In the IT and information security world, the need for Information Barriers or Ethical Walls is becoming more prevalent with the explosion of collaboration tools — in particular, Microsoft 365. The term has quickly grown beyond its origins in financial services to encompass any policies designed to prevent certain segments of users from communicating with each other or to allow specific segments to communicate only with other specific segments. Despite the availability native Microsoft tools to address these needs, in practice they are very finite and don’t allow for collaboration outside of these groups. In this blog we explore the uses cases for information barriers, and how to design them to restrict specific collaboration, but with enough flexibility to allow other types of communication.
Origins of and Business Applications for Information Barriers
Traditionally an “Information Barrier” is a term used in finance for a system of controls and monitoring including, but not limited to, physical segregation of employees and restrictions on access to and flow of information to ensure that:
- Information relating to the Group and the Finance Documents (and related transactions) is not disclosed to any person who is or who is acting on behalf of either a Competitor or an investor or equity holder in a Competitor or who is engaged in any M&A or other advisory activity in relation to or on behalf of a Competitor; and
- Information available to any team or employee who is or who is acting on behalf of either a Competitor or an investor or equity holder in a Competitor or who is engaged in any M&A or other advisory activity in relation to a Competitor is not disclosed to any team or employee acting in relation to the Group or the Finance Documents (and related transactions).
Collaboration tools have quickly expanded the need for restricting collaboration of other types of information between individual or groups of individuals including but not limited to intellectual property (IP), regulated data including personally identifiable information and healthcare information (PHI), and more.
For example, information barrier policies can be used for everyday collaboration scenarios like these:
- Ensure financial or confidential company information cannot be accessed or shared with certain groups within their organization.
- Prevent employees in different geographical locations or subsidiaries from accessing specific data for compliance with privacy regulations such as GDPR.
- Ensure files created by, for example, an SVP or higher are restricted to users at that level of the organizational hierarchy or above.
Get Flexible Information Barriers Using Third Party Tools
Flexible information barriers are essential for productivity and ensuring you get the most out of your Microsoft investments. Fortunately, third party tools provide an affordable option for organizations that want the information barriers without having to create separate sites and other complex mechanisms to limit access by certain parties. NC Protect provides capabilities for the configuration and enforcement of information barriers within their Microsoft environment.
It provides the following add-on capabilities using the Microsoft investments and classifications already in place to:
- Control file access and sharing in line with business rules for users from different operating companies or geographical regions beyond sole reliance on permissions.
- Restrict access to files without complex permissions or multiple sites using dynamic attribute-based access control (ABAC) policies to control .
- Automatically secure access to content based on the creator of that content e.g. files created by an SVP or higher is restricted to users at that level of the organizational hierarchy or above.
- Provide the data governance needed to control External/Guest access to files.
Configuring Flexible Information Barriers Policies with NC Protect
Configuring Information Barriers within NC Protect is as simple as building out the conditions with which you want to control collaboration. NC Protect can use any data or user attribute as part of the condition that blocks chat messages or file attachments.
A common use case is to prevent two groups of users from sharing files. Simply map out the use case in the condition builder. The example in the image below prevents Con_Mobile and Toso_Telecom from sharing files via email.
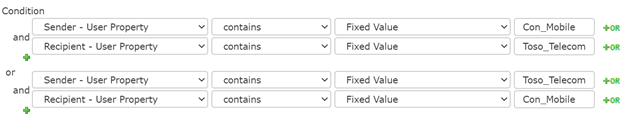
Unlike other solutions NC Protect considers users in the context of both the sender and recipient as part of the condition. This allows greater flexibility to control the communication that is possible e.g. one-way “broadcast” messages can be sent or additional controls can be placed on one group e.g. allow HR to send files with PII to users but prevent others from doing so.
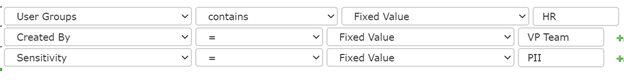
In addition, NC Protect rules and protection can also be applied at a more granular or scenario based level. Information Barriers that are too restrictive can severely restrict an organizations ability to work together. NC Protect’s real-time conditional policies allows barriers to be tailored to the exact needs of the organization, providing protection that truly meet business and compliance needs.
See it for Yourself
Information Barriers don’t have to be finite. Contact us to see how to create Information Barriers for M365 that support real world collaboration needs.


