Encryption is an essential means of protecting sensitive information and is required for certain types of data under many regulations. As more companies move to the Cloud and introduce Microsoft 365 (M365) applications like SharePoint Online to their communication and collaboration channels, the potential for data getting into the wrong hands grows exponentially, making encryption strategies essential. Encryption key management in Microsoft 365 also poses a headache for many organizations moving to the Cloud. Learn how to improve encryption and key management processes in collaboration tools, including the Microsoft 365 suite.
Encryption Trends
The use of encryption has evolved over the past decade as organizations understand the benefits and privacy regulations that demand it. Adoption is growing as sweeping global regulations and data privacy laws have raised the stakes on data breaches and the standards for data protection. Despite this, even organizations with robust data security policies are still prone to accidental data loss or overexposure through simple human error.
Half of organizations in a recent survey are already leveraging encryption in their data environments, according to the 2021 Global Encryption Trends Study by the Ponemon Institute. However, 65% cited the ability to identify sensitive data in their environment as the biggest challenge to planning and executing a data encryption strategy. Respondents also indicated that key management (69%) and policy enforcement (68%) are the most important features they look for in an encryption solution.
How can organizations improve encryption and key management processes in collaboration tools, including the Microsoft 365 suite, to fit their compliance and security requirements?
What is Encryption?
Encryption is a common method for protecting sensitive information. It involves a process of encoding or scrambling the contents of a transmission or a file. The encryption is performed using an algorithm matched to a cryptographic key. The content can then be unscrambled or decrypted by an authorized device that uses a matching key. Anyone who attempts to read the file without decrypting it first will find the content is in an unreadable form.
Above: Example of encrypted text referred to as ciphertext.
When discussing encryption in data security, two approaches are often considered: encrypting data in transit and encrypting data at rest.
Data in transit is data that is sent from one location to another, such as across the internet or a wireless network. If unprotected, this data transmission can be exposed to an attacker that is connected to the same network. Data in transit is usually protected by secure encrypted protocols, such as HTTPS, SSL, TLS, etc.
Data at rest is the information stored or archived on our devices, company servers and in cloud storage tools. An attacker will often find data at rest a more valuable target. They do not need to capture the information as it is transmitted but can hack into and explore a vulnerable system and extract unprotected data with ease.
What are Encryption Key Management and BYOK?
Encryption key management is simply the process of managing the encryption keys used to encrypt and decrypt data. Securing encryption keys is critical to any enterprise that uses encryption as a part of its security strategy. This is vital when the encryption keys are hosted with a cloud service provider, such as Azure or AWS, because the keys reside with the provider—not the data owner. Bring Your Own Key (BYOK) encryption management systems allow organizations to manage their own encryption keys.
BYOK allows for unique encryption keys to be generated and assigned to encryption solutions. These managed keys can then be assigned expiry dates and deleted when they are no longer needed. This will guarantee that data encrypted with an expired or erased key is secured and inaccessible, no matter who holds a copy of the file.
It is important to note that some BYOK systems still upload the encryption keys to a cloud service provider. For an enterprise that requires absolute control of its keys, a hardware security module (HSM) should be considered. An HSM is a physical device that provides additional security for encryption solutions. The HSM is usually hosted on an enterprise’s own infrastructure, where it holds the master key that is used to provision and manage other cryptographic keys. This approach allows an enterprise to encrypt its data and retain full control and management of its keys.
With an encryption key management solution like BYOK or an HSM, an organization will have much more control over its protected data. If an organization was to lose access to its sensitive files, then the encrypted content would still be protected and not accessible without the appropriate key.
Enhancing Encryption and Key Management in Microsoft 365 and SharePoint
Adding dynamic encryption to content stored and shared via on-premises and Cloud collaboration tools such as SharePoint and M365 provides essential protection to ensure sensitive data is protected in accordance with both regulatory and business policies.
NC Protect is a key tool in any organization’s security and compliance toolbox for identifying and protecting Microsoft 365 (M365) and SharePoint data. It helps to address the challenge of identifying sensitive data – a leading challenge for companies trying to implement an encryption strategy – as well as dynamically encrypting sensitive data.
NC Protect can be used to locate and classify all sensitive and confidential data (personally identifiable information (PII), healthcare data (PHI), intellectual property (IP), HR data, Board docs, contracts, etc.) in your Microsoft suite of on-premises, cloud or hybrid environments. While dynamic classification and access control are NC Protect’s first line of defense, if a sensitive document that requires encryption is identified, it can encrypt the content immediately – limiting the audience to only credentialed users. In addition, the contents of an email and any attachments sent through Exchange can also be encrypted automatically with NC Protect.
NC Protect keeps data protected no matter where it is stored or travels: in motion and at rest.
How Does Encryption Work With NC Protect?
