There is saying, “If a man keeps an idea to himself, and that idea is taken by stealth or trickery, I say it is stealing. But once a man has revealed his idea to others, it is no longer his alone. It belongs to the world.” Intellectual Property is the ‘secret sauce’ of every organization, it’s what sets you apart from the competition and gives you an edge. It goes without saying that Intellectual Property theft can have dire consequences to the survival of your company. Despite this knowledge, there are five serious misconceptions about IP Theft that are putting your organization at risk.
How China Stole an Entire Airplane
In October 2018, ZDNet ran a story on how China’s efforts into establishing a foothold in the aviation industry by building its home-grown plane left a trail of hacks across the aviation industry. Through a coordinated approach, “contractors” (such as hackers, cybercriminals) are hired and assigned the theft of particular interest. If they cannot gather intelligence, Chinese intelligence will recruit company insiders, or even coercing Chinese employees to aide their hacking efforts using blackmail or threats against families living at home.
According to the security firm Crowdstrike, the end goal was to acquire the needed intellectual property to manufacture all of the C919’s components inside China. An accusation filed in California on October 25, 2018, charged 10 Chinese individuals with conspiring to steal aerospace trade secrets from 13 western companies, most of the U.S. based. The indictment also revealed that French aerospace manufacturer Safran was infiltrated when employees in its Suzhou, China office inserted malware into the Safran computer network. This malware gave Chinese agents access to Safran’s confidential files.
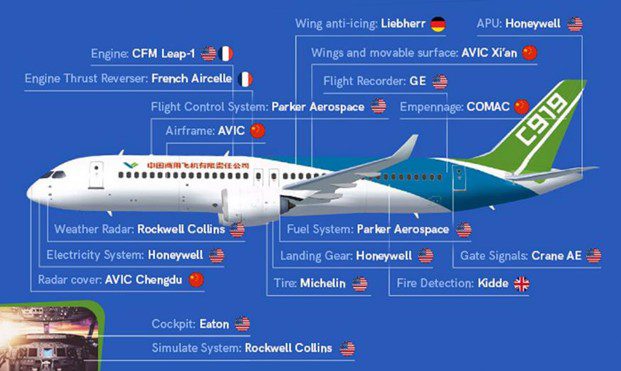
According to U.S. Trade Representative Robert Lighthizer, China’s IP theft costs the US between $225 billion and $600 billion each year.
What is Intellectual Property?
Intellectual property, also referred to as ‘IP’, is the production of new ideas you create and own by your organization that is critical in achieving its missions.
The types of intellectual property are varied:
- Proprietary software / source code
- Business plans, proposal, strategic plans
- Customer information
- Product information (designs, formulas, schematics) Some examples:
- KFC – It’s their recipe
- Coca Cola – It’s their recipe
- Tesla – It’s their software
- Google – It’s their search engine
How is Intellectual Property at Risk from Insiders?
Insider threats fall into two categories: malicious and negligent acts that put business-critical data at risk. Malicious threats come from people within the organization, such as employees, former employees, contractors or business associates, who have access to inside information concerning the organization’s security practices, data, IP and computer systems. Intellectual Property theft is when one of these insiders steals proprietary information from the organization with the intent to use it for personal gain.
Some known examples:
- In January 2019, Apple accused one of its employees for stealing over two thousand files containing confidential and proprietary Apple material, including manuals, schematics, photographs and diagrams relating to its company’s self-driving car.
- In July 2019, Tesla accuses a former engineer of theft of files containing Autopilot source code to his personal iCloud account in late 2018 while still working for the company.
- In January 2020, a former SoftBank Corp. employee was arrested for allegedly passing proprietary information from the major phone carrier to officials at Russia’s trade representative office in Tokyo.
- In March 2020, former Google employee Anthony Lewandowski pleaded guilty to stealing trade secrets from its self-driving car program to found Otto, a self-driving truck startup, which Uber acquired for a reported $680 million.
What is the impact of insider Intellectual Property theft?
The impact of insider theft of IP can be devastating. Trade secrets worth billions of dollars have been lost to foreign countries, competing products have been brought to market by former employees and contractors, and invaluable proprietary and confidential information has been given to competitors.
Five Misconceptions About IP Theft Putting You at Risk
The following five serious misconceptions about Intellectual Property Theft put organizations at risk.
1. Very few insiders ever steal intellectual property to sell it.
Instead, they steal it for a business advantage either to take with them to a new job, to start their own competing business, or take it to a foreign government or organization.
Here is an example. A Chinese EV startup Xpeng, have stolen some of Tesla intellectual property, but it’s not stopping the company from straight-up copying its website design too.
2. IT administrators are the biggest threat.
Many people believe that because they hold the “keys to the kingdom”, that they would be the prime suspect for theft of IP. According to Insider Threat Division of CERT, there is no observable case in their database which shows IT administrators stole intellectual property.
Those that steal intellectual property are usually current employees who already have authorized access to that IP (around 75% according to the insider Threat division of CERT). Such as engineers, programmers, or salespeople.
3. High-level security technologies such as SIEMS can identify and prevent IP theft.
Technology is not able to recognize human behavior from logs and system events. You cannot infer logs to a reveal user’s intention and motivation.
