While the data breaches that make the headlines often focus on personal data, there’s a lot more at stake if a hacker cracks open the gates. There’s even higher stakes when intellectual property (IP) theft is the goal potentially stripping away an organization’s competitive advantage. It’s not just hackers that are a threat to IP. Employees, contractors and partners all pose a risk to IP from accidental or deliberate data loss. IP comes in many common forms, such as documents and spreadsheets, but images and CAD files pose just as big a risk and are more difficult to protect with traditional security tools. Today’s technical spotlight covers how to protect and watermark CAD Files to help prevent data loss and IP theft and meet Defense compliance requirements such as CMMC.
What are CAD Files?
If you’re not familiar with them, computer-aided design (CAD) files are used for designing models or architecture plans in a 2D or 3D rendering. CAD files are used for creating architectural designs, building plans, floor plans, electrical schematics, mechanical drawings, technical drawings, blueprints, or for special effects in movies. They are used by every organization related to any type of manufacturing or construction, including those who manufacture tools and equipment for other manufacturers.
2D CAD files are drawings that mimic ‘old school’ drafting work. Most often these still exist as blueprints for structures where the height isn’t as critical for the design or is a standard dimension, however the layout within that 2-dimensional space is critical. For example, how do we fit our desks, chairs, tables, etc., into that space? The problem with portraying complicated 3-dimensional objects like machine parts in only 2 dimensions is that they need to be rendered from multiple angles so that all critical dimensions are portrayed properly. This used to result in a lot of drawings of the same part, but from different angles.
3D files on the other hand can be portrayed in 3 dimensions and can be rotated in space and even ‘assembled’ with other parts. This can help Engineers discover issues (such as a pipe or shaft that has been accidentally routed through another part) much more quickly so they can be resolved long before production begins.
Much like image files, there are several types of CAD file extensions (.DWG, .DXF, .DGN, .STL) and the file type is dependent on the brand of software used to create them.
Why are CAD Files Challenging to Classify and Protect?
Since most CAD files contain intellectual property or IP, protecting them is critical to protect competitive advantage, avoid malicious theft/corporate espionage and stop sharing with unauthorized audiences. Depending on the industry, different regulations and protection policies may also need to be applied to protect CAD files. For example, in the defense industry, file that contain controlled unclassified information (CUI) must be classified and labelled as CUI under CMMC 2.0, NIST 800-17, and NIST 800-53 regulations.
Out of the box tools are often limited in their ability to classify and tag CAD files to meet the stringent requirements. Additionally, CAD files are often shared and collaborated on using file shares or even file sharing and collaboration tools like SharePoint, and Teams. Without the ability to properly classify and tag information Defense suppliers are at risk of losing valuable Government and Defense contracts to accidental sharing or malicious users.
5 Tips to Protect CAD Files
Protecting CAD files is no different to protecting any other sensitive documents in your care. We recommend you:
- Identify Sensitive CAD Files – The first step to any data protection strategy is knowing where your sensitive CAD files exist. If you don’t, you should consider using a scanning tool to find any files and apply appropriate protections.
- Restrict Access – Ensure only users and partners who require access sensitive CAD are authorized to do so. Then follow tip #3.
- Restrict Actions Authorized Users Can Take – Just because a user should be able to access a document, should they have carte blanche? For example, should they be able to edit it, download it or share it? Should they be able to access it on a public Wi-Fi or at an airport? You need to be able to apply fine grain access and usage controls to prevent data misuse and loss.
- Digitally Watermark files to provide a visual reminder of the sensitivity level of files and add information about the user for tracking purposes in the event of a leak. For Defense applications you’ll want to add CUI markings to your watermark such as a CUI Designation Indicator.
- Track Access – Keep an audit log of access and actions authorized users have taken with sensitive CAD files (print, save, download, email, etc.) and have a process in place to identify any suspicious activity (multiple downloads, access in the middle of the night, from a suspicious IP address, etc.).
Classify, Protect, Encrypt and Watermark CAD Files with NC Protect
NC Protect provides advanced data-centric security across Microsoft applications to enhance information protection for cloud, on-premises and hybrid environments. The platform empowers enterprises to automatically find, classify and secure sensitive data, and determine how it can be accessed, used and shared with granular control using attribute-based access control (ABAC) and security policies.
