NC Protect Resources
All Resources | Kojensi Resources | NC Protect Resources

Video: Simplify compliance and security with archTIS and Microsoft
Discover how NC Protect leverages Microsoft security investments to enhance information protection by adding dynamic ABAC policy-based access and data-centric controls to secure sensitive data collaboration in Microsoft 365, GCC and GCC High.

eBook: Securing the Edge – Mastering Data Security in Defense
Defense organizations need a robust, adaptive solution that can keep pace with these dynamic threats and ensure sensitive data remains protected. This eBook explores the opportunities for enhanced data protection when you combine NC Protect with your existing Microsoft ecosystem and solutions like Microsoft Purview Information Protection.

Webinar: Extending Microsoft Collaboration Applications with ABAC for Enhanced Security and CMMC Compliance
Explore how archTIS's NC Protect implements a Zero Trust model for file access and sharing, ensuring compliance with CMMC and NIST standards to enable secure handling and collaboration on FCI and CUI.

NC Protect NIST 800-172 ABAC Capabilities Matrix
This Capabilities Matrix highlights how NC Protect provides the access control mechanisms defined in NIST SP 800-162 Guide to ABAC.
White Paper: Protecting Sensitive Data with Digital Security Watermarks
How to Secure Your Digital Assets with Automated Security Watermarks: Use Cases and Tools

White Paper: ITAR Compliance Checklist
A guide to compliance and information security requirements and best practices for achieving ITAR compliance.

White Paper: CMMC 2.0 – Jumpstart FCI & CUI Protection with Data-Centric Zero Trust
Explore how extending a Zero Trust approach to file access and sharing ensures compliance with the CMMC 2.0 standards that map to NIST 800-171 and NIST 800-53 for secure and compliant collaboration of FCI and CUI.

eBook: The BYOK Gap in Microsoft Azure and M365
Understanding the potential risks of retaining encryption keys with Cloud Service Providers (CSP), including Microsoft Azure and Microsoft 365 (M365),
that can lead to data exposure and non-compliance with GDPR and other data protection laws.

eBook: Complying with Australia’s SLACIP Act & SONS Regulations for Critical Infrastructure
Risk management and governance are critical to SLACIP and SoNS, however, enforcing these mandates is another matter. Explore who these regulations impact, what is required and how to quickly stand up secure and compliant information sharing in this eBook.
Webinar: 5 Steps to Prepare SharePoint Data Before Migrating to M365
In this webinar, we share 5 key steps to prepare your data in SharePoint on-premises before you migrate to ensure a smooth transition to M365 and SharePoint Online.

Case Study: A Master Class on Digital Transformation and Data Security with NC Protect
Discover how archTIS’ NC Protect offers a solution to secure Skool4Kidz digitised curriculum in M365 with in-transit encryption and unique security capabilities.

Guide to Controlled Unclassified Information (CUI) Markings
Download this guide to understand the US DOD's new controlled unclassified information (CUI) marking requirements and how to automate the process.
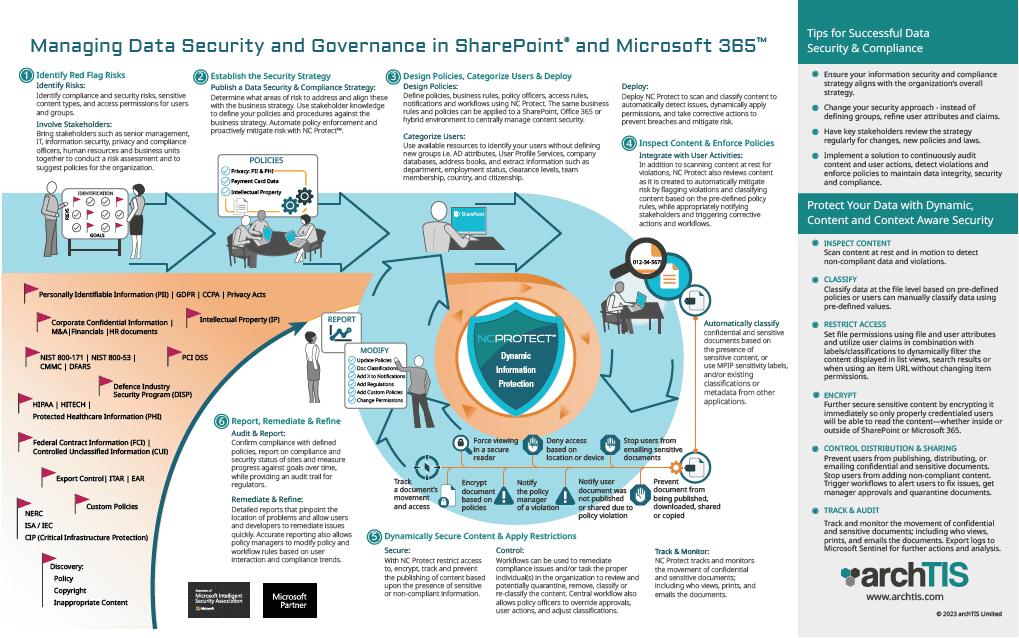
Infographic: Managing Data Security and Governance in Microsoft 365 & SharePoint
Get the steps for effectively manage data security and governance; from defining your strategy to using NC Protect to enforce compliance and apply dynamic security to Microsoft 365, SharePoint Server and file share content.

Webinar: Protect Sensitive Data with Microsoft Purview Information Protection & ABAC Policies
archTIS’ Dave Matthews and special guest Microsoft's Director, Director, Compliance and Privacy Ecosystem, Hammad Rajjoub, discuss how to enhance information protection controls to guard your most vital assets and ensure they don’t accidentally or deliberately walk out the door.

NC Encrypt Thales CipherTrust Manager Connector
The NC Encrypt CipherTrust Manager Connector provides an intuitive interface that links directly to CipherTrust Manager, enabling you to leverage your existing CipherTrust Manager keys to encrypt Microsoft application content.
Webinar: Independent Encryption Key Management and BYOK Support for M365 & SharePoint
Data encryption and key management are a core part of any organization’s security and compliance toolbox. However, many organizations prefer to manage their own encryption keys. In this recorded Webinar we discuss how to add independent key management and BYOK to your Microsoft 365 and SharePoint on-premises environments to minimize unnecessary access and build confidence in Microsoft services.

Request-For-Proposal (RFP) Template for Information Security Providers
Preparing a request for proposal or 'RFP' to purchase an information security solution to enhance data protection in SharePoint, M365, or Teams? Download this free RFP Template to easily collect important information and compare offerings from security software vendors to assist in the selection process.

Video: NC Protect Integration with Microsoft Purview Information Protection
Learn how Microsoft Information Protection sensitivity labels combined with NC Protect’s dynamic access and secure collaboration rules give you expanded protection and control over all your M365 collaboration.
No results found.
