Information barriers that were once relegated to financial services and regulatory compliance are quickly becoming a must have to accommodate a variety of business scenarios. The art of running a business is a forever evolving path of goldmines and hurdles. Trying to map these business processes over current technology, is challenging at best and extremely difficult to achieve for all elements and viewpoints of business workflows.
Just when you believe that you have tamed the digital frontier, by implementing the best user role-based access controls to the various social channels, desktop SOE, financial systems, document repositories, payroll, and HR portals – an urgent request comes in for a “locked down private network” to securely share information to a select few on a need-to-know basis within and external to the business.
This request goes against the grain of your current IT methodology of simplification and consolidation of access controls. However, requests for data separation have become extremely common as business, and its associated communications web, become more global. ‘Information barriers’, also known as information walls, ethical barriers, exclusion/inclusion barriers, or cones of silence, are becoming an essential element of business to prevent the collaboration of material which may lead to conflict of interests or competitive advantage.
For example, an information barrier might be erected between parties (internal and external) that deal in mergers and acquisition, tendering, investments, and legal representation to name a few.
Have you already entered the matrix of policy management?
The act of applying information barriers to actively monitor and separate access to information from individuals or groups is not as simple as applying set and forget viewing (or non-view) rights in your user access management (role-based access control) system.
Traditionally information was held within “documents”; therefore, it could be controlled with a simple permissions toggle set on the file. With this permissions model, it’s difficult to maintain the effectiveness of information barriers, especially:
- If the “information” is held within collaboration tools.
- If you need to provide restrictions based on geo-location or nationality.
- If you need to apply multiple restrictive elements to the information barrier policies.
- If they need to provide “need to know or not” access to certain elements in the same folder or site collection.
- If your information barriers include personnel from outside of the organization (contractors, partners).
7 Use Cases for Information Barriers
Examples of everyday business information barriers are:
- Ensure users in a trader group do not communicate with other internal business groups.
- Stop finance personnel working on confidential company information from communicating with certain groups within their organization.
- Prevent an internal team with trade secret material from sharing files with people in certain groups within their organization.
- Limit a research team’s call or chat abilities with a product development team.
- Restrict collaboration between users in different geographical locations or subsidiaries to meet regulatory guidelines such as GDPR.
- Ensure files created by, for example, an SVP or higher are restricted to users at that level of the organizational hierarchy or above.
- Restrict the sharing of files via chat, based on file sensitivity.
Configuring an Information Barriers is not a one size fits all art form. Each and every industry, use case or regulatory requirement will have individual configurations – determined by the individual business circumstances, processes, and compliance requirements.
For example, in the legal world, there are a multitude of Information Barriers that need to be enabled. They may require top-down as well as side by side information barriers to ensure client information is segregated and contained on a need-to-know basis between sub-entities, legal practices, lawyers and external parties. Examples where legal information barriers are imperative include:
- When a lawyer moves from one legal practice to another
- A single law firm is acting on behalf of multiple clients in the same (or related) matter.
- When an attorney-client relationship ends
- Internal and external parties working on the same matter or internal project.
These information barriers screen individuals within an entity or group of users from any new/conflicting information that may introduce the possibility of confidential information being used inappropriately.
More effective information barriers consider document and user attributes, not just user roles
Whilst constructing these Information Barriers may seem easy enough to do using out-of-the-box (OOTB) tools, in reality, they often completely cut off all communications between these groups regardless of the scenario – hindering other work practices.
For example, if information barriers are set up between your traders and marketing teams, then your traders can’t receive any information from marketing because the information barrier policy specifies no communication is allowed between these two groups. The context of the communication isn’t considered; it simply creates a virtual wall between these two groups.
There are also often limits on the number of entities or groups that you can place information barriers between, which can be problematic in today’s global economy. The more entities/users there are, adds more complexity to managing information barriers using OOTB tools or role-based security models. Adding to this complexity is the requirement to add and remove internal entities, groups and external guests to these security models.
What if you had the choice of creating effective, flexible, and contextual information barriers for your existing Microsoft 365 environments? Imagine information barriers that enable you to successfully separate your data via granular Attribute-Based Access Controls (ABAC) policies that can dynamically determine if the specific data action should be allowed or restricted.
The trick to successfully implementing dynamic information barriers is leveraging content attributes (e.g. classification, sensitivity, author, site permissions, etc.) and user attributes (e.g. group permissions, security clearance, role, location, time, etc.) as part of the policy to block/allow access. Once the policies are defined, any new data or users that are introduced into the business processes are adopted by these conditions and secured accordingly.
As ABAC is a “do not trust – challenge everything” zero trust methodology, access is based on the attributes of the content (file, chat or message) and the user at that moment in time. When a policy (condition) is modified to include/exclude an attribute, at the next interaction between that user and content, the new governing policy will be invoked and applied. The same happens at the content level. If the attributes are changed, then a different set of access conditions may instantly apply.
BUILDING DYNAMIC INFORMATION BARRIERS IN MICROSOFT 365 WITH NC PROTECT
You can see the advantage of using an ABAC-centric solution to create flexible vs finite information barriers that stop all non-compliant communication and collaboration.
NC Protect is an advanced information protection solution built with ABAC controls to enable secure and dynamic security in Microsoft 365 applications (SharePoint Online, Office, Exchange) and other file shares. Create dynamic information barriers to meet your compliance and security requirements, with the following advantages:
- Blocks file access and sharing of restricted content, without stopping collaboration of approved content.
- Supports information barriers for one to multiple entities or groups, without limitation.
- Segments access to country-specific sensitive information in SharePoint Online without complex permissions, roles, folder hierarchies or site collections.
- Restricts in-application ribbon functionality for guest users.
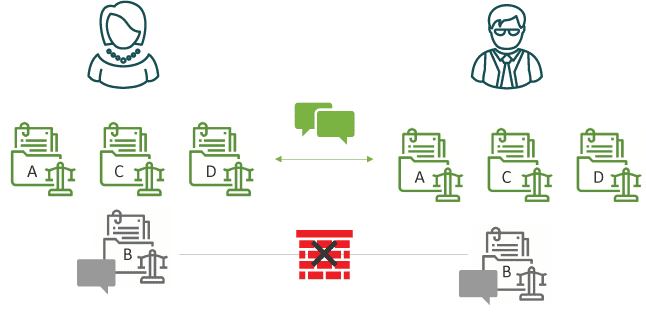
For example, take the scenario in the diagram below. A legal firm is using Microsoft SharePoint. Two of the firm’s attorneys are working on multiple cases that they need to collaborate on, but they are not allowed to communicate on case B, as there is a conflict of interest. NC Protect will allow conversations and file exchange on the other cases, but block any communication or file exchange on Case B.
Summary
If you are looking for a solution that will assist you in creating Information Barriers (cloud or on-premises) to block unauthorized communication but are flexible enough allow permitted topics within internal groups and external guest users, if required, then reach out to the team at archTIS.


