What do you do when your IP is put at risk by your supply chain?
Data security policies are most often targeted around insider threats and external attackers, but your distributors can equally put intellectual property (IP) protection and other sensitive data at risk.
IP is arguably a business’s most valuable asset and can take the form of product designs, software code, media content, etc. Protecting your IP is important because it allows your business to maintain a competitive edge in the market and generate revenue from your innovation. Companies regularly take steps to protect their IP, such as securing their networks and applications, educating users on data security practices, and working with legal and compliance experts to develop and implement an effective IP strategy.
The risk of IP theft isn’t a new occurrence. Patents and copyrights were implemented more than 200 years ago to help protect intellectual property and the content creator’s rights. In the modern world, IP theft isn’t just used for capital gains and competitive advantages; in some recent cases it has been used to gain influence and ‘clout’. The recent data breach where a US National Guardsmen leaked classified information to his gaming group is a prime example of this.
When Supply Chain Cybersecurity is the Weakest Link in IP Protection
This was the problem that a manufacturing client encountered when they experienced several leaks over several months of upcoming product releases. Due to the nature of their products, there was a lot of public interest in future releases that fueled these ‘sneak peek’ motivated leaks.
Having worked in the manufacturing industry for decades, the client had an IP strategy to protect its own data from internal and external threats. As a result, they successfully adjusted during the pandemic lockdowns, when many of their employees were working from home and collaborating online in shared workspaces. However, their data protection policies had a gap — their distribution network.
When working with their supply chain partners, the client would inform them of new product releases in advance. These updates would allow retailers to plan for seasonal releases and allocate inventory space for the new products. This process involved setting up meetings and presentations that sometimes included images of the new product lines. This was where the problem with IP theft would often occur.
The client took steps to protect their IP internally by restricting access and implementing a strong zero trust access policy. These security steps were ineffective when it came to presentations when images of unreleased products are displayed on big screens in boardroom meetings or presented during teleconference calls.
During these meetings, an attendee would sometimes take a clandestine photo of the displayed image from their phone. The image would then be shared with friends or family via text message and WhatsApp. Inevitably, someone would post it online to share a ‘sneak peek’.
This put the client in a bind, as they had contractual obligations to share new products with their distributors. While these partners also had agreements in place not to redistribute materials and information shared in meetings, it was difficult to prove who, when, and where the leaked image was captured.
The Theft Deterrent Strength of Security Watermarks
The client began manually applying watermarks to the presentation file to deter photographing. This would require the presenter to manually update the watermark, and include the name of the presenter, the meeting details, date and time. This information would then have to be updated for each and every meeting and would need to be accurate to ensure the integrity of the identifying information. The problem with this process was twofold. One, it was considerably resource-heavy with two full-time employees dedicated to the manual watermarking process. Two, a simple mistake could mean the watermark information was incorrect or forgotten entirely.
archTIS was able to solve this challenge with dynamic security watermarks. With NC Protect once a watermarking policy has been enabled, it will dynamically pull the desired watermark attributes (both user and data values) and automatically apply them to the presentation file at the time of access. This means the watermark would be automatically updated for separate meetings at different times, and when shared by individual employees, visually marking the document with the user’s unique information each and every time it is access or shared.
The NC Protect applied security watermark contains all of the information required to identify the place and time of the meeting, and the presenter. In addition, individual images in the presentation can also be watermarked separately.
The ability to apply multiple watermarks to a document successfully deters photographs and data leakage. In the event of a leak, it allows investigators to quickly identify when the photo was captured and correlate this information with their audit logs. The legal team can then quietly remind the partner of their contractual obligations and the need to protect unreleased IP for the sake of all involved.
Automating the Application of Dynamic Security Watermarks to Protect IP
Security watermarks can be used in a range of industries to protect not just IP but other sensitive information including personal information, healthcare information, payment card data, classified data and more.
Applying dynamic security watermarks is a simple process with NC Protect. The security policies in NC Protect use both user and data attributes, also called attribute-based access control (ABAC). These policies can also be set up to not only apply watermarks but can also restrict what information an employee can access — and what they can do with the file once they have access.
