by Irena Mroz | Jan 26, 2022 | Videos
NC Protect Automates Classification & Compliance See how NC Protect’s dynamic classification and protection capabilities ensure compliance and secure sharing. Request a Demo

by Irena Mroz | Jan 26, 2022 | Videos
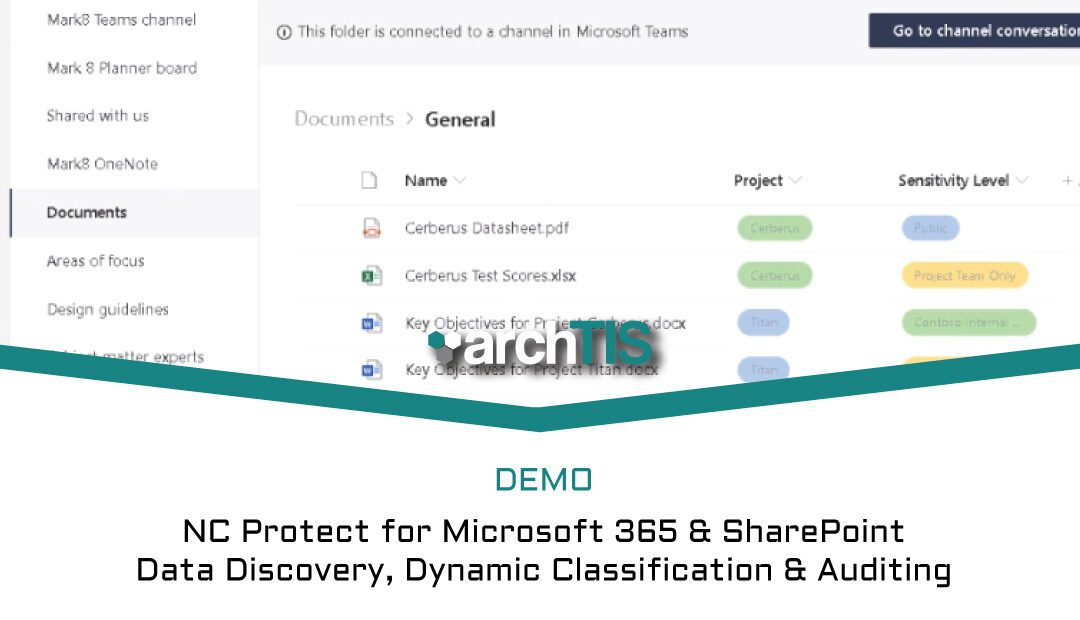
NC Protect for M365 and SharePoint See NC Protect’s dynamic and unique data protection features to ensure secure collaboration, sharing and info barriers across M365 apps. Request a Demo

by Irena Mroz | Jan 19, 2022 | Blog
In a world of hybrid, on-premises and cloud enterprise IT solutions, global communications and data regulations (i.e., PII, GDPR) that stipulate what information can be shared in which situation, organizations around the world need effective data loss prevention (DLP)...

by Irena Mroz | Jan 13, 2022 | Blog
The world has changed and along with it the strategic role of information security Now more than ever, the Boardroom, Chief Executive Officer and Chief Information Officer have Information Security front of mind and keeping them awake. Every day a new attack, incident...

by Irena Mroz | Jan 5, 2022 | Blog
Companies are reporting sharp increases in data loss spurred by remote and hybrid work. How is this occurring with all the security measures and tools enterprises have in place? Insider privilege abuse and data mishandling are cited in multiple reports as growing...