Adding Multiple Watermarks to Protect IP in Microsoft Excel, Word and PowerPoint
Protecting intellectual property (IP) and trade secrets is critical to a company’s bottom line. Keeping IP and sensitive business-critical information within the confines of the company and its employees is not always possible, especially in the manufacturing industry. Vendors must often share previews of new products with retailers and distribution partners before release. In defense manufacturing, they may need to share designs with multiple vendors building parts for warfighting vehicles and platforms. Digital watermarking is an important tool to ensure employees and third parties don’t share IP outside of their intended audiences.
Sharing IP Can be Risky
Oftentimes, manufacturers create and share intellectual property, product designs and sensitive images with third parties as part of the supply chain process. These materials can include presentations, documents, and images that contain unreleased or proprietary designs, artwork or products. Leaked IP can significantly impact the manufacturer and their supply chain partner’s marketing strategy, sales and competitive advantage.
Unfortunately, IP theft often goes unnoticed until it reaches the open market, or, worse, is used by a competitor. The problem is expansive, and the stakes are high, with intellectual property theft costing the U.S. economy alone up to $600 billion annually.
Top 3 Sources of IP Leaks
The age of digital transformation has made it easy for sensitive data and IP to be leaked or breached. Here are the 3 most common sources of data leaks.
Insider threats: Intentional or accidental leaks originating from employees or contractors working on a project are called ‘insider threats’. In the manufacturing industry, supply chain partners are also potential sources of leaks. Insider-perpetrated leaks can arise from simple negligence or mistakes or from malicious intent such as financial gain, personal agenda, or a desire for notoriety. For example, a Dupont research chemist pled guilty in 2007 of misappropriating the company’s intellectual property. He had downloaded 22,000 abstracts and accessed 16,706 documents outside the scope of his job.
Hacking and cyberattacks: Cybercriminals often target company networks or email accounts to access, steal and sometimes release sensitive files. Attacks are often initiated by foreign powers or competitors seeking to steal technology or new product information and reproduce it as their own.
Physical theft: Printed or photographed information can literally walk out the front door and subsequently be leaked online or shared with unauthorized individuals. The National Guard classified data leak in April 2023 is a prime example of this type of breach and an insider threat. It involved a National Guardsman with top-secret security clearance printing and photographing classified national defense information and posting it online for personal notoriety.
Preventing IP Theft with Digital Watermarks
Implementing strict security protocols for employees and contractors and watermarking documents with the handler’s information is critical to protect IP. It ensures that your users comprehend the sensitivity of the information they are handling and any policies that govern it. Furthermore, if an employee’s information is displayed all over the document, it discourages photographing. It also creates a digital thumbprint in case of a data leak allowing companies to easily identify the leak point.
Technologies that dynamically watermark documents ensure that sensitive data is automatically stamped offer the best protection. NC Protect automates the watermarking of Office documents (Word, PowerPoint and Office), PDFs, CAD files, and more, with attributes of the user accessing the file, including name, date, time, and any other attributes a company needs to track the chain of custody and warn users of document sensitivity.
Adding Multiple Watermarks to Protect Documents and Images in MS Excel, Word and PowerPoint
While a single watermark is beneficial, adding a separate watermark to a sensitive image within a document or presentation ensures the image itself is protected in the same way.
You may be thinking that’s a great idea, but is it even possible to add multiple watermarks to a document? The answer is yes with NC Protect. In addition to watermarking a document, it can also individually watermark images and other elements within the document. This multi-watermark approach ensures sensitive or copyrighted images are independently marked as sensitive – automatically.
NC Protect’s policies are automatically applied in real time based on the combination of user attributes, document sensitivity and environmental conditions at the time of access. Therefore, security controls and access rights can change depending on the situation. For example, if a user is in the office, they may be able to access the document in the Office application so it can be edited with the watermark automatically applied. If they are at home, it will be displayed in a secure read-only Reader app with their information displayed as a watermark.
