To Encrypt or Not to Encrypt?
Read our tips on when to use encryption and other steps you can take to protect sensitive data.
Many organizations want to leverage encryption in their environments. This usually starts with encrypting data and devices that physically leave the organization. External USB drives with encryption or internal drive encryption on laptops using BitLocker, for example. We have all heard stories of secret government documentation being left behind on the train or a laptop with employee information left in a Taxi while traveling. This small step helps minimize exposure (and potentially heavy fines) when traveling with sensitive data and is a smart way to limit this potential security issue.
In addition, organizations attempt to encrypt data in motion, specifically as it moves across the physical boundaries of the office via SSL on websites, VPN, email etc. Then, they look at encrypting data at rest throughout the organization, usually in a one-off methodology for specific, highly sensitive files.
The Downside of an Encrypt it all Approach
However, doing this ‘piecemeal’ encryption and protection strategy becomes unwieldy. Eventually, organizations often look at encrypting data at rest throughout the organization. This is a logical way to look at data security, but encryption on a large scale does have some downsides.
- High Resource Utilization – Blanket encryption of all your data can result in significant computational overhead, especially in large organizations with a substantial amount of data. The data must all be encrypted and then selectively decrypted whenever an authorized user wants to use it. It must then be re-encrypted when an authorized person has modified the document.
- Potential loss of encrypted data – Changing a user’s password or even removing a laptop from a domain can make the data stored by the user or on that device non-recoverable if you don’t have a copy of the key. Making the data so secure that you can no longer access your own information is obviously not helpful.
- Complexity – Needing to push out encryption keys and determine who can access your data. Large-scale encryption programs can be challenging to roll out.
Encrypting all the data throughout the organization probably doesn’t make sense because of these downsides. Instead, look at the data that is company sensitive or regulated: intellectual property (IP), healthcare data (PHI), Payment card data (PCI), personally identifiable information (PII), etc. For example, Healthcare information, Credit Card data, and employee and customer data are a lot more important than your standard company memos, policies and procedures and where your Christmas Party will be held this year.
Using Classification to Aid in Determining What to Encrypt
How do you determine what’s sensitive and needs to be encrypted? Data classification is not just crucial for governance; it can also be used to add security trimmings to sensitive data, such as encryption and more.
Two primary methodologies are used to classify data as sensitive: Manual and Automated Classification.
- Manual classification means the user is responsible for determining whether a document is sensitive. This can be done through a third party tool or the manual addition of a metadata tag, a SharePoint Column value, a sensitivity label, or an MPIP label that’s been added to the document. This approach has a few downsides, including having to potentially go through a significant volume of existing documents. Militaries tend to prefer Manual classification because a document may contain unclassified information (people, places, things) that, when combined due to a specific event, are considered classified. This type of classification can be difficult to automate.
- Automated classification works very well for existing documents and takes the need for user interaction (and mistakes) out of the equation. Automated classification works much better with items that are easy to quantify. For example, Credit Card numbers, National ID numbers and easily recognizable strings of data that can be found using Regular expressions or lists of keywords.
Combining these two mechanisms can provide a highly customized experience, especially if you have more complex classifications. It ensures a high degree of classification and tagging accuracy that can be leveraged to protect your documents dynamically.
Reaping the Benefits of Automated Encryption
Ensure that your organization’s business-critical data is classified and protected according to your business regulations and applicable regulatory policies. NC Protect adds granular policy-based access and protection controls to business-critical content in Microsoft 365 applications.
It has its own built-in Classification engine to determine whether the data is sensitive automatically. Further, if you have been tagging data manually (or leveraging another data classifier), NC Protect can leverage that existing data or a combination of the two. Finding and protecting sensitive data while still adding protections (possibly different levels of protection) to data that has been manually classified can provide a very secure result.
Dynamically Encrypting Data at Rest
NC Protect can leverage Microsoft RMS encryption and can apply this encryption only to the specific documents or types of documents (i.e., documents marked as sensitive, CAD drawings, financial documents, etc.) you want to encrypt. NC Protect also offers an encryption tool if you prefer not to use Microsoft’s encryption or wish to manage your own keys.
With NC Protect, encryption can be applied to specific types of data at rest in a very granular manner. However, it can also add additional access and security controls to data accessed under specific conditions. For example, you may not consider it necessary to encrypt data accessed by trusted users internally from a company-issued laptop.
