Struggles with Guest Access in Microsoft 365
Speaking with clients, I find one of the biggest issues they struggle with is how to properly secure Guest access in Microsoft 365 applications.
While many organizations had already begun outsourcing their email to M365, most had really only begun looking at the rest of the M365 offering (Teams, SharePoint Online and OneDrive) when COVID hit. Most organizations wound up diving headfirst into this offering in an attempt to deal with the sudden need to work and collaborate with colleagues from home. Many organizations had their budgets and resources thrown entirely into this new deployment.
To give a little bit of perspective, from April 2020 to April 2021, Teams alone more than doubled from 70 million users to 145 million users. Incredibly, in the following quarter alone, Teams added another 105 million users to bring the total up to 250 million at the end of July 2021. In 2021, 86% of organizations reported that they had migrated from SharePoint On-Premises to SharePoint Online.
With the sudden rush to roll out the rest of the M365 environment, it seems many just weren’t able to perform their due diligence regarding security. They are now going back and revisiting their current posture around M365. The features that make M365 such a great tool for collaboration can also make it “too easy” to collaborate with anyone, particularly those we don’t want to share sensitive data with – whether internal or external users.
I personally have dropped data into folders that I had forgotten contained more people than I really wanted to share that particular data with. While I’ve been fortunate not to share anything too critical, there have been a number of incidents where that has happened, including one at the US Army Futures Command.
Conveniently, NC Protect makes it much easier to place Information Barriers between internal users and Guest users.
Control how Guests access and interact with your data
Dynamic ABAC Policies
NC Protect attribute-based access control policies (ABAC) can limit guest access in a number of ways, the simplest of which is to deny guests the ability to view any information labeled as ‘sensitive.’ Guest users have a ‘Guest’ attribute within the environment, so you can create a simple Dynamic Access rule in NC Protect to prevent guests from viewing data labeled as or containing sensitive information and apply it across SharePoint and OneDrive. It doesn’t matter if the Guest has full access to the container that the data resides in or not. If the data is marked as sensitive, Guests won’t even see that it exists.
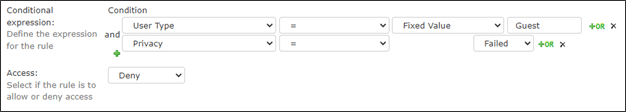
NC Protect has a built-in compliance engine to discover and tag sensitive data such as Credit Cards, National ID numbers, CUI data, or it can perform custom keyword searches. NC Protect can also leverage existing classifications, including Microsoft Purview Information Protection/MIP sensitivity labels and third party metadata, to prevent Guests from accessing any data considered sensitive or “not for public release”. Any data attribute can be used for this purpose, even a simple manual flag or checkbox on the file within SharePoint.
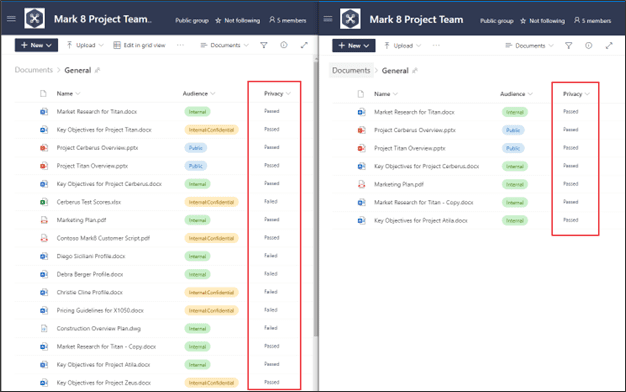
Further, NC Protect can limit the exfiltration of data by requiring that all data that Guests access must be viewed in the Secure Reader. The built-in Secure Reader has a lot of great features, including true ‘read-only’ access so that documents can only be viewed but can’t be copied, downloaded or printed. In addition, the Secure Reader can display an uneditable digital watermark of the user’s login details and date (as well as any other attribute or information label) within the document to discourage screen grabs of the data.
Redacting Sensitive Data
NC Protect can also redact data from documents in transit. For example, if a guest (or other user) needs to be able to access a specific document, however, it contains a credit card number that they are not authorized to see. Based on their guest attribute, it will automatically redact the credit card number and only show the portions of the document that the guest user is authorized to view. This allows guests to have access to sensitive documents without being able to see the portions of data that make it sensitive.
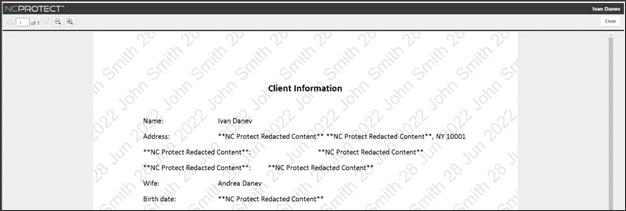
These are easy ways to limit what Guests can access, but NC Protect can also apply more granular rules to leverage other native Microsoft security features, including automatically applying encryption if the sharing scenario warrants it.
Auditing Guest Access and Activity in Microsoft 365
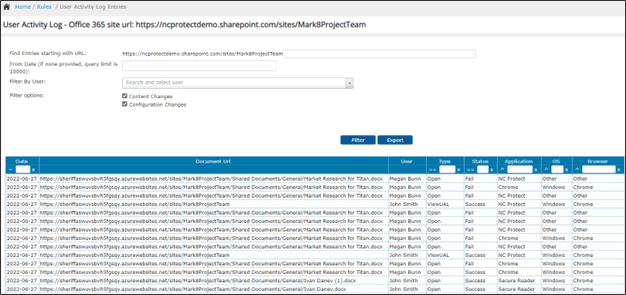
NC Protect also has the ability to verify that only the correct users are accessing the correct files. The Activity Log records all user activity related to data access and usage so that you have a complete audit trail to verify access or give to an auditor. The data is accessible via the User Activity Log in the NC Protect console or it can be imported into Microsoft Sentinel, Splunk or other SIEM solutions for data aggregation.
M365 Permission Mapping
Lastly, NC Protect has the ability to run a permissions Map Scan to determine who currently has access to your Files, Folders and Site Collections. You can sort the data however you wish and look for permissions by File or by user. In the example below, I’ve highlighted all Guest users (those within Azure that have the #EXT# tag) that have access to data.
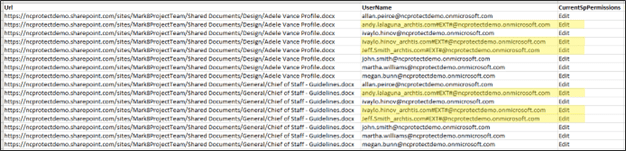
While NC Protect can limit or prevent Guests from accessing these files, this can be a useful audit step to determine how exposed your information is to Guests and what files and folders they have been given access to.
The Permissions Map Scan is a powerful tool to determine how widespread the permissions creep is throughout your organization. I have never looked in a client environment and seen a truly ‘clean’ and secure environment. It’s always an issue of “How bad is it?”
Summary
As users place documents in locations that they may or may not belong (sometimes accidentally, sometimes maliciously), the traditional security model quickly breaks down, and sensitive data becomes exposed. NC Protect’s data-centric model ensures that data stays protected no matter where it lives or travels.
Learn more or book a demo to see the power of NC Protect for M365 and SharePoint on-premises for yourself.


