In a world of hybrid, on-premises and cloud enterprise IT solutions, global communications and data regulations (i.e., PII, GDPR) that stipulate what information can be shared in which situation, organizations around the world need effective data loss prevention (DLP) strategies to prevent the theft and misuse of business critical assets.
Traditional data security solutions tend to monitor the specific threat points DEVICE ACCESS via end point security solutions, DISASTER RECOVERY via timely data backups and USER ACCESS via role-based (RBAC) permissions all in a static nature. These solutions react based on the permissions that are set.
So how do you make your organization’s data loss prevention strategies more proactive?
The creation, storage and sharing of information is mostly performed in an unstructured manor, and humans are mostly unpredictable and prone to error – making data loss due to negligence or malicious intent inevitable. You need a solution that can discover, monitor, control and audit the access to business critical information, for internal and external users, and in real time to provide a more proactive DLP strategy.
Essential Components for Proactive Data Loss Prevention
Discover
To provide real-time data control, a solution must be able to discover and isolate content that is deemed sensitive and classify or tag it as such within the organization’s repositories and collaboration tools. The rules that determine the data discovery processes should be central and work across on-premises, cloud and hybrid solutions to ensure easy management, consistency and compliance of corporate governance policies.
Monitor
Monitoring access to individual files, not just the application or folder, is essential to a proactive approach that can challenge the user’s permissions to access content in real time. The selection of the correct access control methodology at this point will determine the proactiveness of the solution and the extent of future technical debt that you take on in the ongoing management of information access within your organization.
By introducing Attribute Based Access Control (ABAC) methodologies to your DLP processes you benefit from dynamically applied security that challenges every access request in real-time.
The ABAC security model allows the business to define the rules of who can access certain information and under what circumstances. Controlling who accesses information and under what conditions ensures the right people to access the right information at the right time.
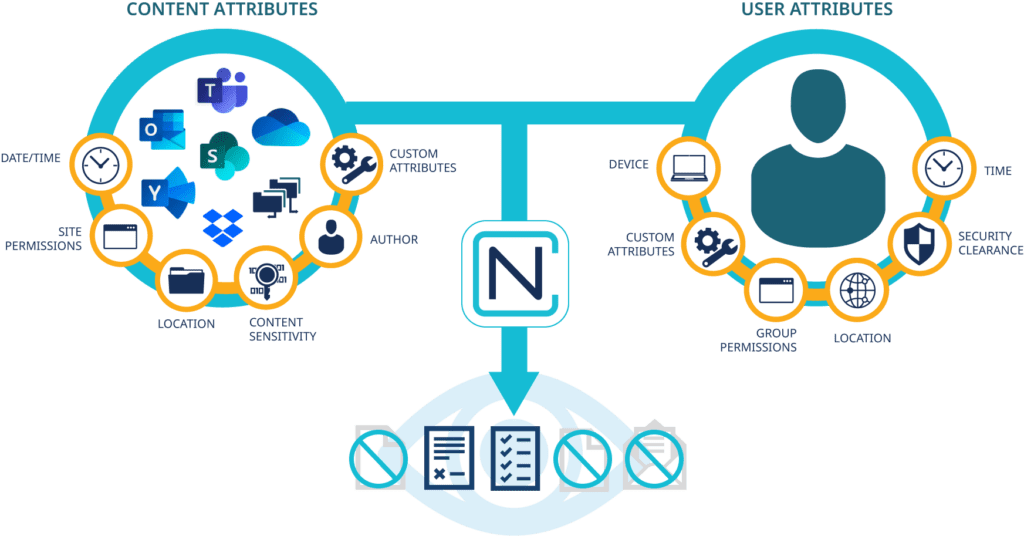
Using an ABAC-enabled solution, the controlling access attributes can be based on any combination of user (i.e. position, nationality), content (via discovery process rules) and environment (access point information). This allows governance and security teams to create policies which dynamically adjust access, usage and sharing rights to files, chats or messages in content services and collaboration platforms based on real-time comparison of user context and file content to enforce regulations and policies throughout the business.
Control
Once you have dynamic security controls, you can protect sensitive content in more granular ways. Depending on the user’s access, you can control the information that is contained in files or chats– by denying access/ hide restricted content / view all. Hide or show files in common repositories to different users in effect making advanced real-time information barriers on your existing document repositories.
Determine the actions that a user can perform on a document – edit, view as read only, print or email a document – to prevent accidental sharing of information. Advanced DLP solutions should also be able to redact sensitive information and watermark documents to further increase the security of the information.
These dynamic decisions are not only made on the defined users attributes, but also the file’s classification and environmental elements like physical location – therefore access to documents will dynamically change based on the user’s scenario at that moment in time to meet the organization’s governance policies.
Audit
It goes without saying, that any data loss prevention solution must provide auditing on all the interactions that a user has had on a document or chat. This is especially important for regulated industries that must track access to sensitive information (e.g., PHI/HIPAA, PII/Privacy Acts, trading information/SEC, etc.). Whilst in product audit reports are vital for quick referencing, the ability to dynamically feed these reports to SIEM solutions will ensure that you are able to monitor corporate trends across your entire IT infrastructure.
Many solutions on the market do pieces of this. For example, some focus on discovery and classification, but not protection. There are more holistic solutions that can provide an end-to-end solution for consolidated and less complex data discovery, classification and protection. When evaluating solutions, you also need to consider your resourcing requirements for the ongoing management of the solution (e.g., IT, security). From a governance perspective you also need to determine how granular your controls need to be based on the sensitivity and industry regulations that are governing the data in your care.
IMPLEMENTING ABAC-POWERED DATA LOSS PREVENTION SECURITY
As data loss from users becomes more prevalent and stringent regulations governing sensitive data continue to evolve, data loss prevention solutions that are underpinned by ABAC will provide your organization with more granular and real-time access controls over sensitive and business-critical information stored and shared across enterprise document management and collaboration tools.
NC Protect is an advanced data-centric security solution that is both content and context aware to automatically find, classify and secure sensitive data in on-premises, cloud and in hybrid environments including Microsoft 365, SharePoint Server, Dropbox, Nutanix Files and Windows File Shares. It protects against data loss, sensitive data misuse and unauthorized file access enabling enterprises to fully take advantage of the productivity benefits these collaboration tools offer. NC Protect’s ABAC-based policies dynamically adjust file security based on real-time comparison of user context and file content to make sure that users view, use and share files according to your business’ regulations and policies.
Learn more or contact us to discuss how we can help you implement a proactive ABAC-powered data loss prevention strategy.


