The world has changed and along with it the strategic role of information security
Now more than ever, the Boardroom, Chief Executive Officer and Chief Information Officer have Information Security front of mind and keeping them awake. Every day a new attack, incident or vulnerability is announced that has a significant impact on reputation, compliance, cost or service delivery. The pandemic has brought digital investment forward to introduce work from home environments, including collaboration platforms such as Microsoft 365 and we are producing data and content at a prolific rate. Enterprise data is now everywhere, both inside and outside the enterprise perimeter. CIOs cannot tell you where the data is, whether it is sensitive, how they are controlling it or who has access to it.
All this is occurring at a time when legislation is increasingly holding Directors and Executives more accountable for securing organizational and personnel data. A number of Governments are now considering voluntary or mandatory governance standards to focus on cyber security as a corporate risk, as well as the risk to national and economic security.
Finally, the threat of a cyber incident is only increasing. According to the Australian Cyber Security Centre’s Annual Cyber Threat Report 2020-21, over 67,500 cybercrimes were reported, an increase of nearly 13 percent. That is one report every 8 minutes compared to one every 10 minutes last year.
The role of information security has irrevocably changed in this environment. More importantly, users will no longer tolerate security controls impeding functionality and productivity in a digital world that is accelerating past geographic and enterprise boundaries.
Chief Information Security Officers, despite increasing budgets, must now adapt to this environment and lead their organizations on a new Information Security paradigm to both protect and enable their data whenever and wherever it is required in a cost-effective, risk-managed way.
Zero trust has quickly become the model of choice. Learn how a Zero Trust Access model centers its controls directly around the data vs the systems and applications that it sits behind.
What’s all the fuss about Zero Trust?
The concept of “Zero Trust” (ZT) in security has been around for a number of years. Simply put, the Zero Trust approach dictates that you must verify and validate each action, every time, in context, to the level needed to meet the desired level of confidence for a decision.
The idea is that dynamic systems can explicitly verify everything needed, while minimizing assumptions so that decisions are made within an organization’s risk appetite. In a recent report, Microsoft outlined the 3 guiding principles that should underpin a zero trust methodology as follows:
Verify each and every time
Continuously authenticate and authorize using all available data points, attributes and context; user identity, location, device health, service or workload, data classification, and anomalies.
Enforce least privileged access
Use a combination of ‘Just-In-Time’ and ‘Just Enough’ Access (JIT/JEA), risk-based adaptive policies and data protection practices to safeguard your data and user productivity.
Assume you are breached
Adopt this proactive security posture to prevent threats and quickly address any you encounter by:
- Segmenting network, user, device, and application access to minimize the attack surface and prevent lateral movement.
- Encrypting all sessions end to end.
- Leveraging monitoring and analytics to provide visibility, detect threats and improve your overall defenses.
The zero trust approach is considered so critical, that in 2021 the U.S. Presidential Cybersecurity Executive Order for Cybersecurity mandates that all U.S. federal agencies must transition to a Zero Trust Architecture (ZTA).
NIST Special Publication 800-207 describes ZTA, and many industry analysts have covered the concepts, including Forrester with their Zero Trust eXtended (ZTX) model, as well as Gartner’s Lean Trust and Continuous Adaptive Risk and Trust Assessment (CARTA) model.