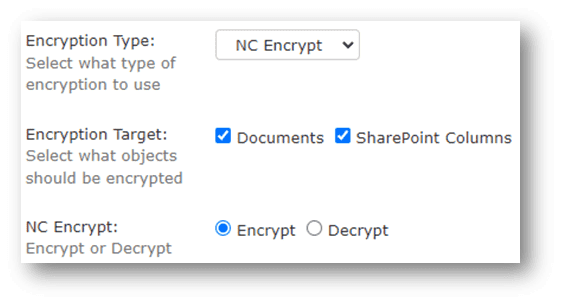
Out-of-the-box NC Protect extends the value of Microsoft Purview Information Protection (MPIP) and RMS controls. In addition to encrypting data at rest and sensitive document libraries, NC Protect can also encrypt SharePoint column values, ensuring greater protection of SharePoint lists and metadata. In addition, NC Protect manages both access and encryption policies across all Microsoft 365 (SharePoint Online, Exchange, Office), SharePoint Server, and/or hybrid environments from a single application to reduce complexity and streamline data security policy management.
An example of how this might work in practice could be an organization that has a collaborative workspace that is shared between several departments. Documents uploaded into this workspace are generally safe to be seen by all users that have access. But what happens if a user accidentally drops a document into this space that contains highly sensitive or personal information? With NC Protect, you can ensure that several checks are applied to the document, and it can be automatically encrypted to protect against unauthorized access to ensure sensitive content is protected.
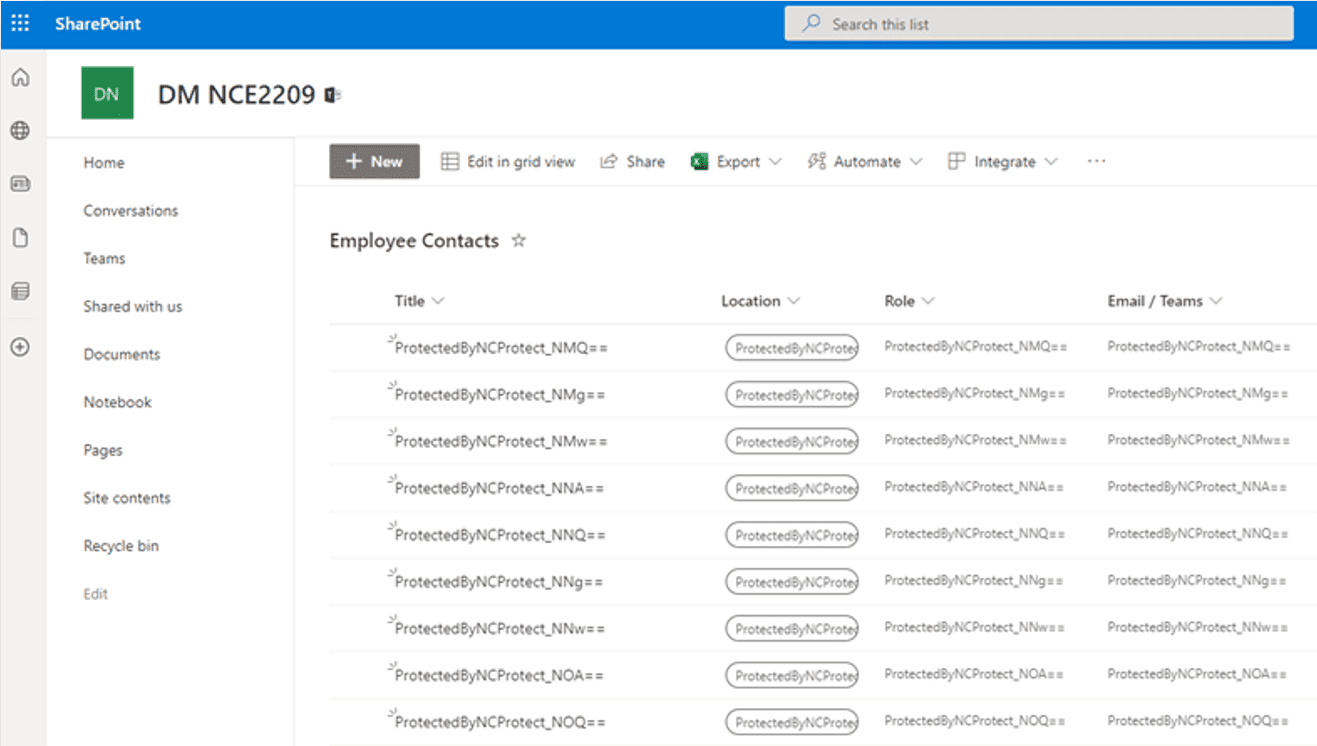
Above and below: NC Protect can encrypt sensitive content in M365 applications and SharePoint on-premises, as well as SharePoint columns and lists (Online & On-Premises).
How does NC Encrypt Provide Independent Encryption Key Management for Microsoft 365 and SharePoint?
NC Encrypt is an optional module for NC Protect that provides additional capabilities for organizations that want to manage their own encryption keys. When encrypting your data with Microsoft’s MPIP protection, it is important to realize that your encryption keys are hosted with Azure. If you were to ever lose control of your keys, then a third party could gain access to your data. NC Encrypt’s independent Microsoft encryption key management ensures that you remain in full control of your own keys by applying BYOK support and key retention management.
Organizations can use NC Encrypt to dynamically generate their encryption keys or import and use their own via connectors to third party key management platforms. This includes integrating with key management solutions using the Thales CipherTrust Manager. Customers can easily leverage their existing encryption investments and add FIPS 140-2 certified third-party Hardware Security Modules (HSMs).
Learn more about encryption and key management for Microsoft 365 using NC Encrypt.