There are many ways to share data in SharePoint, including lists. A SharePoint list is a collection of data that a user can share with other users to whom they have permitted access. A variety of default list templates are provided in SharePoint to allow for easier set-up. Users can also import such lists (usually in CSV format) from other applications. As with any other method of sharing data, controlling access to SharePoint lists is crucial to security – especially if the information is sensitive. While there is SharePoint list security out of the box, encrypting SharePoint lists is not possible. Read on for tips on managing access to and encrypting SharePoint List Columns to prevent unauthorized viewing of and access to sensitive column values.
Default SharePoint List Security
List security in SharePoint is tightly coupled with permissions. By default, all SharePoint sites, lists, and libraries in a site collection inherit their permissions settings from the site that is directly above them in the hierarchy.
- List owners and administrators can assign and take away permissions.
- Everything inside a specific list inherits all of its permissions from the site that contains them (if not specified otherwise).
- You can’t break or reinstate permission inheritance for a list with over 100,000 items in it.
The core process of assigning unique permission to lists is quite simple and usually consists of two steps:
- Breaking permission inheritance for that list.
- Assigning unique permissions to the list.
Inheritance breaking is an uncomplicated process. If you’re already on the Permissions page (per the instructions above), then choose the Stop Inheriting Permissions option.
As soon as you’ve broken the inheritance permissions for the list, you are free to assign your own permissions to the list in question. This can be done from the same Permissions tab, using another button titled Grant Permissions (this option may not be visible if the inheritance rules are still in place). You’ll have several options in the following window, including:
- Invite people option with the ability to specify who would have access to this list.
- Change the permission level of the entire list, from the default Edit one to other ones, like Read, Contribute, etc.
- The ability to send an email notification to everyone in the Invite people box, and more.
You can also change the permission levels of the list for specific groups. You’ll have to go to the Permissions tab once more, choose the group in question and use the Edit User Permission option to change their permissions. The permission range can be freely changed to a variety of levels and use cases, from Full Control to View Only and everything in between.
Encrypting SharePoint List Columns for Better Security
What about encrypting a SharePoint list column value? For example, perhaps the list contains company servers and passwords, or there is a personnel list containing personally identifiable information (PII). Other potential columns values you may want to encrypt include Document Name/Title, Descriptions, or Tags that may contain:
- Confidential personal information such as First/Last Names, DOB and/or Addresses
- Intellectual property or company confidential information
- Sensitivity or classification level of military or government documents
Unfortunately, SharePoint does not provide field-level security or the ability to encrypt lists and column values. You are limited to restricting access at the list or complete item level.
Trying to build the customization to accomplish this can be cumbersome. If you require column encryption and granular item-level access then consider adding a third party tool like NC Protect paired with NC Encrypt. Together they not only allow you to restrict access at the item level — but also dynamically encrypt SharePoint list columns values and files based on predefined policies.
NC Encrypt’s agentless design means there’s no administrative overhead. There are no encryption keys or passwords that need to be shared with end users or endpoints. No software to be installed and maintained or endpoint policies to update.
Sharing rules can be configured to apply and remove encryption at rest for both documents and column values. Since NC Encrypt policies are based on attributes you can apply fine-grain access controls based on the user, sensitivity level of the content, user location, device and other custom factors. You’re not just limited to controlling who can see decrypted values based on roles or the location of the list. In fact, administrators can also be prevented from seeing sensitive list information while still being able to perform administrative tasks.
NC Encrypt is a seamless solution that doesn’t require users to change how they work to ensure sensitive data is properly encrypted.
CONFIGURING SHAREPOINT LIST COLUMN ENCRYPTION
The process of encrypting SharePoint list column values is easy to do in the platform’s central policy manager where the access and protection policies for both NC Protect and NC Encrypt are configured.