NC Protect offers a range of unique capabilities to restrict access to, protect and watermark CAD files, as well as other documents, in Microsoft’s document management and collaboration application. Capabilities include:
- Classification
- NC Protect automatically applies Microsoft Information Protection (MIP) sensitivity labels based on the contents of the file.
- Apply additional meta data or classification as required. For example, tag files as CUI.
- Encryption
- NC Protect leverages Microsoft Information Protection (MIP) sensitivity labels and Rights Management System (RMS) to encrypt CAD and other files.
- Encrypt files at rest or in motion (e.g., email attachments)
- Watermarking
- Watermark CAD files with any attributes such as user name, date, time, etc. to deter photographing and remind users of the sensitivity of the file.
- Automatically embed CUI Designator data into a 2D or 3 D CAD file as a secure digital watermark including: Name, Controlled BY, Category, Distribution/Limited Dissemination Control, and POC.
- Add CUI designator markings.
- Restrict Access & Actions
- Protected CAD files can only be opened and modified by authorized users based on predefined policies.
- Force read-only access for internal and guest users with a built-in Secure Viewer to prevent Copy, Paste, Print, Save As and Download capabilities.
- Policies can also control if and who protected CAD files can be shared with.
- Hide sensitive CAD files from the document view of unauthorized users in file sharing applications.
- Tracking
- Track access to all protected files as well as actions users have taken with the file.
- Export user actions and logs to Microsoft Sentinel, Splunk or a CSV file for further analysis and upstream actions.
- Supported Platforms & File types:
- Protects CAD file across all Microsoft 365 applications: SharePoint, Teams, Exchange email, Office 365, as well as SharePoint Server and Windows file shares.
- NC Protect supports multiple CAD file formats including: .dgn, .dwf, .dwfx, .dwg, .dwt, .dxf, .ifc, .iges, .plt, .stl, and .cff2.
Easy to Configure Access, Protection and Watermark Polices
Applying these policies and controls with NC Protect is easy to do using the built-in policy builder.
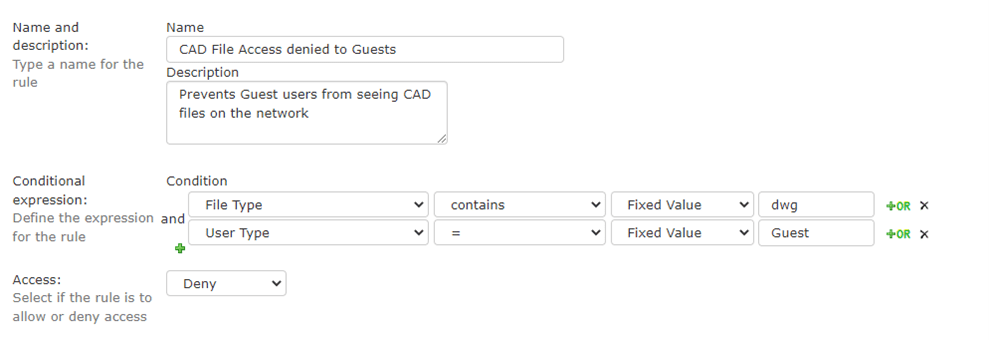
The policy below allows NC Protect to deny any guests users the ability to see that CAD files even exist within the network. With this policy activated, a guest will not see a dwg file – even if it resides in a container or Team that they have full access to. Consider how easy it is to share access to SharePoint and Teams with external users and how critical collaboration with external vendors can be for the business. I have often seen users place sensitive data into places that they don’t realize are accessible by people outside of the organization. This type of policy allows NC Protect to apply a blanket restriction on guests and mitigate the potential loss of sensitive intellectual property.
