With the abundance of compliance requirements that organizations must comply with, such as HIPAA, PCI and GDPR to name a few, there is an increasing need for organizations to properly classify sensitive data and safeguard it accordingly. Defence contractors have additional data protection obligations under mandates such as CMMC, ITAR, DFARS and NIST 800-171. Identifying and classifying sensitive data is a crucial initial step in any organization’s compliance journey. Once that step is complete, you also need to implement security measures to control access to it and ensure it’s being used and shared in accordance with regulations to meet compliance obligations.
What makes NC Protect unique is its ability to protect data based on its classification, rather than just reporting on its location or attempting to move it to a quarantine folder. Read on to explore NC Protect’s capabilities for classifying, securing access to and protecting sensitive data can assist you in your compliance journey.
Classification is an Essential First Step for Compliance
NC Protect offers the ability to classify data using its own methods, making it an essential tool for organizations beginning their classification journey. However, many organizations have already invested in existing Data Discovery and Classification solutions and may be reluctant to disrupt their established processes. This is where NC Protect excels.
Bring Your Own Classification
NC Protect specializes in safeguarding sensitive data through attribute-based access control (ABAC) and data protection policies. It can leverage existing classifications from third-party tools, such as Microsoft Purview Information Protection sensitivity labels, ISEC, Janusseal, and others, as well as user attributes from Entra ID and other identity applications in its dynamic attribute-based policies. These policies dynamically control access and apply data-centric protection to files. It integrates seamlessly with collaboration tools in Microsoft 365, GCC High, SharePoint on-premises and file shares.
Step 2, Protecting Sensitive Data After it’s Classified
Here are some practical use cases for leveraging NC Protect’s advanced capabilities to protect sensitive data based on its classification and other relevant factors using data-centric, attribute-based security.
1. Control Access to Sensitive Data
NC Protect’s real-time attribute-based access control (ABAC) policies can restrict access to files based on the policy, file’s classification and user attributes to protect sensitive information against accidental and malicious data loss and misuse. Dynamically control how sensitive information can be used and shared based on the file’s classification, user and environmental attributes at the time of access.
For example, is the user on the corporate network or public Wi-Fi? With whom is it being shared? With NC Protect, access and sharing can be automatically approved or denied based on the context of the request as files move between people and locations.
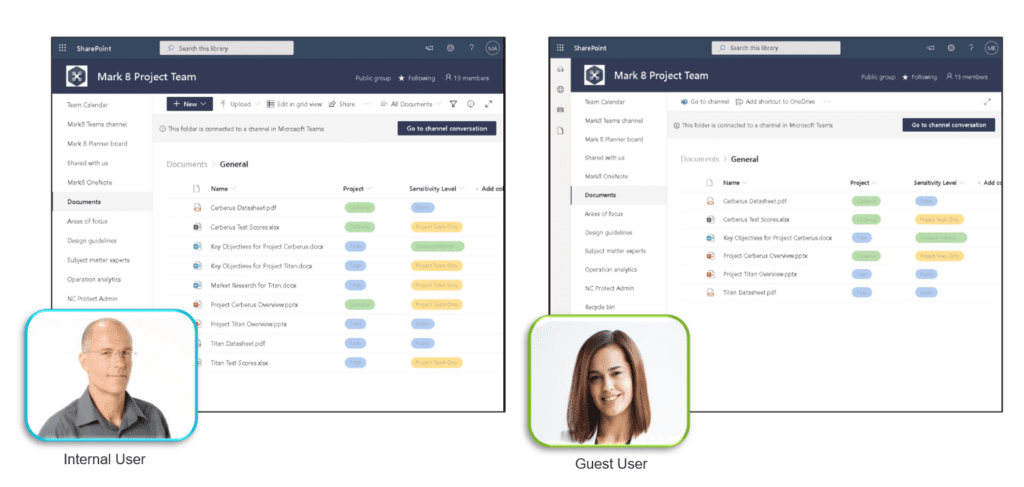
2. Hide Files from Unauthorized Users
NC Protect can obfuscate or hide sensitive files based on their classification and the user’s attributes. Unauthorized users won’t be able to see that those files exist, even if they have full access to the Folder or Site Collection where the data resides.
For example, NC Protect can mitigate the classic mistake of saving a sensitive file to a public directory, such as an HR file. Simple rules can be defined to prevent anyone who isn’t part of the HR department and/or who doesn’t have ‘Manager’ or ‘Director’ in their title from seeing that particular file, even if it is accidentally placed in a public folder.
This is also a useful capability for controlling Guest Access. NC Protect can enforce rules to prevent Guest users from seeing or interacting with any type of sensitive data in your environment. This is a key concern for many companies when enabling Guest Access.