For example, some possible use case scenarios and policies include:
- A catch-all rule that applies a customized watermark (e.g., user name, time, date, location) to all PowerPoint presentation files when opened from a specific location.
- Or the rule could be enhanced to include a condition that only applies the watermark to documents specifically tagged for watermarking.
- Or a third condition may be added that excludes the dynamic watermark appearing when internal editors and content owners are accessing the document from within the office. The staff creating and managing these presentations would only see the dynamic watermark if they were working away from the office.
NC Protect’s conditional ABAC policies ensure that your employees and authorized third parties only have appropriate access to the document under approved conditions. Watermarks can be applied to a variety of document types including Microsoft Office documents (Word, Excel, PowerPoint), text files (.txt), images (png, .jpg, .jpeg, .tif, .tiff, .bmp), CAD files (dgn, .dwf, .dwfx, .dwg, .dwt, .dxf, .ifc, .iges, .plt, .stl, .cff2) and PDF documents (.pdf).
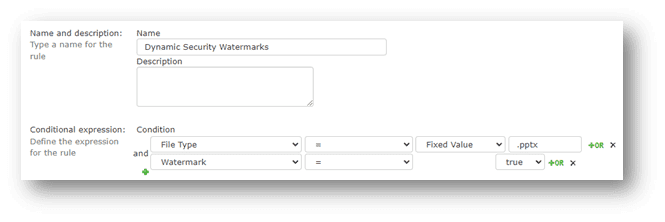
Above: Figure 1, Easy configure dynamic, conditional watermarking policies for multiple file formats.
The next step in creating a Dynamic Watermark policy is to design the custom watermark itself. NC Protect allows various watermark types, including the traditional full-page watermark (displayed at a 45-degree angle), Headers, Footers and ‘Stamps’, which can be positioned in a specific location in the document. For example, this is a requirement for Controlled Unclassified Information (CUI) designator indicator labels. Watermarks can also be applied to specific images in a file using the Tagged Images watermark type.
For added protection sensitive watermarked documents can also be displayed using the built-in Secure Reader. This provides true read-only access with no options to print, save, download, or copy/paste. If a user tries to bypass the security by taking a screen grab or photo on their phone the watermark is visible creating a digital thumbprint for forensic purposes.
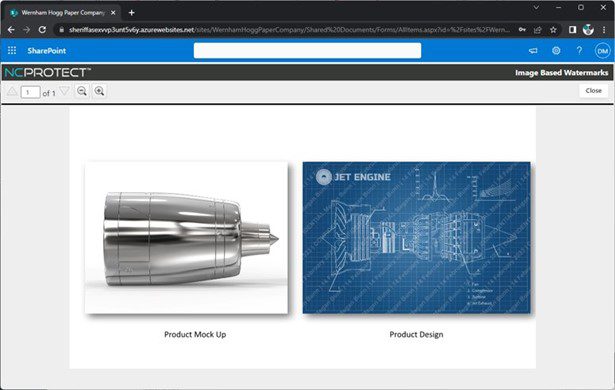
Above: Figure 2, A document displayed in NC Protect’s Secure Reader with only the sensitive image watermarked within the document.
Protect Supply Chain Cybersecurity & Collaboration with NC Protect
Enforcing a robust data security policy and automating data controls to protect your IP when used internally and when shared with contractors and partners is easy with NC Protect. The software is deployed in your own data environment, and it is an agentless solution that does not need any additional software on your end-point devices. It is device agnostic and will provide effective IP protection on Windows, Mac, Linux, Android and IOS devices.
NC Protect’s ABAC policies go far beyond dynamic security watermarking to provide effective control over data access and actions users can take with that data once access is granted. As Microsoft Intelligent Security Association (MISA) partner, NC Protect seamlessly integrates with Microsoft’s security technology to better protect sensitive data in Microsoft Office documents using Microsoft’s own Purview Information Protection security tools.
Contact us for a demo or to learn more about how we can help secure your IP and reduce the risk of unauthorized access and distribution across your Microsoft collaboration applications.