Blog
Stay up to date on industry trends, security advice, product news and more.

Sensitive data exposure: causes, detection and mitigation
The modern world is a tech-savvy and digitally enabled in the office and outside of it. So much can be done ...

5 Best Practices for Employee Information Privacy
In this article we'll go over 5 best practices for employee information privacy incl. knowing sensitive data, applying granular encryption, training employees and others.

Introducing Data Discovery, Classification and Security for Nutanix Files
NC Protect Now Offers Integrated, AHV Ready Data Discovery, Classification and Security for Sensitive Information in Nutanix Files
5 Ways Remote Work is Putting Your Data at Risk
Get the facts about data loss and remote work in this new Infographic, and 4 simple steps your organization can take to address this trend that's been amplified by work from home.
Enhancing Microsoft Information Security with NC Protect
Discover the complementary nature of NC Protect, as well as the value and advanced information protection capabilities it provides Microsoft 365 customers.

Building a Data Classification Scheme and Matrix
A lot of the specific terms like framework, matrix or model might seem like a mystery for a lot of people, especially when it comes to these terms being applied to data classification as a process. This article describes what a data classification matrix is and what the most obvious errors are that you can do when forming a data classification scheme.

What is Sensitive Data? Sensitive Data Definitions, Types & Examples
Data security and data breaches are recurring topics in the IT world. While it’s vital to keep all data safe from exploitation, it’s even more vital to keep the so-called “sensitive data” safe from exposure. This discourse would expose you to the definition of sensitive data, what makes data sensitive, and how to protect information from exposure, and exploitation.

SharePoint File and Folder Security
There’s a number of different security levels in the SharePoint as a system. Two of the lowest ones are file security and folder security. Learn more about their differences and how you can operate with them, in this article.

11 Data Security Blogs to Add to Your Summer Reading List
Catch up on data security trends, challenges, tips and products to boost your skills and ensure you're up-to-date on how to protect collaboration with these curated reads.

Data Classification: Definition, Types and Steps to Get Started
Data classification is an important topic for any company that works with large amounts of data. Learn more about classifying data, types of data classification, examples and data classification framework.
7 Practices to Ensure Compliance with South Africa’s POPI Act
South Africa has created the POPI Act to govern data privacy. Ensure your data security practices comply.

Designing Information Barriers in Microsoft 365 for Real-world Collaboration
How to design Information Barriers in Microsoft Teams to restrict specific collaboration, but with enough flexibility to allow other types of communication.

Security Testing in SharePoint
Like almost any application that works on the web, SharePoint, in all of its’ versions, has a list of ...

Working from Home Fuels New Data Loss Stats
Get the facts about this alarming trend and the steps your organization can take to address data loss that has been amplified by working from home.

GDPR Compliance Requirements Checklist and Plan
GDPR is a legal regulation of data processing that relates to citizens of the EU. The regulation might seem overwhelming at first and that is why there are two different requirements checklists to help you inside this article. Improve your GDPR compliance plan using our pieces of advice.

Security Roles in SharePoint Architecture: SharePoint Security Matrix
Security roles in SharePoint represent different levels of permissions and responsibility, from End Users to SharePoint Farm Administrators. Learn more about each of their features and the overall SharePoint security matrix in this article.
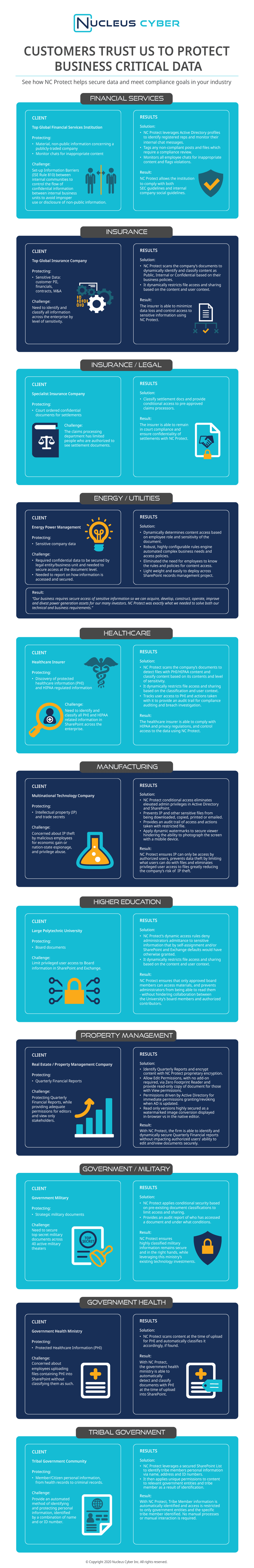
See How Your Peers Secure Business-critical Information with NC Protect
See how customers trust NC Protect to protect their business critical data in Microsoft cloud, on-premises and hybrid collaboration apps in this Infographic.

The Need for Proactive Data Security in the Age of Collaboration and WFH
Why using reactive security solutions instead of tools designed to proactively prevent insiders from misusing or oversharing information won't protect your data.