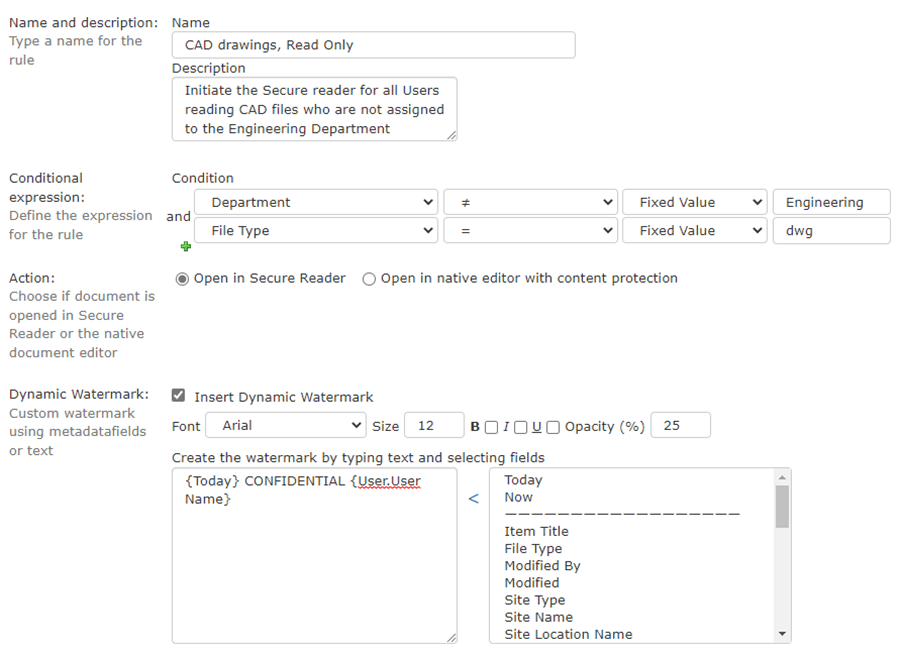
Going a step further, the policy below forces any users who are not part of the Engineering Department to be limited to read only access to CAD files. Even if a user is part of an Engineering group that gives them access to these files, if their department is not Engineering NC Protect will automatically invoke the Secure Reader when they try to open them. In this case we’re using the department attribute, but NC Protect can use any attribute such as existing group memberships, their title or any custom attribute to determine how users can interact with these files.
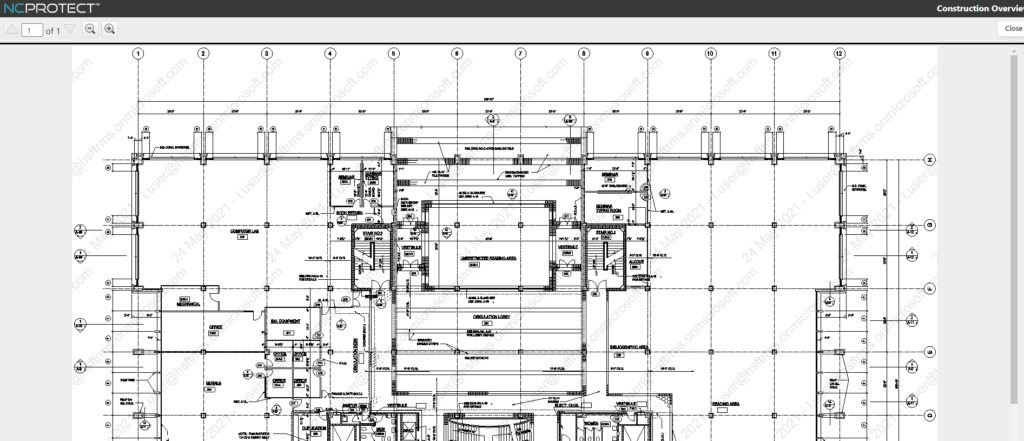
The built-in Secure Reader enforces ‘true read only’ access. Users can’t download, copy or even print a protected file. NC Protect even watermarks the CAD file so if a user screenshots the drawing, the photo will contain their name, date and ‘CONFIDENTIAL’ as seen in the image below.
Schedule a Demo
Need help protecting CAD files? Contact us to set-up a demo of NC Protect’s capabilities to secure your CAD files and other business-critical documents across Microsoft 365 apps, Share Point Server and other file sharing applications.