The 6 Pillars of Zero Trust
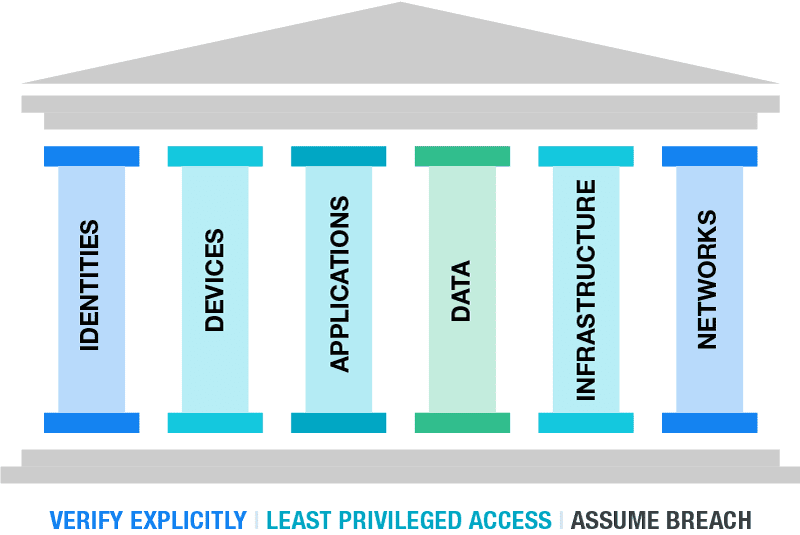
To implement zero trust, these 3 key principles need to be applied across the following 6 foundational areas:
- Identities including users, services or devices.
- Devices as they create a large attack surface as data flows.
- Applications are how users consume data. Controls should be applied to ensure appropriate access, monitor for abnormal behavior, and control user actions.
- Networks should be segmented.
- Infrastructure, whether on-premises or cloud-based, represents a threat vector.
- Data should be classified, labeled and encrypted based on its attributes.
The idea is that dynamic systems can explicitly verify everything needed, while minimizing assumptions so that decisions are made within an organization’s risk appetite.
In a new study by Microsoft and Forrester, customers implementing a Zero Trust security strategy realized the following benefits:
- A 92 percent return on investment (ROI) within three years with a payback period of fewer than six months.
- Lowered the chance of a data breach by 50 percent with the ability to detect abnormal user behavior, identify potentially compromised accounts, monitor native and open authentication (OAuth) apps, and detect and remediate attempted malware attacks.
- Security process efficiency gains of 50 percent or more.
What is Zero Trust Access?
While the concept of Zero Trust is important, and the principles behind are solid, it does need careful consideration to minimize targeting the wrong areas when executing the methodology.
What if you could base your Zero Trust data security approach on a few core principles, in a model that builds strong foundations of comprehensive, dynamic security of your most critical assets, capped by a layer of verification and validation that meets your needs, in your context?
Principle 1: Data-Centric Security
When we focus on placing the controls on critical data assets, versus the perimeter or user permissions, this is referred to as data-centric security. At its most simplistic, it is making sure that security and controls are on the data itself and have the right level of protection relevant to the sensitivity of the information.
Next, we hit another key consideration for protecting your data assets; how do we know what is “relevant”?
The answer is that it almost always depends on the context, and it can change over time as the content and context change.
For example, a document may start out being non-sensitive but say someone adds confidential information on an M&A deal that only a small team should know about – thus, the sensitivity and audience have changed. Now think about under what conditions someone should access this data. Should they have the same access in a coffee shop that they would when they are in the office?
Principle 2: Context is critical, it drives relevance
For data and its security to be relevant, the context is critically important in defining what, where, and how access is needed. It can also be flexible, applicable to almost anything, and in any combination.
Many organizations have mandatory information security and privacy requirements, including the type of information they can capture, hold, and use and how it must be handled. These legal obligations become both major constraints and significant value drivers, and meeting these expectations is not optional.
Numerous compliance obligations may apply and interact regarding data security and handling requirements, including, but not limited to:
- US Health Insurance Portability and Accountability Act of 1996 (HIPAA) requirements for Protected Healthcare Information (PHI)
- Personally Identifiable Information (PII) is governed under a plethora of multinational, country and even state regulations, for example, the European Union’s General Data Protection Regulation (GDPR), Australian Privacy Act, California Consumer Privacy Act (CCPA), and more.
