NC Protect Resources
All Resources | Kojensi Resources | NC Protect Resources

Demo: NC Protect for M365 and SharePoint
See NC Protect’s dynamic and unique data protection features to ensure secure collaboration, sharing and info barriers across M365 apps.
Webinar: POPI Act Compliance 7 Best Practices to Protect Personal Data
Amid growing risk, the need to comply with the Protection of Personal Information Act (POPIA), and the emergence of a remote and hybrid workforce, organizations must find ways to achieve a balance between enabling collaboration and securing sensitive information. You will discover the seven best practices for compliance with privacy legislation, without sacrificing collaboration.

Webinar: Stop the Top 10 Data Loss Scenarios
Since the onset of COVID-19, companies are reporting sharp increases in data loss spurred by remote and hybrid work. But, just how is all this data leaking with all the security measures enterprises have in place? View this webinar and explore our solutions to the different data loss scenarios that plague most companies.

White Paper: Building Dynamic Information Barriers in Microsoft 365
This white paper examines the challenge of building information barriers using role based security and how to create more usable separation for more complex use cases using dynamic attribute-based access control (ABAC) policies.

Data Sheet: NC Protect Data Connector for Microsoft Sentinel
Microsoft Sentinel is a cloud-native SIEM that you can use for intelligent security analytics across your entire enterprise. The NC Protect Data Connector for Microsoft Sentinel allows you to easily ingest user activity and protection logs and their associated “events” from NC Protect into Microsoft Sentinel.

Technology Brief: Meeting the US Presidential Executive Order for Zero Trust
The new U.S. Presidential Cybersecurity Executive Order for Zero Trust requires US Federal agencies to transition ...

Webinar: 5 Tips to Protect Your Sensitive Data in Nutanix Files
With remote work comes new risks and concerns about how data is accessed and used in cloud sharing apps like ...
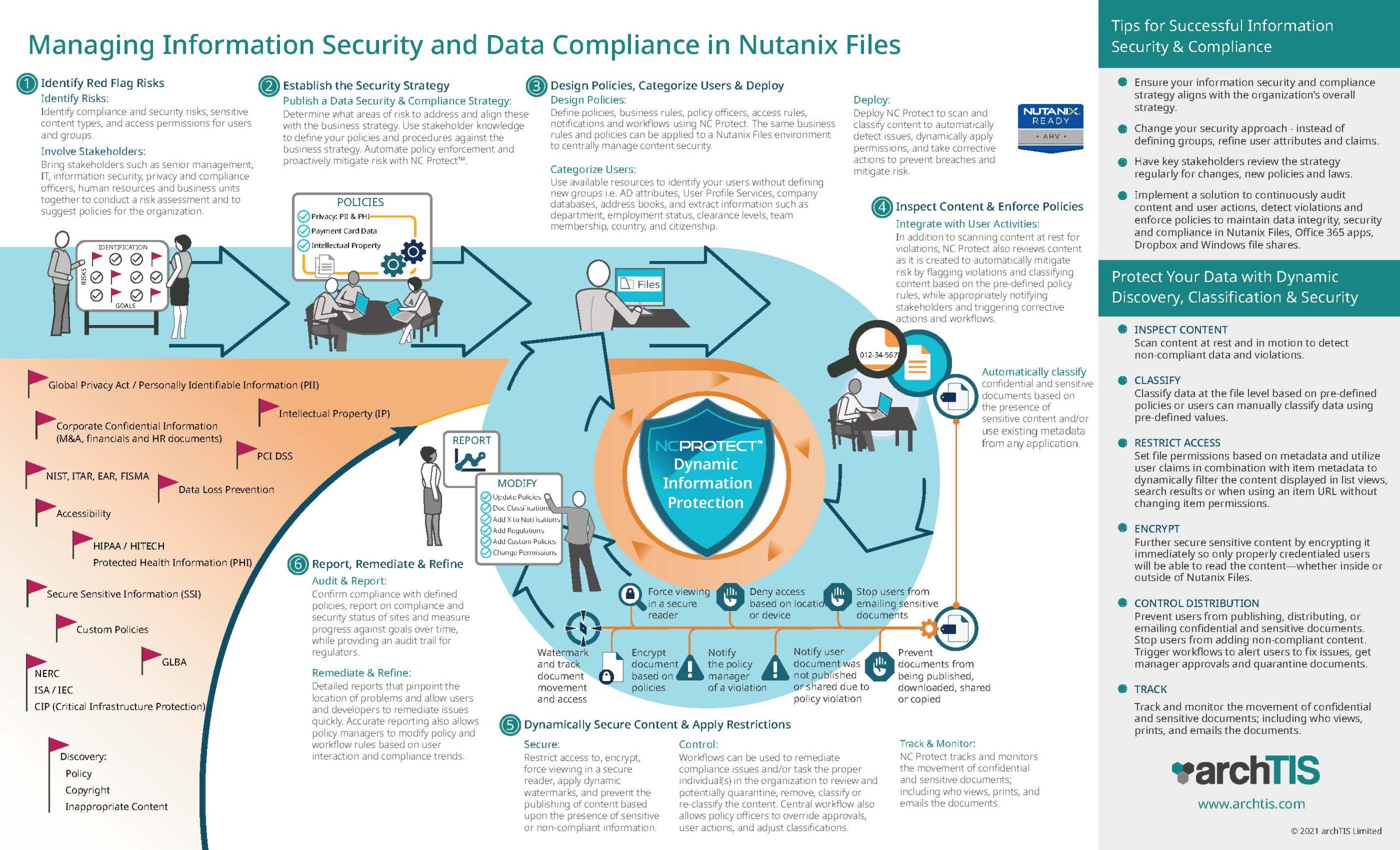
Infographic: Managing Information Security and Data Compliance in Nutanix Files
6 steps for effectively managing information security and compliance; from defining your strategy to using NC Protect to enforce compliance and apply dynamic security to data stored and shared in Nutanix Files

