The UK government’s Security Policy Framework (SPF) outlines the expectations and requirements for security measures to be implemented across UK government departments, and external agencies handling government information and data assets. The framework covers various aspects of information security, including governance, risk management, technology and services, and culture and awareness. In this article, we examine how information security is addressed in the framework, the data classification and marking requirements of the Government Security Classifications Policy (GSC) and how to align your data management policy with the SPF using automated data-centric information protection.
UK Security Policy Framework
The UK Security Policy Framework considers that all information that His Majesty’s Government (HMG) deals with has value. HMG handles various types of sensitive information, and it must ensure the confidentiality of citizen data, commercial information, and national security-related data. Additionally, the SPF states that HMG aims for good governance, and efficiency in data handling and meeting its obligations to international partners.
In all of the above, HMG expects its partners in the public sector, suppliers, and other commercial entities that handle government information to adhere to the same principles.
UK Government Security Classifications (GSC) Policy
The UK Government Security Classifications Policy (GSC) identifies and values information according to its sensitivity to drive the proper protections. The policy was enacted in 2014 (and updated again in 2018) to replace the previous Government Protective Marking Scheme (GPMS). The GSC updates the classification markings used by UK government bodies and was adapted for use in modern workplace environments.
The GSC uses three levels of classification, each with a baseline set of security controls to provide appropriate protection against typical threats. Additionally, ICT systems and services may require
enhanced controls to manage data risk and integrity.
- TOP SECRET: Information marked as TOP SECRET deemed the most sensitive and could cause considerable loss of life, international diplomatic incidents, or severely impact ongoing intelligence operations if compromised. Disclosure of such information is assumed to be above the threshold for prosecution under the Official Secrets Act.
- SECRET: This marking is used for very sensitive information that needs protection against serious threats, which might seriously damage military capabilities, international relations or the investigation of serious organized crime if compromised.
- OFFICIAL: All routine public sector business, operations and services are classified as OFFICIAL. Many departments and agencies operate exclusively at this level.
-
- Data at the OFFICIAL classification may be shared across government agencies, however, where a need-to-know principle is identified, the document should be marked as “OFFICIAL-SENSITIVE”; “OFFICIAL-SENSITIVE COMMERCIAL”; “OFFICIAL-SENSITIVE LOCSEN” or “OFFICIAL-SENSITIVE PERSONAL”.
-
- All OFFICIAL-SENSITIVE documents must be marked and contain special handling instructions that identify why the data is deemed sensitive, and how it must be held, processed, and transferred.
All documents produced by a public sector entity in the UK are presumed to be OFFICIAL unless otherwise marked. Document markings are optional for OFFICIAL classified documents. Otherwise, classifications must be capitalized and centrally positioned at the top and bottom of each page in the document. The UNCLASSIFIED marking was deliberately omitted from this new classification policy. Everyone who works with UK government bodies, including contractors and suppliers, is responsible for marking and protecting the information that they work with.
The classification label relates only to the document’s confidentiality. When classifying a document, the owner must consider the risk if the data within is exposed. For example, suppose a company was to label a document as OFFICIAL. In that case, they accept that the data in the document does not offer value if a Foreign Intelligence Service, or Organized Crime outfit compromised it. When classifying documents, the label must consider the capability and motivation of potential threat actors.
Applying Government Security Classification Markings
The Security Policy Framework clearly identifies that businesses and organizations working with UK government departments are responsible for labeling and protecting HMG data according to the classifications in the GSC.
But how do you ensure that your users understand the classification requirements and appropriately label them?
One option could be to use the built-in tools in Microsoft to force headers and footers through document templates. Microsoft can ensure new documents are automatically labeled OFFICIAL, and you will then have your users appropriately update the labels of OFFICIAL-SENSITIVE data and above. The downside of this approach is that mistakes are easily made when policy enforcement is dependent on user applied classification, due to simple mistakes and/or misunderstanding of the classification guidelines. This method also does not address files that are not editable with Microsoft Office, such as PDFs, images and CAD drawings.
Automate Security Policy Framework and GSC Compliance with NC Protect
With NC Protect from archTIS, businesses can automatically apply the required visual markings, including headers, footer and classification level, and more, to various file types to ensure they comply with the Government Security Classifications Policy. In addition, NC Protect offers dynamic, personalized security watermarking that goes beyond just stamping a document as OFFICIAL.
By using attributes from the document, such as the author, originating department, file location and automatic classification scans, NC Protect can identify the classification level appropriate to the file and apply the proper protective markings.
NC Protect is deployed in your application environment and integrates with your collaboration tools to seamlessly augment sensitive data access and data protection controls. As a result, no additional software needs to be deployed on your servers, desktops, or mobile devices.
Creating a dynamic protective markings policy in NC Protect is a simple process and is managed by the product’s policy manager. Building a rule to control access and automatically apply markings is simple. Simply select which attributes or file properties will be used to define the document’s classification. These attributes can be selected from a drop-down list of predefined values, or customized properties can be added.