Did you know, that “dissatisfaction” played a significant role in many of the IP thefts? Dissatisfaction notably resulted from the denial of an insider request, which in turn decreases the person’s desire to contribute and diminish loyalty.
Yet, machines are not able to recognize “negative emotions” as a risk and businesses regularly miss these “red flag” behavior warnings.
Importantly, with these types of tools you cannot detect theft of IP until the information is in the act of being stolen. In other words, the window of opportunity can be quite small.
That’s why it is essential to pay close attention when you see potential physical behavior indicators of heightened risk.
4. IP theft takes place after hours and requires sophisticated hacking.
Not so! Most of these crimes tend to be quick thefts around resignation. In most documented cases IP was stolen during business hours and within one month of resignation using a variety of methods. But some of them stole slowly over time, committing their final theft right before departure.
“All of us have the right to change jobs, but none of us has the right to fill our pockets on the way out the door. “ – US Attorney David L. Anderson
5. IP theft is only conducted by a single person.
IP theft can be initiated by an individual that may not have access to the IP. However, other insiders can be recruited or coerced into providing the IP.
According to the Insider Threat Division of CERT, around 33% of IP theft was for the benefit of a foreign government or organization.
What Can You Do to Mitigate Theft of Intellectual Property?
To prevent your intellectual property from walking out the door, consider the following set of recommendations.
1. Review employee contracts
Employees bring information with them and possibly competitive and stolen IP from their previous employer. Be aware that your organization may be liable for the theft. As part of your IP agreement that you make new employees sign, include a statement attesting to the fact that they have not brought in any IP from any previous employer.
It is inevitable that many of your employees will move to other businesses at some point in time. As soon as an employee or contractor turns in their resignation, you need to be prepared to act. Identify what information they are accessing. Identify movement of that information 30 days prior to resignation and 30 days post-resignation.
- Establish consistent exit procedures which should include:
- Access termination procedures,
- Ask departing employees to sign a new IP agreement reminding them of the contents of the IP agreement while they are walking out of the door
- Review your termination policies and processes
2. Pay attention to physical behavior
Dissatisfaction, disgruntlement, or a negative argument over their entitlement may lead them down the path of IP theft.
3. Periodically review and adjust your access controls.
Many insiders at the time of stealing information, had access above and beyond what their job description
4. Don’t just monitor, prevent abnormal user activity.
Monitoring data movement such as unusual activities – large attachments; printing sizeable documents; copying or downloading certain information to laptops and removable media, and monitoring of users when they give notice of resignation are all good things to do. But at that point the data is gone. Once it leaves your company systems a user can email it or upload it to cloud storage in a matter of second. The damage is essentially done.
Instead look for solutions that proactively prevent users from stealing your IP and other sensitive information in the first place. NC Protect is one such solution that is specially designed to prevent insider threats.
NC Protect dynamically adjusts file security based on real-time comparison of user context and file content to ensure users view, use and share files according to your business’ regulations and policies. With NC Protect prevent IP theft and misuse with data-centric protection that proactively:
- Prevents downloading of IP and sensitive files to removable media and PCs.
- Stops users from attaching sensitive files to emails.
- Forces users to view sensitive documents in NC Protect’s secure web viewer for read-only access to prevent saving, copying, downloading and printing.
- Automatically embeds personalized watermarks when user view or edit sensitive documents that include attributes such as the user’s name or email and the time and date that the file was accessed. Create a digital thumbprint that travels with the document even if someone tries to circumvent security by snapping a photo.
- Dynamically changes the user interface (UI) in Office 365 apps to hide files, channels and tabs from users based on their permissions. Users can’t steal what they can see.
An ounce of prevention is worth a pound of cure
When is comes to IP theft it’s far better and less costly to stop it from happening in the first place, than to repair the damage afterwards. Understanding the threat of insiders stealing IP is real is the first step – but employing technology to thwart attempts is critical to protect your business and bottom line.
Guest Bio
 Boaz Fischer is the Chief Executive Officer of CommsNet Group, a firm that he founded in 1996 specializing in helping organizations to identify, mitigate and disrupt Insider Threats by focusing on addressing the human element.
Boaz Fischer is the Chief Executive Officer of CommsNet Group, a firm that he founded in 1996 specializing in helping organizations to identify, mitigate and disrupt Insider Threats by focusing on addressing the human element.
Boaz is certified by Carnegie Mellon University in the subject of Insider Threats as well as being Master Certified in Neuro-Linguistic Programming (NLP) with a focus on addressing the human psychology and how that impacts business success.
He is the author of four books:
- “The Essential Guide To Information Technology Security Best Practices” (2010)
- “Protecting Your Business from Cyber Attacks In Only 10 Minutes A Day” (2015)
- “Protecting Your Business From Insider Threats In 7 Effective Steps” (2017)
- “How To Protect Your Business From Cyber Breach In Only Two Minutes A Day (2020)”
As well as publishing over 200 security articles. Boaz has a regular and popular YouTube insider risk discussion titled “Naked Insider”, where he peels the “onion layers “off to understand why people behave the way they do.


