Audit & Track Sensitive
Data access
ingest logs and associated “events” into Microsoft Sentinel & Splunk
Audit and track sensitive data access
Today’s organizations must assume they will be compromised by a bad actor, disgruntled or even a negligent employee. We can no longer solely afford to settle for after the fact detection and user behavior analysis to detect a breach. NC Protect’s real-time data security leverages attribute-based access control (ABAC) policies which take into consideration content and user context, to prevent both negligent and malicious data loss, and audit and track sensitive data access. It provides advanced information protection that’s simple, fast and scalable to protect and audit sensitive information access across the Microsoft 365 collaboration stack.
NC Protect also provides out of the box centralized reporting and auditing capabilities to:
- Report on the number of issues identified by classification level.
- Allow policy officers to review the results and – if needed – rescan, reclassify or reapply permissions.
- Log and track sensitive access, user activities and actions such as producing, editing or deleting data, and general access.
- Track any changes to NC Protect settings and policies, and who made them.
- Ingest user activity and logs collected in NC Protect into Microsoft Sentinel or Splunk.

Get advanced insight & alerts with NC Protect’s
SIEM Integrations
Leverage the power of your SIEM applications, including Microsoft Sentinel or Splunk, for deeper analysis and to automate downstream actions from the insights gained from the audit logs created by NC Protect and cross-correlate them with the rest of your investigation and reporting ecosystem.
Easily ingest user activity and logs collected in NC Protect into Microsoft Sentinel or Splunk to analyze the data at cloud scale, as well as trigger holistic alerts and remediation actions alongside the dynamic and real-time access controls of NC Protect.
- Jump start threat investigation with just a few clicks using built-in Sentinel workbooks.
- Create custom reports and visualizations to analyze user activity and behavior tracked by NC Protect.
- Get advanced auditing capability by aggregating NC Protect access data with existing SIEM processes.
- Trigger real-time alerts and workflows on suspicious user activity.
- Report on guest file access and activity.
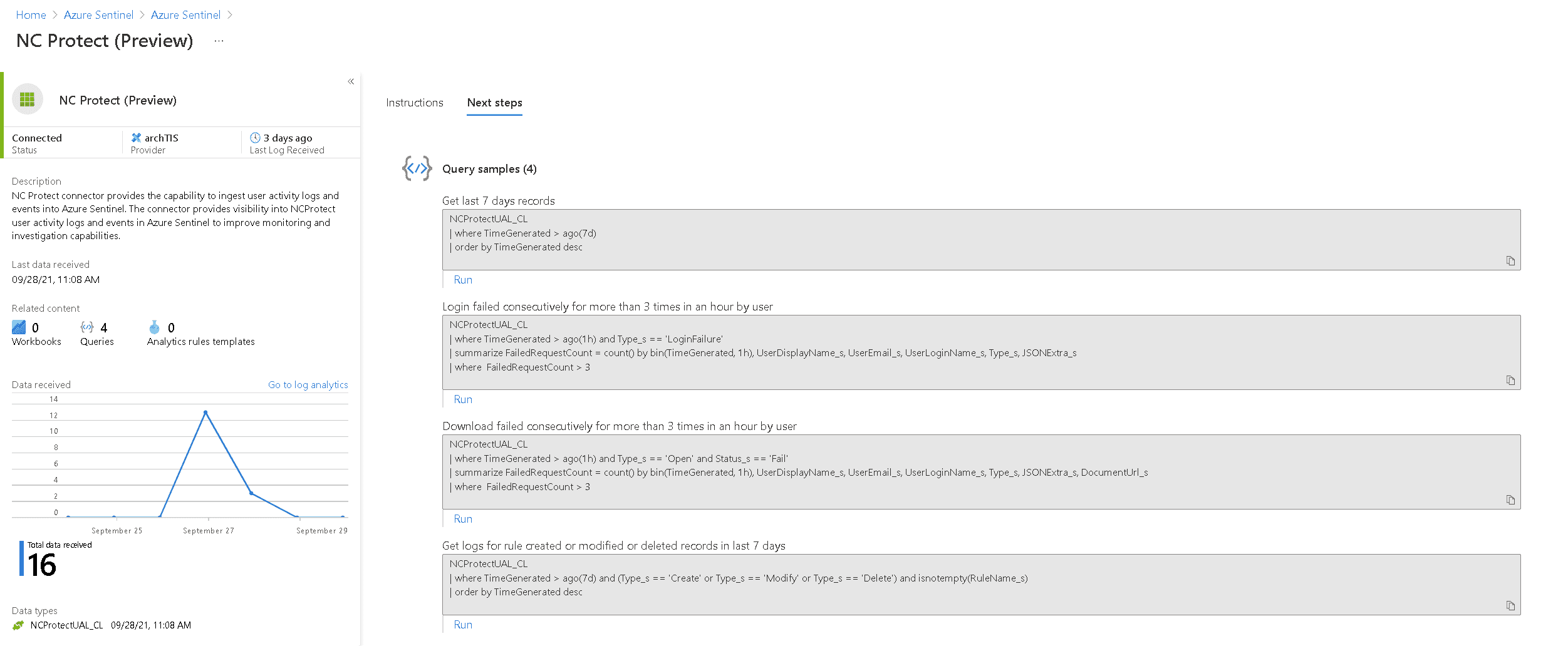
NC Protect data connector for Microsoft Sentinel
The NC Protect Data Connector for Microsoft Sentinel allows you to easily ingest user activity and protection logs and their associated “events” from NC Protect into Microsoft Sentinel.
Let’s Get the Conversation Started
Learn how to leverage NC Protect for data discovery and classification, paired with dynamic access and security to proactively protect sensitive information.