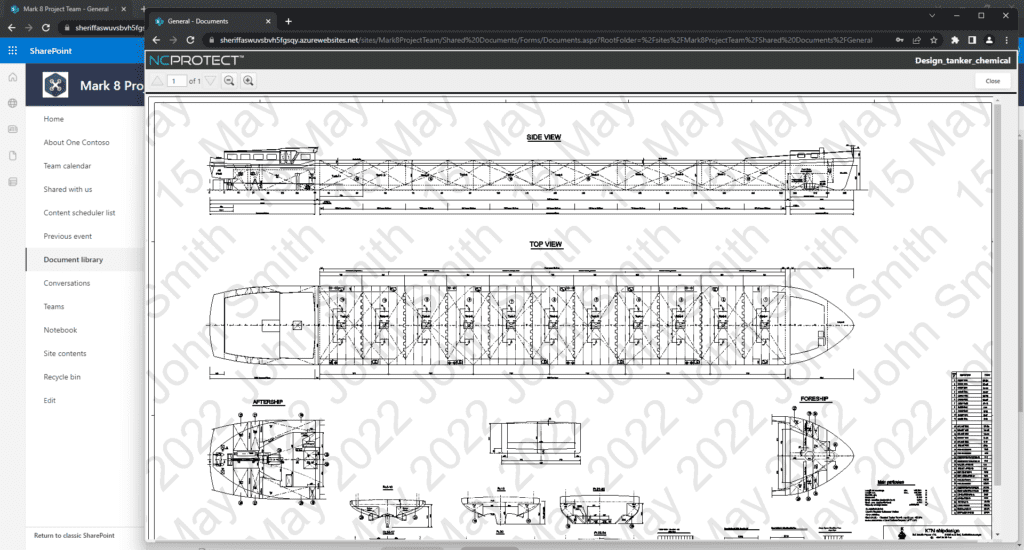
3. Apply Dynamic Watermarks
In addition to obfuscating files, NC Protect can add dynamic security watermarks that contain any variables, such as the user’s name and the date, along with any other relevant data to make screen grabbing of sensitive data more challenging. Watermarks can be applied in the native editing application (e.g., Word, Excel, PowerPoint) or in the built-in Secure Reader app, which provides secure, read-only access to files. Additionally, watermarks cannot be removed by the user. This makes it much less likely that users will leak sensitive data, such as company salaries or intellectual property, when their username, ID, date of access and other identifying information are displayed prominently in a document.
4. Dynamically Encrypt Sensitive Data
Regulations such as HIPAA and PCI DSS, as well as other frameworks, often require specific types of sensitive data, including personal or financial information, to be encrypted. NC Protect’s data-centric, policy-based approach enables you to automatically encrypt files based on their classification. The contents of emails and attachments sent through Exchange can also be encrypted automatically.
NC Protect’s data protection capabilities are far more flexible than just applying blanket encryption to sensitive files. While encryption provides additional security for documents, it can also generate significant overhead. Many organizations want to take the extra step of encrypting sensitive documents, but don’t want to deal with the hassle of encrypting all of their documents when they don’t need to. With NC Protect, apply encryption only when truly needed, not as a catchall for protecting sensitive data.
Encryption can be applied using Microsoft Purview Information Protection or the optional NC Encrypt module. The NC Encrypt module provides “Hold Your Own Key” (HYOK) and “Bring Your Own Key” (BYOK) capabilities, enabling seamless management of data security and compliance. By using policy-based encryption, you can easily meet your compliance obligations.
5. Report on Sensitive Data Access
NC Protect’s auditing capabilities report on who has access to sensitive data and what actions they have taken with it. This allows you to provide detailed information to auditors, if necessary, as well as verify that the policies are working as intended. You can easily analyze user activity logs collected in NC Protect with Microsoft Sentinel via a free Connector or import logs into Splunk to analyze the data at cloud scale and trigger holistic alerts and remediation actions alongside the dynamic and real-time access controls of NC Protect.
Take a Proactive Security Posture
I always say that three types of people prioritize security:
- Those forced to because of a compliance requirement.
- Those who know that just about everyone will be breached eventually.
- Those who have already been breached.
While classifying and protecting sensitive data may seem like an additional burden for many, the possibility of exposing regulated information, losing Intellectual Property, incurring significant compliance violation fines, or suffering a huge hit to your organization’s reputation and the bottom line should be a massive motivator to classify and secure data.
A large number of companies have had to provide credit check services to all users and have undergone a significant loss of trust after a data breach. Unfortunately, not all of these organizations, especially smaller ones, have been able to withstand such losses. Fortunately, most organizations have recognized that security and data protection are critical operational expenses and are continually re-evaluating their security posture.
If you have any questions about how NC Protect assists with classifying and protecting sensitive data, please don’t hesitate to contact us.