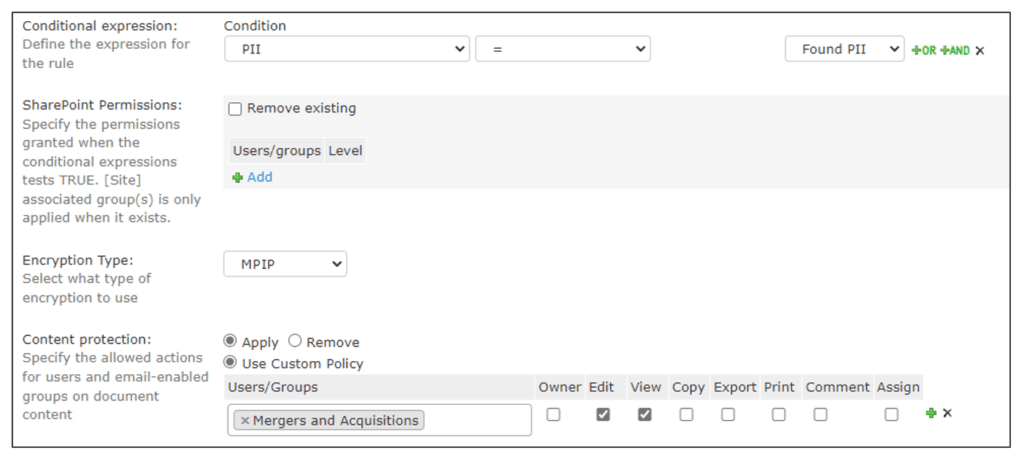
However, you may want to provide additional protections when that same user accesses that same data from their phone or outside the country. NC Protect is powerful enough to leverage that user’s attributes to provide dynamic protection tailored to the situation, including encryption and watermarking on the fly. So, when in the office, the users can access the document normally with no restrictions, but on the go, they can be presented with an encrypted file that’s watermarked with their user information when opened.
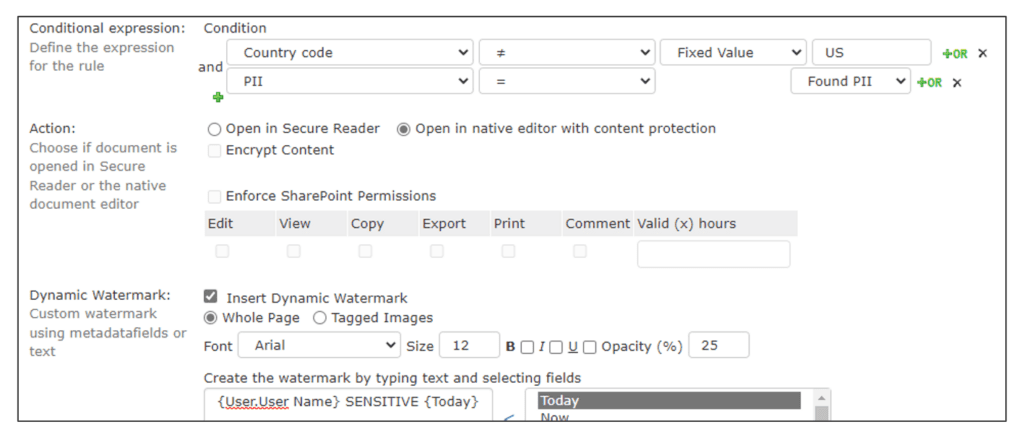
In the screenshot above, you can see that you can add access and usage restrictions to users when they access sensitive data from outside of the country or when the data is being accessed (or attempted access) from a different device type, from an unauthorized browser type or even by different IP addresses. This can help prevent accidental data loss or data exfiltration if an employee is working in a public location versus a more secure site.
Dynamically Encrypting Data IN MOTION
Aside from encrypting data at rest, NC Protect policies can automatically encrypt emails and sensitive files shared via Exchange email to ensure only the intended recipient can access the information. It can also block email attachments that contain sensitive data or replace attachments with a link to a secure web viewer or file URL that requires additional authentication and verification.
Data Protection Beyond Just Encryption
While this post concentrates on encryption, NC Protect can provide additional protections such as forcing read-only access that prevents print, download, copy and paste to obfuscating sensitive data from users, such as Guest users or users from other countries if you’re dealing with ITAR restrictions. Encryption does not need to be applied to files if users can’t see they exist.
This post gives you some ideas on how to leverage encryption and other security mechanisms to protect your data, no matter where it resides in your environment. If you have any additional questions or are curious if this solution is right for you, please get in touch with us.


