Blog
Stay up to date on industry trends, security advice, product news and more.

A Cyber Christmas Carol: Scrooge Worthy Security Lessons for 2022
Let’s take a walk with the Security Ghosts of Past, Present and Future for some Scrooge worthy security lessons to take with us into 2022.

Notice regarding the recent Log4j vulnerability
As a matter of critical priority, archTIS has undergone technical analysis of this vulnerability and any impacts ...

Join archTIS at 365 EduCon DC and the Content Protection Summit this Week!
archTIS will be sponsoring and speaking at several events this week. See what we have instore for you if you're attending 365 EduCon DC or the CDSA Content Protection Summit in LA.

Introducing Kojensi Version 2.0 for Sensitive Information Sharing and Document Collaboration
Enhanced capabilities in Kojensi Enterprise v2.0 support secure, military grade data protection to enable secure collaboration between defence and industry.

Understanding Higher Education Cybersecurity Threats to Research and IP
The impact of Higher Education cybersecurity breaches can be mitigated with these tips to help protect research IP.
6 FinTech Cybersecurity Trends for 2022
What cybersecurity trends can we expect to see for FinTech as 2021 draws to a close and we get ready for 2022? Here’s 6 FinTech Cybersecurity Trends for 2022.
Best practices for POPIA compliance
Complexity, budget and time are among the challenges organisations wanting to achieve compliance with the Protection of Personal Information Act (POPIA) face, but they have to better protect sensitive information or face serious consequences.

Building Dynamic Information Barriers in Microsoft 365
The challenges of building information barriers with role based security and how dynamic attribute-based access control (ABAC) solves complex use cases.

4 Skeletons to Keep Locked in Your Data Closet
While every company may not have skeletons in their data closets that could discredit or embarrass them, there is a lot of data that every company needs to keep secret. Here’s some advice on how to keep these skeletons in the data closet or repository where they belong.

Join archTIS at Microsoft Ignite Nov 2-4 in our Partner Showcase
We’re excited to announce that archTIS is exhibiting at this year’s virtual event in the Partner Showcase. We will be demonstrating how our NC Protect product provides advanced data-centric security for secure collaboration in Microsoft 365 applications that is simple, fast and scalable.
Using Digital Security Watermarks to Prevent Data Loss and Aid in Forensics
Dynamic, digital security watermarks can augment your information security practices to provide a visual deterrent to prevent data loss and aid in forensics.
Meeting the Presidential Executive Order for Zero Trust
The Executive Order for Cybersecurity requires federal agencies to adopt a zero trust architecture. Why this ‘trust no one’ ethos must extend to the data.

5 Information Security Take-aways from the Facebook Whistleblower
5 information security take-aways from the Facebook Whistleblower breach to help protect your organization from insider threats.
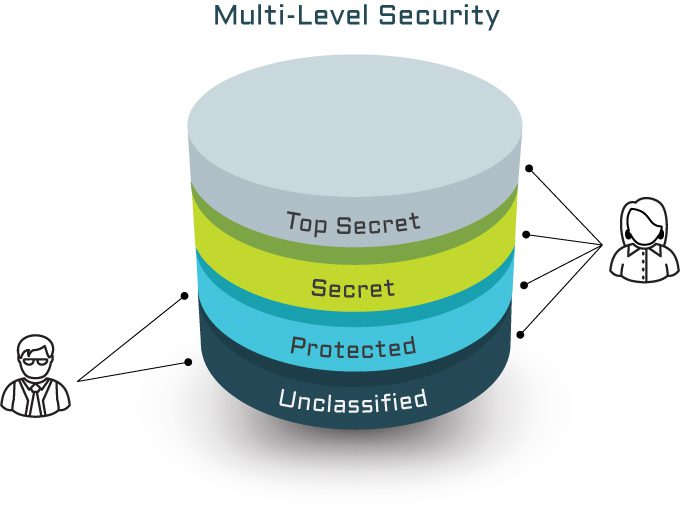
What is Multi-Level Security (MLS) and why is it important?
Implementing the right separation and information protections needed to meet defence requirements can be a challenge. Dynamic Multi-Level Security (MLS) offers a solution.

The zero trust blindspot – as seen in Top Business Tech
Zero trust architecture is undoubtedly the future of cybersecurity. However, it does not typically extend beyond network access, which is a shortcoming that will eventually come back to bite the information security community as a whole.

Join archTIS at these Upcoming Defence Events in the US and UK
We are excited to share that archTIS will be exhibiting at multiple events in the next few months. Join us to learn about protecting sensitive/classified information with increased threats and regulations aimed at Defence Industry.

archTIS Named a Finalist for Cyber Business of the Year in the Australian Defence Industry Awards 2021
archTIS is pleased to announce that the Company has been selected as a finalist in the Australian Defence Industry Awards for Cyber Business of the Year.
NC Protect Trims SharePoint Information Sharing Risks for BGW
Learn how BGW implemented a SharePoint 2019 on-premises web portal with secure, read only employee, management and industry volunteer access using NC Protect.