- International Traffic in Arms Regulation (ITAR)
- US Defense Cybersecurity Maturity Model Certification (CMMC)
- Australian Defence Industry Security Program (DISP)
If the context and the need for security to address it change, then how can you adapt to the changing requirements?
Security needs the ability to be adaptable and dynamic, to deal with continuously shifting needs.
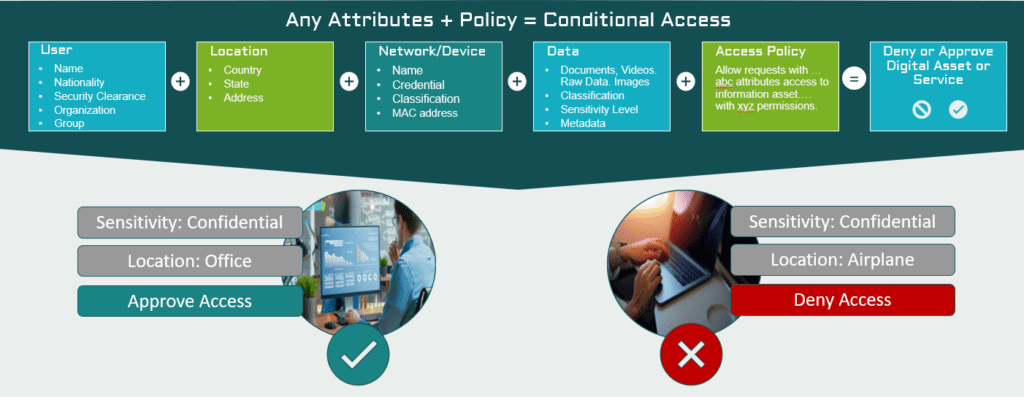
Principle 3: ATTRIBUTE-BASED Access Control (ABAC)
You may be familiar with the idea of “If you can’t measure it, you can’t manage it.” For information technology systems to make a Zero Trust Data Access approach effective we need a means to measure or detect the context of the request, the requestor, and other contextual elements.
Attributes are the characteristics or values of a component that can provide this context. They can contain almost any value (either manually defined or automatically system-assessed) so that we are able to measure and define each key/value pair, such as “company=archTIS”, or “country=Australia”, which allows a system to “uniquely” identify that attribute in the correct context and relevance.
Using these attributes to decide who can access data and under what conditions is the concept of attribute-based access control or ABAC.
Principle 4: Dynamic Policy Enforcement
Once we have the attributes, we then have to decide what to do with the request. Is it authorized? What is the correct response, Permit/Deny? Provide anonymized or tokenized subset of information? Should it be referred to another party for approval?
The terms and conditions of access (whether described as rules, policies, controls, or otherwise) need to become adaptable and enforceable wherever they go, and however they’re applicable. This is the concept of “Dynamic Policy Enforcement,” and it becomes the means with which to achieve that contextual security.
Bringing it All Together
Zero Trust Access comes down to verifying and validating each step, each action, and each element needed in order to satisfy the underlying needs – whatever they are.
Using a data-centric zero trust security approach enforced by ABAC ensures appropriate checks and balances are enforced, and that they are relevant to the sensitivity of the data – in the context of whatever the access or sharing scenario is.
This is critical when considering security in modern information systems, as the context is continually shifting.
Identity + context + request + rules + dynamic decision = enforced contextual security
Implementing Zero Trust Access
If you’re sold on implementing zero trust, consider archTIS solutions.
archTIS products apply and enforce dynamic, policy-driven access controls that leverage both user and data attributes to ensure your users and partners access, share and collaborate on sensitive and classified information — securely.
Whether you need to manage sensitive data securely within your Microsoft 365 applications (SharePoint, OneDrive, Office and Exchange), SharePoint Server or Windows file shares or need to manage access to and sharing of classified information stored with high levels of assurance – archTIS can assist. archTIS puts you on the path to zero trust access and protection with immediate benefit and return on investment, while enabling your big picture goals.