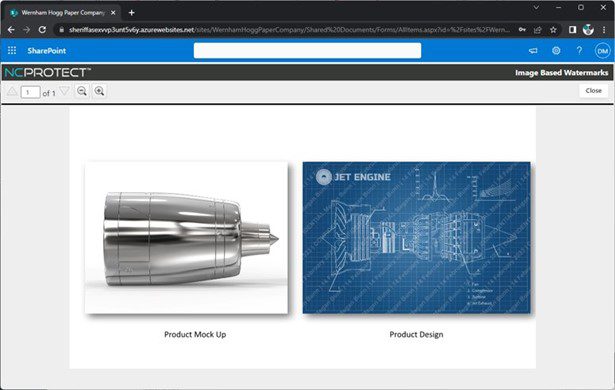
Dynamically watermark sensitive images in a document based on their classification with NC Protect. Force IP and sensitive data to be displayed in the built-in Secure Reader app to prevent users from printing, copying, or downloading files.
Advantages of Dynamic Digital Watermarks for Microsoft Office with NC Protect:
- Dynamic. When an employee views or downloads a document, NC Protect will automatically watermark the document and/or sensitive images with the employee’s name, date, time, client name, and any other data required by your organization.
- Documents and Images. NC Protect can add multiple watermarks and watermark individual images within a document. Supported file types include Word, PowerPoint, Office, PDFs, CAD files and images.
- Digital Thumbprint. Watermarks remind employees and partners of the content’s sensitivity and discourage photographing. If someone takes the risk, watermarks provide a clear forensic trail of who, what, and when the leak occurred.
- Persistent. Watermarks are applied in the native application (e.g. Word, PowerPoint, Excel) and users are able to share and edit watermarked document contents, but not the watermark itself, for security and auditing purposes.
- Read-only Access. Watermarked documents can be displayed in a built-in Secure Reader app that disables the print, download and copy functions if required.
- Customizable. NC Protect’s dynamic data-centric policies are flexible, allowing you to create fine-grain security and access rules to suit your business’ specific needs.
- Defense Visual Markings. Embed CUI Designation Indicator markings including Owner Name, Controlled By, Category, Distribution/Limited Dissemination Control and POC, as well as headers/footers into documents as a persistent watermark.
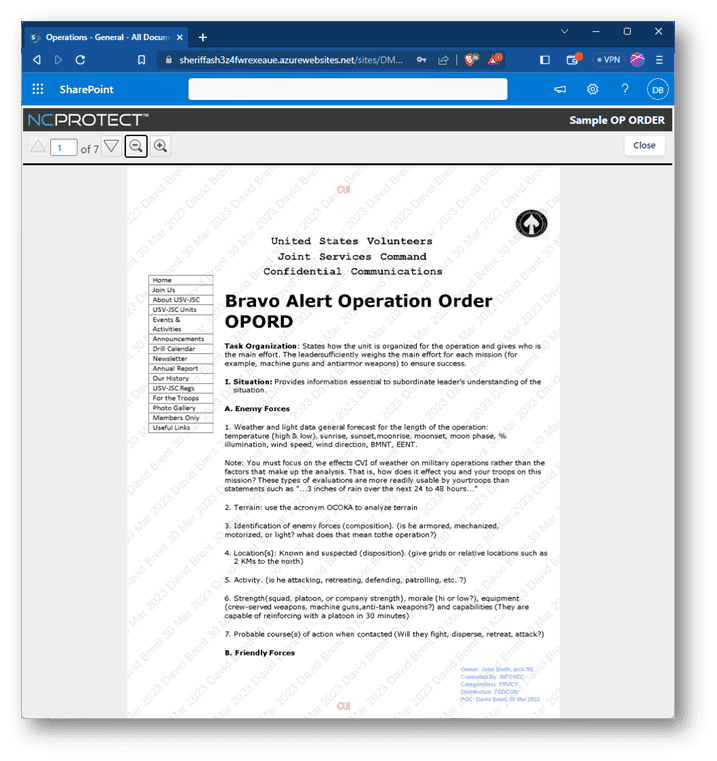
CUI Designation Indicator label and headers and footers dynamically added to Controlled Unclassified Information (CUI) with NC Protect as a persistent watermark and displayed in the built-in Secure Reader app.
NC Protect helps proactively manage and mitigate IP data leakage, which can result in millions of dollars in lost revenue. It enhances data security and provides more secure collaboration in Microsoft 365, SharePoint on-premises and File Shares to help protect your company’s IP, brand reputation and bottom line. Contact us for a demo today.


