by Irena Mroz | Jan 2, 2020 | Blog
2019 was the year of the Insider Threat – and they are sure to continue to compromise organizations in 2020. The Cybersecurity Insiders 2019 Insider Threat Report revealed that 70% of organizations surveyed reported they saw in increase in see insider attacks in...

by Irena Mroz | Nov 13, 2019 | Blog
This post by Nucleus Cyber’s Steven Marsh originally appear in Dark Reading Pull a Van Helsing on those sucking the lifeblood from your data and intellectual property. Vampires do exist — in the workplace, that is. They bleed your company of customer data,...

by Irena Mroz | Oct 24, 2019 | Blog
It’s a familiar tale. Boy meets girl. Boy tries to impress girl with secrets from his government job. Boy steals confidential files from his job as a counterintelligence analyst at the Defense Intelligence Agency (DIA) to give to his journalist girlfriend to boost her...

by Irena Mroz | Apr 4, 2019 | Blog
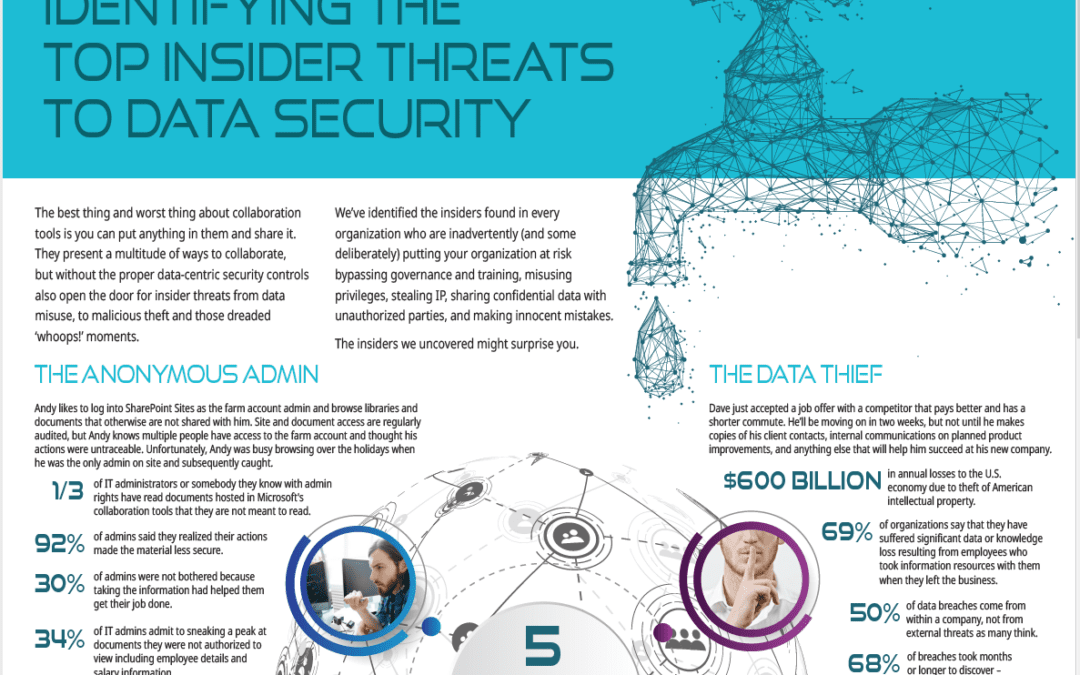
Identifying the Top Insider Threats to Data Security Last week we unveiled one of the characters in our new Infographic, The Anonymous Admin. This week we look at 2 other insiders from the Infographic found in every organization who are inadvertently (and some...

by Irena Mroz | Mar 27, 2019 | Blog
Identifying The Top Insider Threats to Data Security The best thing and worst thing about collaboration tools is you can put anything in them and share it. They present a multitude of ways to collaborate, but without the proper data-centric security controls also open...