Webinar: Remote work is putting your data at risk. Protect it with Zero Trust.
The shift to remote work has organizations grappling with how to protect business-critical data. This Webinar ...

Webinar: Securing SharePoint Data as You Transition to the Cloud
This On-Demand webinar shares the challenges, best practices and most effective tools to migrating to a cloud ...

Data Sheet: NC Protect for Microsoft 365 & SharePoint
With modern collaboration apps, users can access data from an alarming variety of locations. Between Azure, Office 365 and other cloud platforms, businesses are adopting new technologies faster than ever and data loss prevention methodology needs to keep up.

Data Sheet: NC Protect and Microsoft Purview Information Protection (MIP) Integration
NC Protect leverages key Microsoft Purview Information Protection (MPIP) extensibility capabilities to provide fine-grained, data-centric security for collaboration in Microsoft 365 applications. By combining MPIP sensitivity labels with NC Protect’s dynamic attribute-based access control (ABAC) and protection policies customers will benefit from expanded protection and control over information access, collaboration and sharing. Learn more about the integration.

Data Sheet: NC Protect for File Shares
The numbers tell the story, 90 percent of data generated today is unstructured (customer purchase history, call center logs, email, spreadsheets, documents, web content, blogs, wikis, etc.). And information velocity is not slowing down with quintillions of bytes of data being created every day.

Data Sheet: NC Protect for Nutanix
Organizations rely on file storage platforms like Nutanix Files to store and collaborate on unstructured content. And that content is growing quickly.

NC Protect Technical Specifications
The following technical requirements represent the minimum recommended configuration for installing NC Protect version 8.5. archTIS recognizes that each deployment is different and can advise on how your specific environment should be configured to ensure optimal performance.

Data Sheet: NC Protect Overview
With modern collaboration apps, users can access data from an alarming variety of locations. Between Azure, Office 365 and other cloud platforms, businesses are adopting new technologies faster than ever and data loss prevention methodology needs to keep up.

White Paper: Top 10 SharePoint Security and Compliance Risks
This whitepaper describes 10 risks that are common in SharePoint environments. These risks are ones that we at archTIS have frequently seen in dealing with hundreds of SharePoint users over the past few years, and they are risks that can have serious consequences for organisation if left unmanaged.
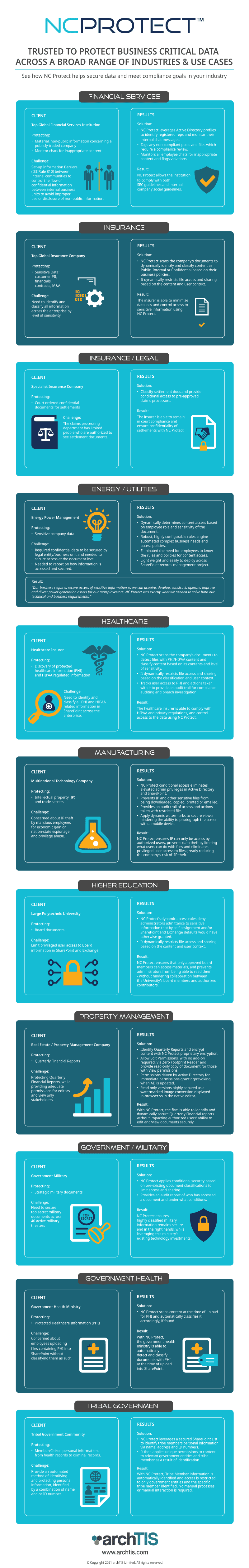
NC Protect Customer Success Stories by Industry
See how NC Protect helps customers in every industry secure data and meet compliance.