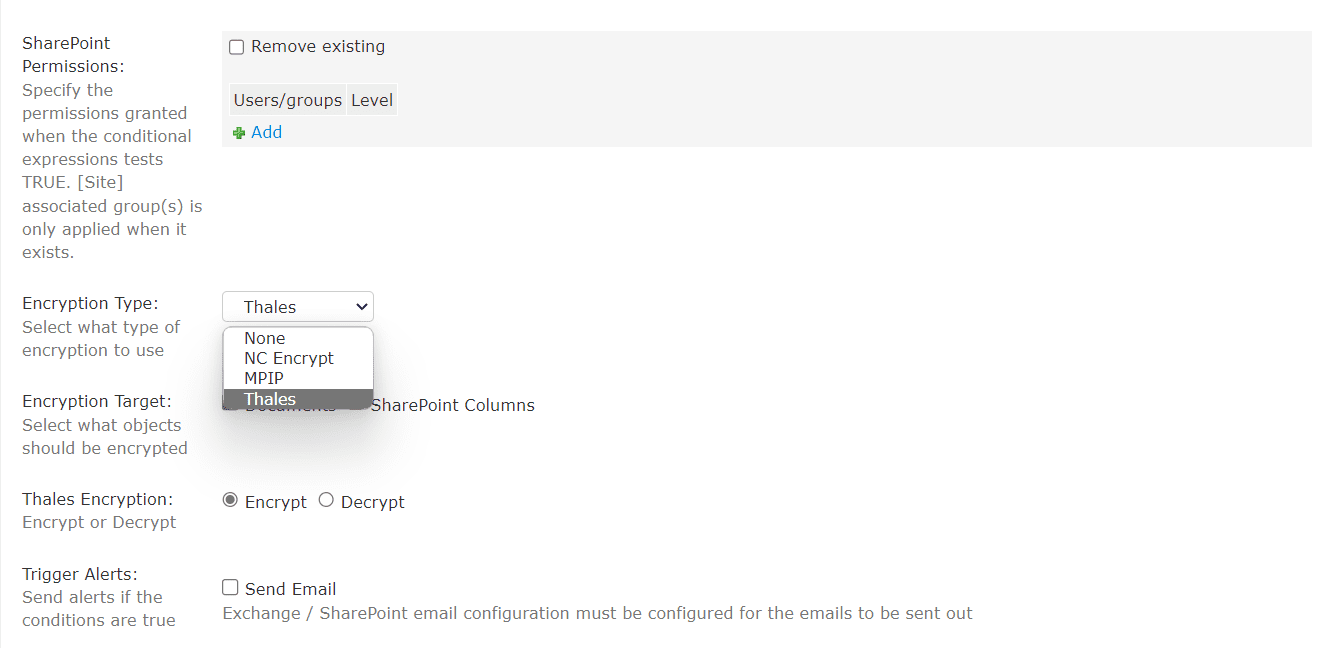
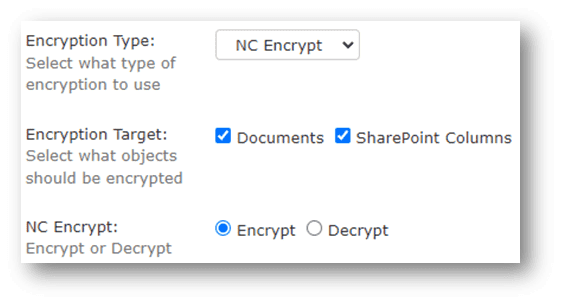
First, select the encryption type (MPIP, NC Encrypt, or Thales CipherTrust Manager) and the target object you want to encrypt: Documents, Columns, or both as seen in the screenshot below.
Then select the Encryption Target: Documents, SharePoint Columns, or Both.
