Blog
Stay up to date on industry trends, security advice, product news and more.

DFARS Compliance in Microsoft 365
Understanding DFARS compliance requirements for CUI stored, collaborated on and shared in Microsoft 365 Applications.
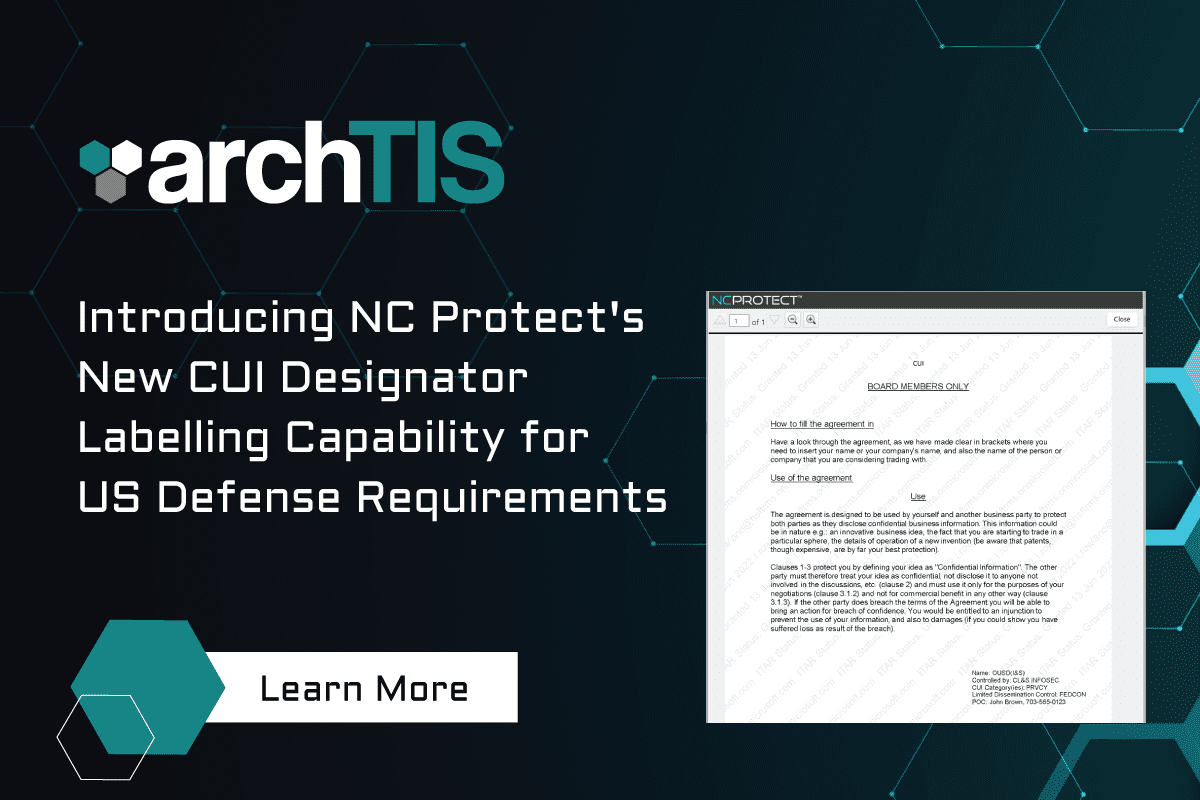
Introducing NC Protect’s New CUI Designator Labelling Capability for US Defense Requirements
We're pleased at announce a new NC Protect watermarking feature to support CUI Designator labelling capability to assist US Defense and the Defense Industrial Base (DIB) with meeting the new CUI document handling and tagging requirements.

Join archTIS at Eurosatory in Paris and Infosecurity Europe in the UK this June
archTIS will be exhibiting at several events in Europe this June; Eurosatory and Infosecurity Europe. Read on to learn more about the activities planned and what we will be showcasing at these two major European security events.
NC Protect is now available in both Microsoft Azure Marketplace and Azure Government Marketplace!
We are excited to share that NC Protect for Microsoft 365 is now available in both Microsoft Azure Marketplace and Azure Government Marketplace!

Missed last week’s Defense & DIB Cybersecurity Summit? Watch the recording
Miss last week's archTIS Defense & DIB Cybersecurity Summit with leading industry and defense experts? Watch the recording for their insights on the zero trust, #CMMC 2 and the new threats the industry is facing and how to best combat them.
Technical Spotlight: How to Protect, Encrypt and Watermark CAD Files
Today's technical spotlight covers how to protect and watermark CAD Files to help prevent data loss and IP theft, and meet Defense compliance requirements such as CMMC.

Adopting a Security vs Compliance Focused Posture
When dealing with regulations you need to consider is your ultimate goal achieving "good enough" compliance or “truly focused” security?
Join archTIS on May 5th for our Cybersecurity Summit Featuring Prominent Government and Defense Industry Thought Leaders
Join archTIS for “Balancing Global Collaboration with Information Security: Best Practices for Tackling Defense and Supply Chain Challenges” to be held on Thursday, May 5, 2022 at AUSA Conference Center, Arlington, VA, 9:00 am – 12 Noon EDT.

Australia and US Pledge More Government Cybersecurity Spend for 2022-23
In the midst of a growing global cyberthreat landscape, the Australian and US governments this week announced plans to increase spend to bolster federal cybersecurity.

15 Ways to Protect Data with Digital Security Watermarks
Learn how today’s security watermarks act as a digital thumbprint that travels with the document to prevent data loss and misuse.

Microsoft 365 and SharePoint Secure File Sharing Tips
Microsoft 365 provides a powerful document management and collaboration platform. However, ensuring proper access and data security can be a challenge. In this blog we examine how to ensure secure file sharing in Microsoft 365, SharePoint and Teams.

The women of archTIS share their experience and wisdom as Women in Tech
In honor of International Women’s Day the women of archTIS share their experience and wisdom as Women in Tech.
Role Based Access Control vs Attribute Based Access Control: Addressing Common Misconceptions
Understanding the two common approaches an organization can deploy: role-based access control (RBAC) vs attribute-based access control (ABAC) to safeguard data.

Case Study: Managing CUI Tagging and Protection in SharePoint
Discover how this Defense Manufacturer automated the management of Controlled Unclassified Information (CUI) in SharePoint to comply with numerous regulations for its safeguarding and dissemination controls.

What is Data-centric Security?
A data-centric security strategy shifts the approach from a company’s outer defences to making the data itself more secure.

MODERNIZING DATA LOSS PREVENTION CONTROLS WITH ABAC SECURITY
Discover how to implement a proactive, ABAC-powered data loss prevention (DLP) strategy to enable more secure and compliant collaboration.

What is Zero Trust Access and How to Employ It
The concept of “Zero Trust” (ZT) is quickly gaining steam as the preferred security methodology. Learn how to apply it to your data access and security processes.

The Top Insider Data Loss Causes and Preventions
Discover the top 10 ways insiders are contributing to data loss in your organization and how to prevent data loss and mishandling in the first place.
