Defence and Supply Chain Information Sharing Require Strict Controls
Implementing the right separation and information protections needed to meet defence requirements can be a challenge. Dynamic Multi-Level Security (MLS) offers a solution.
In today’s global environment, defence and the complex industry supply chains that enable these operations blur the traditional lines of geography and locality. Even more so as we collaborate and share information daily with our partners, suppliers, subcontractors, and our clients, using numerous combinations of information systems and media.
In the defence industry sensitive information handling comes with mandated comprehensive controls. Having systems that enable and can enforce these controls to meet requirements is essential to your information collaboration and sharing security needs.
However, the task of balancing effective security whilst still enabling information sharing in these complex environments is difficult. Dynamic policy enforcement and Multi-Level Security (MLS) methodologies can ensure that separation and protections are in place for contextual access to information without hindering authorized collaboration, whilst also stopping unauthorized access and sharing – a must to meet defence and industry supply chain requirements.
What is Multi-Level Security (MLS), and why is it important?
A security classification is the hierarchical category assigned to information and material that identifies the degree of damage that unauthorised disclosure or compromise would cause to a nation, generally regarding military or other government business. The classification denotes the degree of protection and control required for the storage, transmission, and utilisation of the information.
Alongside security classification is a compartmentalisation layer of separation and associated control requirements. Sometimes referred to as codeword, sensitive, compartmentalised, and can include releasability, caveats or rules around the sharing or dissemination of that information artefact.
All systems have security boundaries, whether logical and enforced, or ephemeral and inadvertent. A security boundary naturally exists wherever two different “security domains” (which could be a set of security requirements, control objectives, or even handling characteristics) come together for some reason. It can be between classifications, between compartments, between organisations, between networks, between systems, or even between nations.
This sort of complexity means that we need the ability to measure and enforce contextual security, with rules or policies that are defined, required, and applied – also referred to as “dynamic policy enforcement” that can provide assurance which can be independently verified by a security assessor.
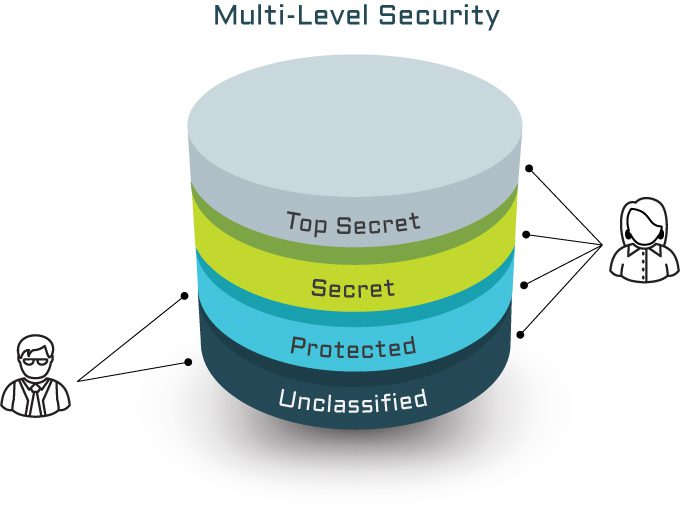
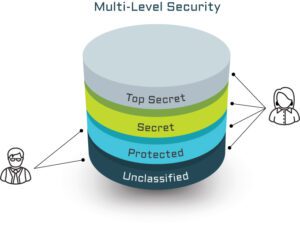 An MLS capability (system, platform, or environment) allows information at different classifications to be stored and accessed within a single security domain, while enforcing different access policies and compartments dynamically depending on context, with the assurance that the separation is effective.
An MLS capability (system, platform, or environment) allows information at different classifications to be stored and accessed within a single security domain, while enforcing different access policies and compartments dynamically depending on context, with the assurance that the separation is effective.
MLS provides your organisation with the ability to:
- Enable custodians to label and tag their content creations in the system.
- Controls and releases information to individuals/devices/locations that meet the contextual rules.
- Enables dynamic policy enforcement and access controls to information.
- Enforce contextual controls based on labels, tags, and other attributes.
- Enable granular controls to apply either between or inside security domains.
By adding controls like Attribute-based Access Control (ABAC), MLS becomes even more effective. When utilising ABAC as the dynamic policy enforcement method you can control provide granular access control at the most appropriate context. These attribute controls can be expressed as a key=value pair (for example [Nationality=Australian], [Location=Canberra, Australia], or [Organisation=archTIS]). By dynamically measuring the attributes of the user or device and aligning it to the rules of access for the information, ABAC can be an effective way to ensure only the right people in the right context can get access to the information.
What are the benefits of combining MLS and ABAC?
MLS combined with the dynamic capabilities of ABAC can enable and support complex information sharing challenges and offers several benefits to:
- Increase the accuracy, provenance and speed of getting the right information to the user, within multiple operational and security contexts.
- Improve access management of compartmentalised information, within contextual constraints.
- Assist to collapse networks and reduce the number of systems that users have to interact with, including potentially within deployed scenarios.
- Enable multi-national information sharing within mission related network environments, potentially improving interoperability and effectiveness.
- Enable files and documents to be rapidly created and shared respecting the security rules and set by the owner.
Fast tracking MLS to comply with information protection obligations
archTIS’ Kojensi platform provides the security controls needed to help you comply with information protection obligations, including MLS. Kojensi provides an assured and accredited SaaS solution to store, share and collaborate both internally and with supply chain, partners, and clients on information up to Australian PROTECTED.
For organisations that need multiple organisations and multiple nationality personnel to share and collaborate on documents and files, Kojensi enables the individual to set the rules for sharing of this info – providing immediate value.
Kojensi delivers several key capabilities and functions, including:
- An ABAC-based MLS platform that enables user driven establishment of virtual workspaces or communities of interest (CoI’s) via an intuitive UI.
- User controlled allocation and invitation of personnel to CoI’s.
- The ability for users to create, modify and upload documents and files, allocating metadata tags to these documents to control their releasability.
- The ability for users to edit documents within the browser, with co-authoring and an easy to use interface that enforces and respects the rules of access.
- The ability for users to modify document and file metadata to permit wider user access to the document.
- The ability for authorised users to modify document and file metadata, to narrow access only to users who have the necessary attributes.
- The mapping of the agreements for handling of security classifications from different nations to support multi-national information sharing.
archTIS can provide the same level of granular ABAC-based control for Microsoft applications with our NC Protect product. It offers advanced information protection across M365 apps including SharePoint (Online and on-premises), Exchange and Office 365, enabling simple and dynamic enforcement of rules (such as automatically detecting and enforcing releasability, encryption, clearance requirements, community of interest, or by keyword and other metadata tags) of data. NC Protect enables simple policy-based access, usage and sharing controls and compliance enforcement for sensitive information, even in an online and cross-jurisdictional scenario like this.
With over 15 years of experience providing architectural and security input to government clients, archTIS’ has deep domain expertise across all elements of sensitive data protection and sharing, including working within multi-national, cross-domain and multi-domain scenarios, including environments up to TS-SCI within both US and Australian contexts.
Need MLS? Let us help.
To benefit from archTIS’ expertise delivering multi-level security, cross domain solutions within the highest security areas of government contact us today.