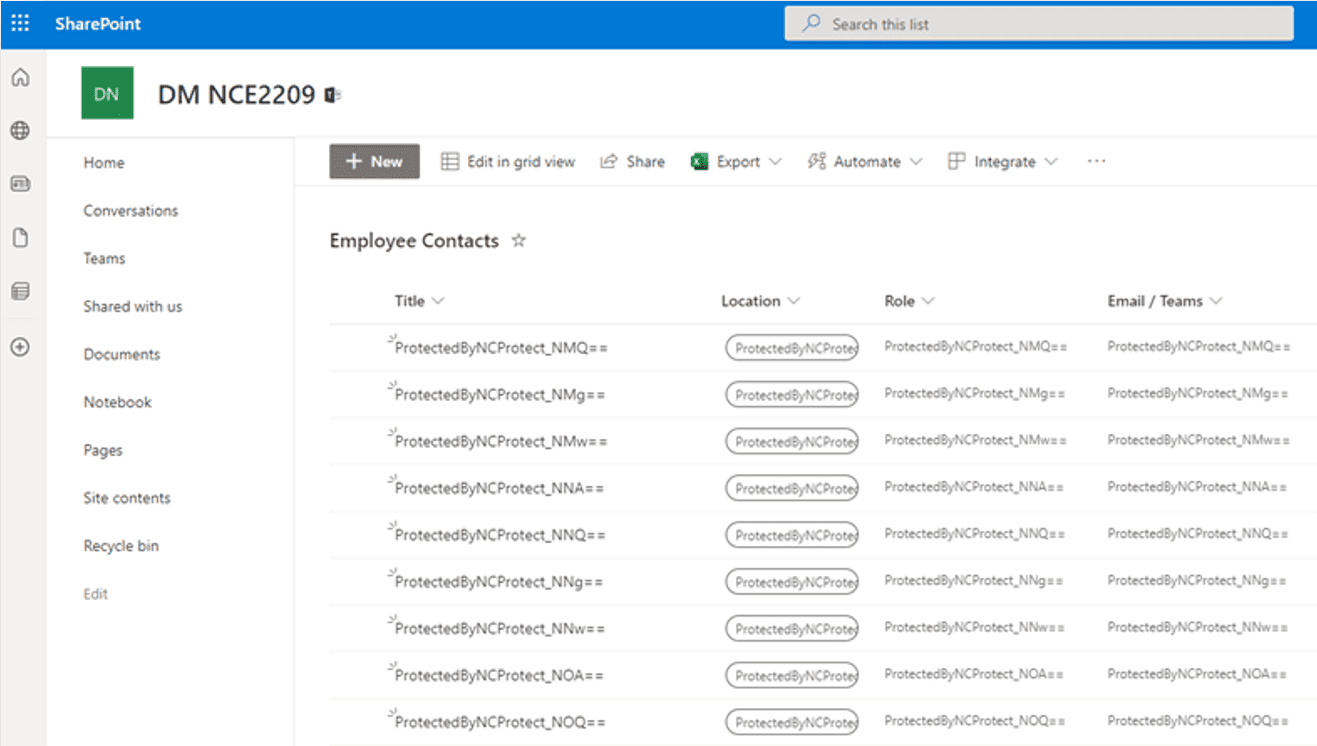
Once the policy is activated, SharePoint List columns values will be encrypted accordingly as in the example below.
Enhance SharePoint security with granular data protection
SharePoint list encryption is one of the many advantages of adding the NC Protect suite to your SharePoint Online or On-Premises environment to further enhance security with unique capabilities to:
- Control access rights to encrypted content.
- Restrict the visibility of column values in SharePoint lists.
- Add independent encryption key management.
- Bring Your Own Keys (BYOK) using connectors to HSM platforms.
- Force Secure read-only access to sensitive content.
- Restrict duplication (copy/save as/download) and file sharing functions
- Apply dynamic watermarks that contain user attributes (e.g., name, date, IP) to encrypted file types including Microsoft Office, PDF, CAD and text-based files, as well as images.
If you’re looking for an easy way to dynamically encrypt SharePoint list values, support BYOK and manage sensitive data access across your Microsoft suite of products, contact us to learn more.