information
Kojensi is a highly secure and trusted platform for sharing sensitive and classified files and document collaboration. It employs ABAC policies to ensure only authorized users have access to information under the right conditions and controls what they can do with that information. Organizations no longer need to add layers of security as an afterthought, which slows productivity and complicates processes. With Kojensi, create, co-author and share documents in real-time, all in a secure and intuitive platform that empowers collaboration and is highly secure-by-design.