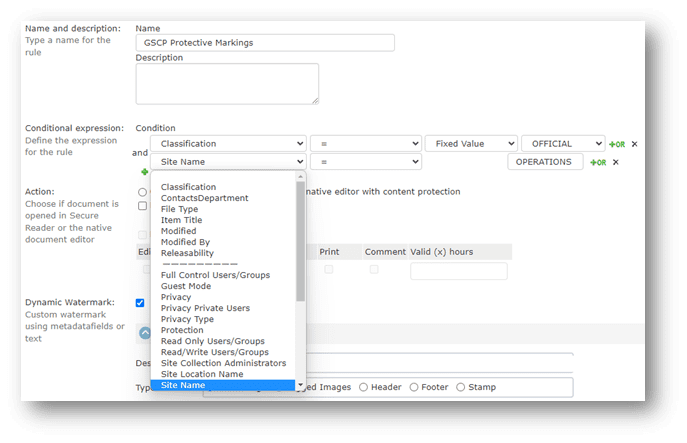
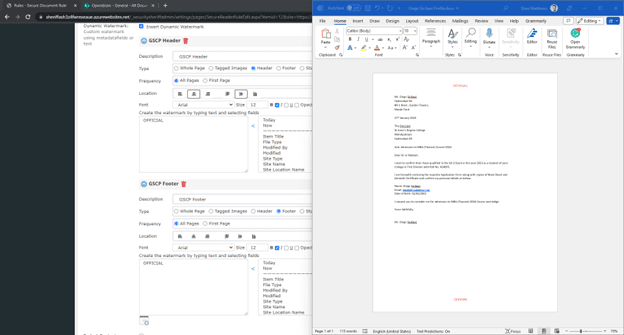
Building Dynamic GSC Marking Policies
NC Protect’s persistent dynamic watermarks can apply protective markings to existing files and legacy data stored at rest in document libraries and on file servers. Or they can be dynamically applied to documents at the time of user access. The users cannot remove them for security purposes.
Protective markings are configured in the dynamic watermarking menu and can be customized to appear as your GSCP policy requires. NC Protect lets you select the type of marking, its location and frequency, as well as formatting the appearance so that the fonts and colors align with your corporate branding. In addition, watermarks can be customized with any combination of user or file attributes.
NBC Protect’s Watermark feature supports the following GSC marking and protection use cases:
- Headers & Footers: Add markings to multiple document types using a single rule. For example, a header and footer can be configured in the same policy and applied to various document types in numerous locations throughout your organization.
- Special handling instructions. These additional markings can be used in conjunction with a classification to indicate the nature or source of its content and signify the need for enhanced handling measures.
- CUI Designation Indicator labels – Dynamically add CUI visual markings to documents that meet US export and Controlled Unclassified Information (CUI) requirements such as ITAR, NIST, CMMC, DAFARS
- User Access Information: Include additional watermarks such as the user’s name, email and the time and date of access. Watermarks create a digital thumbprint that travels with the document and deters unauthorized duplication or distribution of protected content.
Protecting Sensitive Information Access with NC Protect
With NC Protect, you can go beyond just applying protective markings to dynamically manage access and apply file-level protection to data at rest and in transit to ensure that you adhere to all of the principles of the UK government’s Security Policy Framework.
NC Protect uses attribute based access control (ABAC). This data-centric security model utilizes user, environment and file attributes, not roles, to control who accesses information and under what conditions, to ensure that only the right people can access the right information at the right time.
A simplified example of an ABAC security policy applied would be using geographical location to determine access rights to an OFFICIAL-SENSITIVE document as in the image below. For instance, if the user is accessing a protected document from within Australia and has the proper permissions, access is granted according to the policy. But if they attempt to access it from an international location, access is blocked or limited to a redacted read-only view.
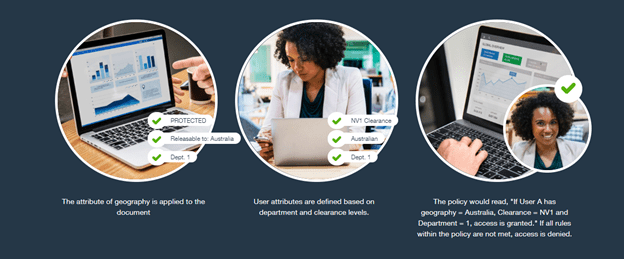
NC Protect’s ABAC policy goes beyond simply granting or denying access to sensitive data. Businesses can automate data encryption for files stored on-premises, in Microsoft 365 and attached to Exchange emails. Dynamic redaction policies can remove or replace protected codewords and patterns of text. Provide secure, time-limited guest document access. Audit and track all file activity and access. Event logs can be ingested by SIEM solutions such as Microsoft Sentinel and Splunk to monitor who is accessing what, when and where and trigger real-time alerts and workflows on suspicious file activity.
Finally, NC Protect provides document discovery and dynamic classification services. These features work out of the box, so your organization can automatically identify and classify sensitive documents. Classifications are applied based on the file attributes, keywords and patterns of text found in the document, identifying clues found in document images, or using a custom dictionary or protected codewords to identify data that demands protection.
Enforce UK Security Policy Framework and GSC Compliance with NC Protect
With NC Protect, enforcing a robust data security policy and automating compliance with the UK government’s Security Policy Framework and Government Security Classifications is easy. It is deployed into your existing application environment (M365, SharePoint on-premises, and/or File shares). Its agentless design means no software is installed on end-point devices for easy deployment and management. Significantly, NC Protect’s ABAC security policies go far beyond SPF compliance to provide granular control over sensitive data access and actions users can take once access is granted to ensure government data remains properly marked, secure and need to know.